Valid 70-685 Dumps shared by PassLeader for Helping Passing 70-685 Exam! PassLeader now offer the newest 70-685 VCE dumps and 70-685 PDF dumps, the PassLeader 70-685 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader 70-685 dumps with VCE and PDF here: http://www.passleader.com/70-685.html (196 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader 70-685 dumps from Cloud Storage: https://drive.google.com/open?id=0B-ob6L_QjGLpfk40ZWRBaERtMW04RHdwYTZ5bkVaRnpyV2hHeXU5bUpNYTU1aUtpaEo3TUk
QUESTION 49
The company purchases 500 USB flash drives from a new hardware vendor and distributes them to the users. The help desk reports that the users are unable to access the new USB flash drives. You need to ensure that users can save data on the USB flash drives. What should you do?
A. Instruct the help desk to modify the BitLocker settings.
B. Instruct the help desk to modify the Windows Defender settings.
C. Request that an administrator modify the driver signing policy.
D. Request that an administrator modify the device installation restriction policy.
Answer: D
Case Study 2 – City Power & Light (QUESTION 50 – QUESTION 54)
Scenario
You are an enterprise desktop support technician for City Power & Light. City Power & Light is a utility company. The company has a main office and a branch office. The main office is located in Toronto. The branch office is located in Boston. The main office has 1,000 employees. The branch office has 10 employees.
Active Directory Configuration
The network contains a single Active Directory domain named cpandl.com. The functional level of the forest is Windows Server 2008 R2.
Server Configuration
All servers run Windows Server 2008 R2. The relevant servers in the main office are configured as shown in the following table:
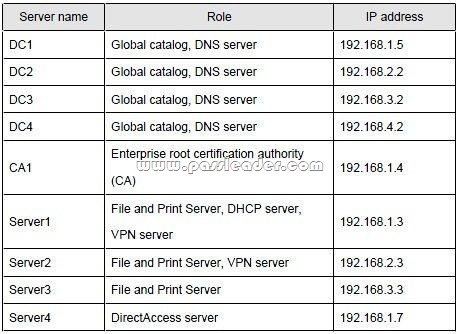
All computers in the main office are configured to use DHCP. All computers in the branch office are configured to use static IP addresses.
User Information
– All user accounts are standard user accounts.
– All client computers run Windows 7 Enterprise.
– Each portable computer has a PPT P-based VPN connection to the internal network.
Corporate Security Guidelines
– All users must be granted the least privileges possible.
– All locally stored documents must be encrypted by using Encrypting File System (EFS).
– The hard disk drives on all port able computers must be encrypted by using Windows BitLocker Drive Encryption (BitLocker).
– All encryption certificates must be stored on smart cards.
The company is deploying a new application. When users attempt to install the application, they receive an error message indicating that they need administrative privileges to install it.
QUESTION 50
You need to recommend a solution to ensure that users can install the application. The solution must adhere to the corporate security guidelines. What should you recommend?
A. Publish the application by using a Group Policy.
B. Disable User Account Control (UAC) by using a Group Policy.
C. Add all domain users to the local Power Users group by using Restricted Groups.
D. Add the current users to the local Administrators group by using Group Policy preferences.
Answer: A
Explanation:
http://magalan.co.uk/install_software_via_group_policy.html
QUESTION 51
Several mobile users access the Internet by using cellular connections. The help desk reports a high volume of calls from mobile users who report the following connection problems:
– When their cellular connections fail, their VPN connections also fail.
– When their cellular connections are reestablished, they must manually connect to the VPN server.
You need to recommend a solution to ensure that the VPN connections are automatically reestablished. What should you recommend?
A. Implement an IKEv2 VPN.
B. Implement an SSTP-based VPN.
C. Configure credential roaming.
D. Configure a Kerberos user ticket lifetime.
Answer: A
Explanation:
Internet Key Exchange version 2 (IKEv2) support was added in Windows Server 2008 R2 and Windows 7 to accommodate a new VPN type that supports VPN Reconnect. VPN Reconnect refers to the ability of a VPN connection to survive short interruptions in network connectivity, such as when you move from one wireless access point to another, or when you switch from a wired to a wireless network adapter. By taking advantage of features in IKEv2, even changes in IP address at the client do not drop the VPN connection or require any user actions. As soon as connectivity to the RRAS VPN server is restored, then the VPN tunnel is automatically reestablished.
QUESTION 52
The company implements a data recovery agent (DRA) for Bitlocker. A portable computer fails. The help desk reports that it is unable to use the DRA to recover the data from the computer’s hard disk drive. You need to ensure that the DRA can be used to recover data from the hard disk drives of all portable computers. Which tool should you use?
A. CertUtil.exe
B. Cipher.exe
C. Manage-bde.exe
D. SDelete.exe
Answer: C
Explanation:
http://technet.microsoft.com/en-us/library/dd875513(WS.10).aspx
QUESTION 53
Five users from the main office travel to the branch office. The users bring their portable computers. The help desk reports that the users are unable to access any network resources from the branch office. Branch office users can access the network resources. You need to ensure that the main office users can access all network resources by using their portable computers in the branch office. The solution must adhere to the corporate security guidelines. What should you instruct the help desk to do on the portable computers?
A. Create a new VPN connection.
B. Add the users to the local Administrators group.
C. Add the users to the Network Configuration Operators group.
D. Configure the alternate configuration for the local area connection.
QUESTION 54
Users report that their DirectAccess connections fail. You instruct the help desk to tell the users to run the Connection to a Workplace Using DirectAccess troubleshooter. The help desk reports that the Connection to a Workplace Using DirectAccess troubleshooter fails to function. You need to ensure that the Connection to a Workplace Using DirectAccess troubleshooter functions properly. What should you do?
A. Instruct the help desk to enable IPv6 on the users’ computers.
B. Instruct the help desk to modify the users’ Windows Firewall settings.
C. Request that the domain administrator configure the Teredo State Group Policy setting.
D. Request that the domain administrator configure the Corporate Website Probe URL Group Policy setting.
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/ee624046(WS.10).aspx
Case Study 3 – A.Datum Corporation (QUESTION 55 – QUESTION 59)
Scenario
You are an enterprise desktop support technician for A.Datum Corporation.
Active Directory Configuration
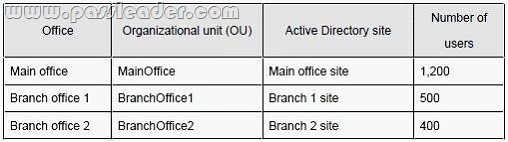
The company has three offices. The offices are configured as shown in the following table:
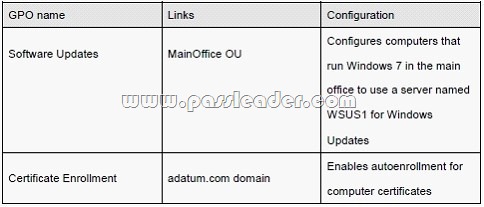
The network contains a single Active Directory domain named adatum.com. Two Group Policy objects (GPOs) are configured as shown in the following table:
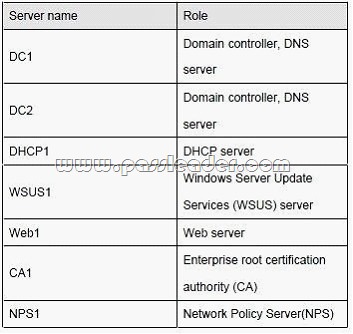
The relevant servers in the main office are configured as shown in the following table:
Wireless Network
A wireless network is implemented in the main office. The wireless network is configured to use WPA2-Enterprise security.
Client Configuration
All client computers run Windows 7 Enterprise and are configured to use DHCP. Windows Firewall is disabled on all client computers. All computers in the research department have Windows XP Mode and Windows Virtual PC installed. You deploy a custom Windows XP Mode image to the research department computers. An application named App1 is installed in the image. Each research department computer has the following hardware:
– 4GB of RAM
– Intel Core i7 processor
– 500GB hard disk drive
Corporate Security Policy
The corporate security policy includes the following requirements:
– Users without domain accounts must be denied access to internal servers.
– All connections to the company’s wireless access points must be encrypted.
– Only employees can be configured to have user accounts in the Active Directory domain.
– The hard disk drives on all portable computers must be encrypted by using Windows BitLocker Drive Encryption (BitLocker).
QUESTION 55
Users in the research department report that they cannot run App1 or Windows XP Mode. You need to ensure that all research department users can run App1. You need to achieve this goal by using the minimum amount of administrative effort. What should you do?
A. Approve all Windows 7 updates on WSUS1.
B. Enable hardware virtualization on the research department computers.
C. Give each member of the research department a computer that has an Intel Core i5 processor.
D. Request that a domain administrator create a GPO that configures the Windows Remote Management (WinRM) settings.
Answer: B
Explanation:
Using Windows XP Mode, you can run programs that were designed for Windows XP on computers running: Windows 7 Professional, Enterprise, or Ultimate editions. Requirements:
– Download and install Windows Virtual PC
– Download and install Windows XP Mode
– CPU with Intel-VT or AMD-V technology enabled in the BIOS – hardware virtualization
QUESTION 56
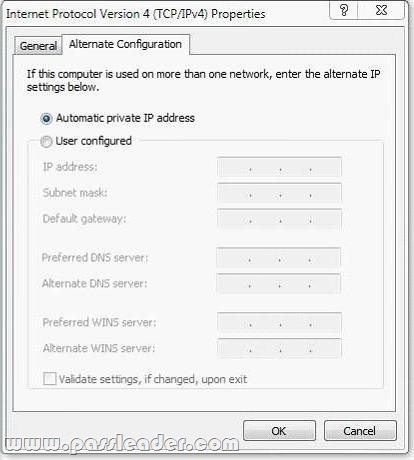
Users in branch office 1 report that they fail to access the company’s intranet Web site located on Web1. They also fail to access Web sites on the Internet. A desktop support technician restarts a desktop computer in branch office 1 and discovers the IP configuration shown in the following screenshot:
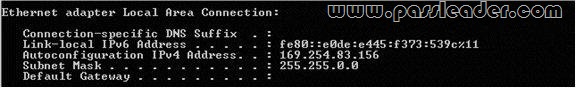
You need to resolve the network connectivity issue. What are two possible ways to achieve this goal? (Each correct answer presents a complete solution. Choose two.)
A. Instruct branch office 1 users to disable IPv6.
B. Instruct branch office 1 users to run ipconfig /renew.
C. Request that a network administrator configure the DHCP router option for branch office 1.
D. Request that a network administrator verify DHCP broadcasts are being relayed to the main office.
Answer: BD
QUESTION 57
Datum hires several consultants to work at the main office for six months. The consultants require Internet access. The help desk reports that the consultants cannot access the company’s wireless network. You need to ensure that the consultants have wireless access to the Internet. The solution must adhere to the corporate security policy. What should you request?
A. that a wireless access key be given to each consultant
B. that a user certificate be generated and imported to each consultant’s computer
C. that a computer certificate be generated and imported to each consultant’s computer
D. that a network administrator install a wireless access point that is connected directly to the Internet
Answer: D
Explanation:
Because of the “users without domain accounts” policy.
QUESTION 58
The motherboard on a portable computer fails. The data on the computer’s hard disk drive cannot be recovered. You need to recommend a solution to ensure that the data on hard disks can be recovered if the motherboard on other portable computers fail. Which two configurations should you recommend? (Each correct answer presents part of the solution. Choose two.)
A. Disable BitLocker on all portable computers.
B. Convert the hard disks on all portable computers to dynamic disks.
C. Export and securely store the computer certificates on all portable computers.
D. Configure the BitLocker settings on all portable computers by using Group Policy.
Answer: AD
QUESTION 59
The help desk reports that several client computers in branch office 1 are missing security updates. You need to identify which security updates are missing. What should you request?
A. that a WSUS administrator generate a Computer Report from WSUS1
B. that a domain administrator run the Microsoft Baseline Security Analyzer (MBSA)
C. that a desktop support technician run a Windows Defender scan on each computer
D. that a desktop support technician generate a System Configuration report for each computer
Answer: B
Explanation:
Microsoft Baseline Security Analyzer (MBSA): to detect common security miss-configurations and missing security updates on your computer systems.
Case Study 4 – Margie’s Travel (QUESTION 60 – QUESTION 64)
Scenario
You are an enterprise desktop support technician for Margie’s Travel. Margie’s Travel is a company that specializes in booking travel for large corporations. The company has a main office in New York and operates a call center in New York and a call center in Los Angeles. The company has 1,000 employees.
Active Directory Configuration
The network contains an Active Directory forest named margiestravel.com. The functional level of the forest is Windows Server 2008 R2. The Active Directory sites are configured as shown in the following table:
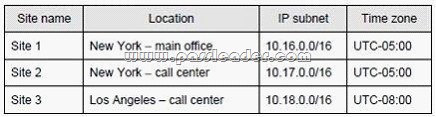
All sites connect to each other by using high-speed WAN links.
Server Configuration
The relevant servers are configured as shown in the following table:
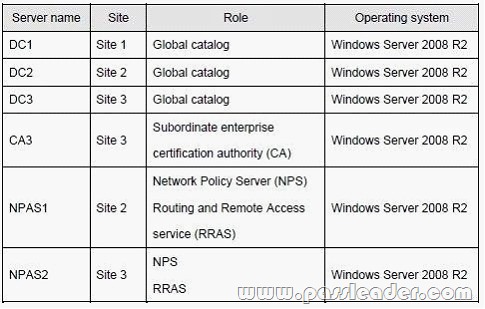
Security Configuration
The relevant security settings for the domain are configured as shown in the following table:
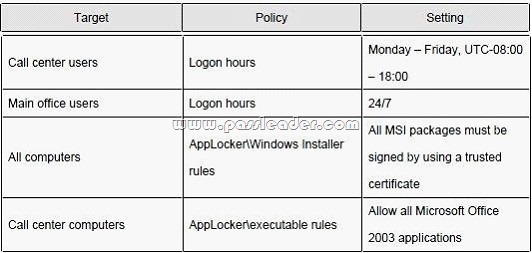
The relevant network policies on the NPS servers and the RRAS servers are configured as shown in the following table:
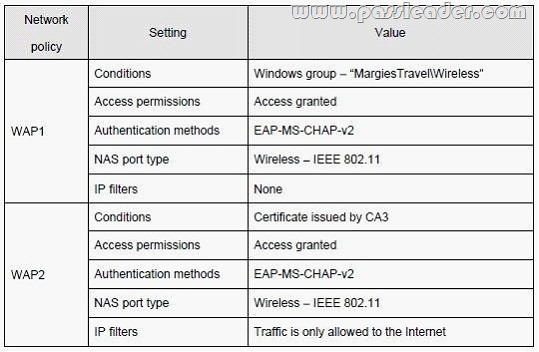
User Information
All client computers run Windows 7 Professional. Sales staff is located in the main office and uses portable computers. All portable computers are members of the MargiesTravel\Wireless group.
Application Configuration
Call center staff uses a custom application to book airline tickets. The application is packaged as an MSI file and is signed by using a code signing certificate that was issued by CA3. The application is published by using Group Policies.
QUESTION 60
The company hires an additional 100 users. The users are unable to install the custom application. You need to ensure that the users can install the custom application. What should you do?
A. Disable User Account Control (UAC).
B. Add the users to the local Administrators group.
C. Request that the application package be re-signed.
D. Request that the user certificates be issued to the new users.
Answer: A
QUESTION 61
You deploy Microsoft Office 2007 to a pilot group in the main office. Users in the pilot group report that all of the Office 2007 applications run successfully. You deploy Office 2007 to users in the New York call center. The call center users report that they are unable to launch the Office 2007 applications. You need to ensure that the call center users can run all of the Office 2007 applications. What should you do?
A. Modify the AppLocker rule.
B. Disable User Account Control (UAC).
C. Deploy the 2007 Office system Administrative Template files.
D. Configure the Office 2007 applications to run in Windows Vista compatibility mode.
Answer: A
QUESTION 62
At 08:00 on a Tuesday morning, an administrator in Site 3 takes DC3 offline to update the server. Users in Site 3 report that they cannot log on to their computers. The users receive the following error message:
“Your account has time restrictions that prevent you from logging on at this time. Please try again later.”
You need to ensure that all users can log on to their computers when DC3 is offline for maintenance. Your solution must adhere to the corporate security policies. What should you do?
A. Modify the logon hours for all users in Site 3.
B. Change the time zone settings for all client computers in Site 3 to UTC-05:00.
C. Request that a second domain controller be deployed in Site 3.
D. Request that the time zone settings for DC1 and DC2 be changed to UTC-08:00.
Answer: C
QUESTION 63
You have two external consultants. The consultants use their own personal portable computers. The consultants report that they are unable to connect to your wireless network. You need to give the consultants wireless access to the Internet. The solution must prevent external consultants from accessing internal resources. What should you do?
A. Issue a user certificate to the consultants.
B. Issue a computer certificate to the consultants.
C. Join both portable computers to the domain.
Add the computer accounts to the MargiesTravel\Wireless group.
D. Create a domain user account for each consultant.
Add the user accounts to the MargiesTravel\Wireless group.
Answer: B
QUESTION 64
Users access a third-party Web site. The Web site is updated to use Microsoft Silverlight. After the update, the help desk receives a high volume of phone calls from users who report that the Web site fails to function. You need to ensure that the Web site functions properly for the users. What should you do?
A. Modify the Windows Internet Explorer AJAX settings by using a Group Policy object (GPO).
B. Modify the Windows Internet Explorer add-ons settings by using a Group Policy object(GPO).
C. Add the Web site to the Windows Internet Explorer Compatibility View list by using a Group Policy object (GPO).
D. Add the Web site to the Windows Internet Explorer Restricted sites by using a Group Policy object (GPO).
Answer: B
Get the newest PassLeader 70-685 VCE dumps here: http://www.passleader.com/70-685.html (196 Q&As Dumps)
And, DOWNLOAD the newest PassLeader 70-685 PDF dumps from Cloud Storage for free: https://drive.google.com/open?id=0B-ob6L_QjGLpfk40ZWRBaERtMW04RHdwYTZ5bkVaRnpyV2hHeXU5bUpNYTU1aUtpaEo3TUk