Valid 70-410 Dumps shared by PassLeader for Helping Passing 70-410 Exam! PassLeader now offer the newest 70-410 VCE dumps and 70-410 PDF dumps, the PassLeader 70-410 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader 70-410 dumps with VCE and PDF here: http://www.passleader.com/70-410.html (512 Q&As Dumps –> 528 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader 70-410 dumps from Cloud Storage: https://drive.google.com/open?id=0B-ob6L_QjGLpfnJzOE1fWnlJOWVtaE93SnJNT3gtaTNYYnVpZkw5THBSMWRKbFlfaXh1azg
QUESTION 1
How can you manage an newly installed Windows Server 2012 R2 core from a another Windows Server 2012 R2 with computer manager?

QUESTION 2
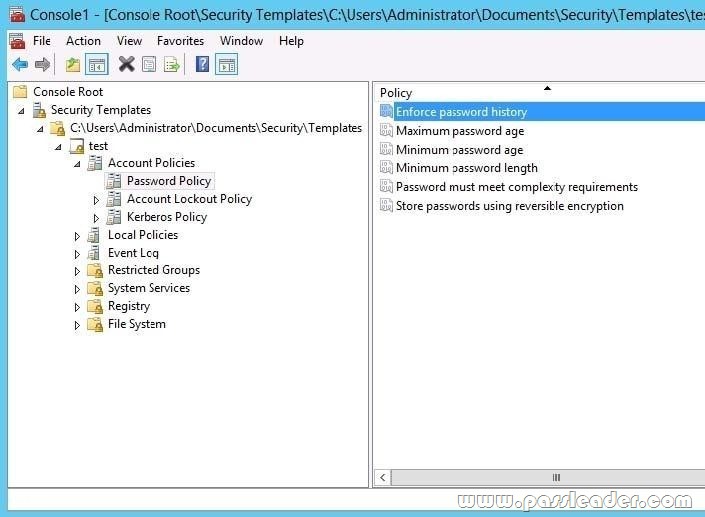
Your network contain an active directory domain named Contoso.com. The domain contains two servers named server1 and server2 that run Windows Server 2012 R2. You create a security template named template1 by using the security template snap-in. You need to apply template1 to server2. Which tool should you use?
A. Security Templates
B. Computer Management
C. Security Configuration and Analysis
D. System Configuration
Answer: C
Explanation:
A. Template was already created – Provide standard security option to use in security policies
B. Needs to be applied at the GP level
C. Security templates are inactive until imported into a Group Policy Object or the SecurityConfiguration and Analysis
D. Tool to ID windows problems
http://technet.microsoft.com/en-us/library/jj730960.aspx
http://windows.microsoft.com/en-us/windows-vista/using-system-configuration
QUESTION 3
Your network contains an active directory domain named Contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. You create a group Managed Service Account named gservice1. You need to configure a service named service1 to run as the gservice1 account. How should you configure service1?
A. From Services Console configure the recovery settings
B. From a command prompt, run sc.exe and specify the config parameter
C. From Windows PowerShell, run Set-Service and specify the -PassThrough parameter
D. From a command prompt, run sc.exe and specify the sdset parameter
Answer: B
Explanation:
SC config, Modifies the value of a service’s entries in the registry and in the Service Control Manager database.
obj= {<AccountName> | <ObjectName>}
Specifies a name of an account in which a service will run, or specifies a name of the Windows driver object in which the driver will run. The default setting is LocalSystem.
password= <Password>
Specifies a password. This is required if an account other than the LocalSystem account is used.
QUESTION 4
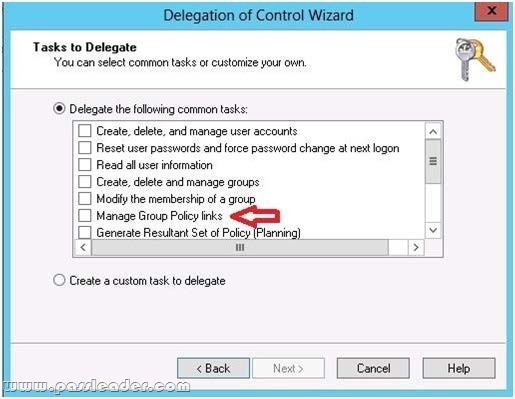
Your network contains an active directory domain named Contoso.com. The domain contains 100 user accounts that reside in an organizational unit (OU) named OU1. You need to ensure that user named user1 can link and unlink Group Policy Objects(GPOs) to OU1. The solution must minimize the number of permissions assigned to user1. What should you do?
A. Run the Delegation of Control Wizard on the Policies containers
B. Run the Set-GPPermission cmdlet
C. Run the Delegation of Control Wizard on OU1
D. Modify the permission on the user1 account
Answer: C
Explanation:
A. Not minimum permissions.
B. Grants a level of permissions to a security principal for one GPO or all the GPOs in a domain.
C. Minimizes delegated permission to a single OU.
D. Will not allow GPO changes to the OU.
Delegation of Control Wizard
The following are common tasks that you can select to delegate control of them:
– Create, delete, and manage user accounts
– Reset user passwords and force password change at next logon Read all user information
– Modify the membership of a group
– Join a computer to a domain
– Manage Group Policy links
– Generate Resultant Set of Policy (Planning)
– Generate Resultant Set of Policy (Logging)
– Create, delete, and manage inetOrgPerson accounts
– Reset inetOrgPerson passwords and force password change at next logon Read all inetOrgPerson information
http://technet.microsoft.com/en-us/library/dd145442.aspx
http://technet.microsoft.com/en-us/library/ee461038.aspx
http://technet.microsoft.com/en-us/library/cc732524.aspx
QUESTION 5
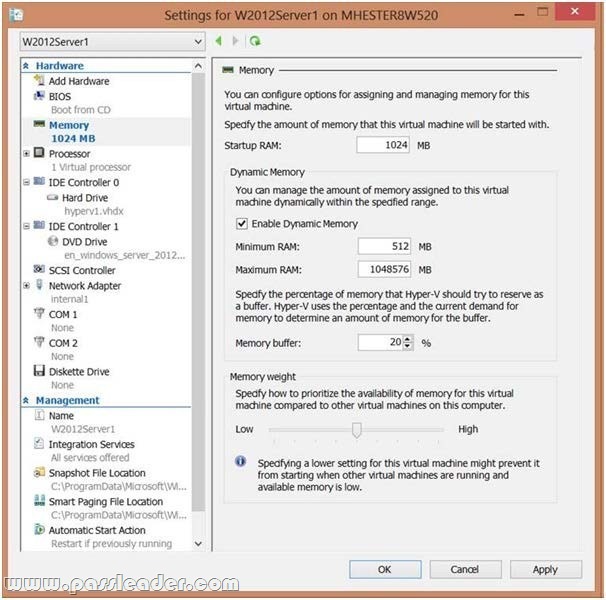
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has 2 dual-core processors and 16 GB of RAM. You install the Hyper-V server role in Server1. You plan to create two virtual machines on Server1. You need to ensure that both virtual machines can use up to 8 GB of memory. The solution must ensure that both virtual machines can be started simultaneously. What should you configure on each virtual machine?
A. Dynamic Memory
B. NUMA topology
C. Memory weight
D. Ressource Control
Answer: A
Explanation:
A. Dynamic Memory adjusts the amount of memory available to a virtual machine, based on changes in memory demand and values that you specify.
B. Used for high performance apps like SQL.
C. Provides Hyper-V with a way to determine how to distribute memory among virtual machines if there is not enough physical memory available in the computer to give every virtual machine its requested amount of memory.
D. Resource controls provide you with several ways to control the way that Hyper-V allocates resources to virtual machine.
http://technet.microsoft.com/en-us/library/ff817651(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/hh831410.aspx
http://technet.microsoft.com/en-us/library/cc742470.aspx
QUESTION 6
You have a server named Server1 that runs Windows Server 2012 R2. You promote Server1 to domain controller. You need to view the service location (SVR) records that Server1 registers on DNS. What should you do on Server1?
A. Open the Srv.sys file
B. Open the Netlogon.dns file
C. Run ipconfig/displaydns
D. Run Get-DnsServerDiagnostics
Answer: B
Explanation:
A. Timestamp server driver.
B. Netlogon service creates a log file that contains all the locator resource records stored in netlogon.
C. Used to display current resolver cache content.
D. Gets DNS event logging details.

http://technet.microsoft.com/en-us/library/cc959303.aspx
http://technet.microsoft.com/en-us/library/jj649883(v=wps.620).aspx
QUESTION 7
Your network contains an active directory domain named Contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2 and has the Hyper-V server role installed. You have a virtual machine named VM1. VM1 has a snapshot. You need to modify the Snapshot File Location of VM1. What should you do first?
A. Copy the snapshot file
B. Pause VM1
C. Shut down VM1
D. Delete the snapshot
Answer: D
Explanation:
How are snapshots stored?
Snapshot data files are stored as .avhd files. Taking multiple snapshots can quickly consume storage space. In the first release version of Hyper-V (KB950050) and in Hyper-V in Windows Server 2008 Service Pack 2, snapshot, snapshot data files usually are located in the same folder as the virtual machine by default. In Hyper-V in Windows Server 2008 R2, the files usually are located in the same folder as the virtual hard disk. The following exceptions affect the location of the snapshot data files: If the virtual machine was imported with snapshots, they are stored in their own folder. If the virtual machine has no snapshots and you configure the virtual machine snapshot setting, all snapshots you takeafterwards will be stored in the folder you specify.
Caution:
Do not delete .avhd files directly from the storage location. Instead, use Hyper-V Manager to select the virtual machine, and then delete the snapshots from the snapshot tree. Do not expand a virtual hard disk when it is used in a virtual machine that has snapshots. Doing so will make the snapshots unusable.
http://technet.microsoft.com/en-us/library/dd560637(v=ws.10).aspx
QUESTION 8
Hotspot Question
You have a server named Server1 that runs Windows Server 2012 R2. Several users are members of the local Administrators group. You need to ensure that all local administrators receive User Account Control (UAC) prompts when they run a Microsoft Management Console (MMC). Which setting should you modify from the Local Security Policy? To answer, select the appropriate settings in the answer area.

QUESTION 9
You have a network printer connected to print server. You need to be able to print if print server goes down. What should you chose?
A. brach office direct printing
B. printer pooling
C. spooling
D. Print forwarding
Answer: A
Explanation:
Branch Office Direct Printing can reduce Wide Area Network (WAN) usage by printing directly to a print device instead of a server print queue. This feature can be enabled or disabled on a per printer basis and is transparent to the user. It is enabled by an administrator using the Print Management Console or Windows PowerShell on the server. The printer information is cached in the branch office, so that if the print server is unavailable for some reason (for example if the WAN link to the data center is down), then it is still possible for the user to print. Branch Office Direct Printing requires the following operating systems:
– Windows Server 2012
– Windows 8
http://technet.microsoft.com/en-us/library/jj134156.aspx
QUESTION 10
You have external virtual switch with srv-io enabled with 10 Virtual Machines on it. You need to make the Virtual Machines able to talk only to each other. What should you do?
A. remove the vswitch and recreate it as private
B. add new vswitch
C. remove vswitch and recreate it as public
D. adjust srv-io settings
Answer: A
Explanation:
There are three possible modes for the Hyper-V switch: private, internal, and public. Do not confuse these with IP addressing schemes or any other networking configuration in a different technology.
Private Switch
The private switch allows communications among the virtual machines on the host and nothing else. Even the management operating system is not allowed to participate. This switch is purely logical and does not use any physical adapter in any way. “Private” in this sense is not related to private IP addressing. You can mentally think of this as a switch that has no ability to uplink to other switches.
Internal Switch
The internal switch is similar to the private switch with one exception: the management operating system can have a virtual adapter on this type of switch and communicate with any virtual machines that also have virtual adapters on the switch. This switch also does not have any matching to a physical adapter and therefore also cannot uplink to another switch.
External Switch
This switch type must be connected to a physical adapter. It allows communications between the physical network and the management operating system and virtual machines. Do not confuse this switch type with public IP addressing schemes or let its name suggest that it needs to be connected to a public-facing connection. You can use the same private IP address range for the adapters on an external virtual switch that you’re using on the physical network it’s attached to.
http://www.altaro.com/hyper-v/the-hyper-v-virtual-switch-explained-part-1/#ixzz2W095PeZd
http://technet.microsoft.com/en-us/library/hh831823.aspx
http://www.altaro.com/hyper-v/hyper-v-virtual-switch-explained-part-2/
QUESTION 11
Hotspot Question
Your network contains an Active Directory domain named corp.contoso.com. The domain contains a domain controller named DC1. When you run ping dcl.corp.contoso.com, you receive the result as shown in the exhibit. (Click the Exhibit button.)
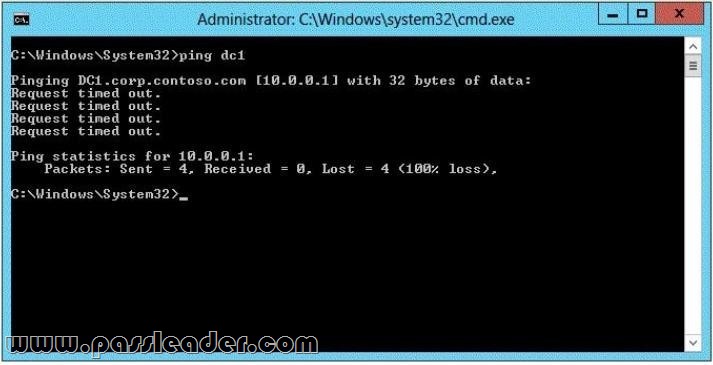
You need to ensure that DC1 can respond to the Ping command. Which rule should you modify? To answer, select the appropriate rule in the answer area.
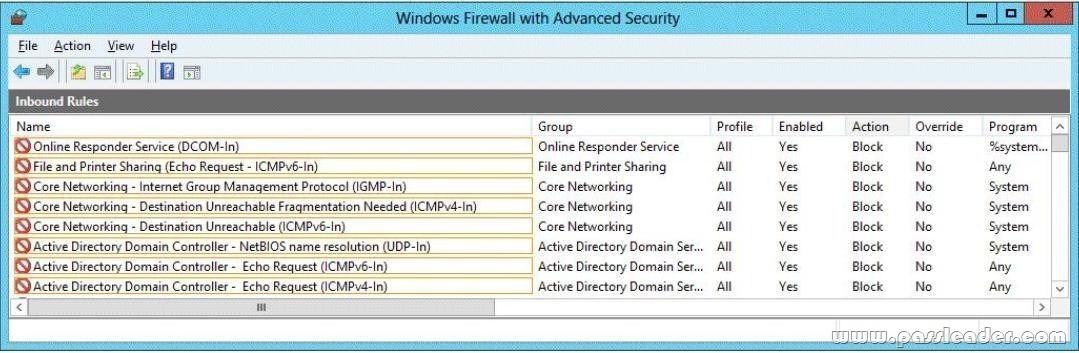
QUESTION 12
Your network contains an Active Directory domain named contoso.com. The domain contains two domain controllers. The domain controllers are configured as shown in the following table.

You install a new server named Server 1 that runs a Server Core Instillation of Windows Server 2012 R2. You need to join Server 1 to the contoso.com domain. The solution must minimize administrative effort. What should you use?
A. The dsadd.exe command
B. The New-ADComputer cmdlet
C. The Djoin.exe command
D. The Add-Computer cmdlet
Answer: D
Explanation:
A. Adds specific types of objects to the directory.
B. Creates a new Active Directory computer.
C. Use djoin for offline join in the perimeter network.
D. Add the local computer to a domain or workgroup.
http://technet.microsoft.com/en-us/library/ee617245.aspx
http://technet.microsoft.com/en-us/library/ff793312(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/cc753708(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/hh849798.aspx
QUESTION 13
Drag and Drop Question
You have a print server named Server1. Server1 runs Windows Server 2008 R2. You have a file server named Server2. Server2 runs Windows Server 2012 R2. You need to migrate all of the printers on Server1 to Server2. Which actions should you perform on the two Servers?

Answer:

Explanation:
printbrm -p all:org – Publishes all printers in the directory, or publishes printers that were published originally. While the original server is still running, use the Printer Migration Wizard or the Printbrm.exe command-line tool to export or back up the print information (such as settings, queues, and drivers) in a printer settings file. Then, import or restore this backup image to a destination server running Windows Server 2012 that has been configured to run as a print server.
http://technet.microsoft.com/en-us/library/jj134150.aspx
QUESTION 14
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1. Server1 runs Windows Server 2012 and is configured as the only domain controller. You need to retrieve a list of all the user accounts. The list must include the last time each user was authenticated successfully. Which Windows PowerShell command should you run? (To answer, drag the appropriate cmdlet or property to the correct locations to complete the PowerShell command in the answer area. Each cmdlet or property may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)

Answer:

Explanation:
To produce a listing of all the users and their last logon date, you can use the following command:
Get-ADUser -Filter * -Properties “LastLogonDate” | sort-object -property lastlogondate -descending | Format-Table -property name, lastlogondate -AutoSize
http://blogs.technet.com/b/heyscriptingguy/archive/2010/07/20/hey-scripting-guy-how-can-i-use-windows-powershell-to-identify-inactive-user-accounts-in-active-directory-domain-services.aspx
http://technet.microsoft.com/en-us/library/ee617192.aspx
http://technet.microsoft.com/en-us/library/cc732952(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/cc732979.aspx
QUESTION 15
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 contains a single virtual machine named VM1. You need to ensure that a user named User1 can manage the virtual machine settings of VM1. The solution must minimize the number of permissions assigned to User1. To which group should you add User1?
A. Server Operators
B. Administrators
C. Power Users
D. Hyper-V Administrators
Answer: D
Explanation:
This group can reduce the number of users that belong to the local Administrators group while providing users with access to Hyper-V Simplified authorization. The Hyper-V Administrators group is introduced and is implemented as a local security group.
What value does this change add?
This group can reduce the number of users that belong to the local Administrators group while providingusers with access to Hyper-V.
What works differently?
The Hyper-V Administrators group is a new local security group. Add users to this group instead of thelocal Administrators group to provide them with access to Hyper-V. Members of the Hyper-V Administrators have complete and unrestricted access to all features of Hyper-V.
http://technet.microsoft.com/en-us/library/hh831410.aspx
QUESTION 16
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Windows Server 2012 R2. You create a group Managed Service Account named gservice1. You need to configure a service named Service1 to run as the gservice1 account. How should you configure Service1?
A. From the Services console, configure the General settings.
B. From Windows PowerShell, run Set-Service and specify the -StartupType parameter.
C. From a command prompt, run sc.exe and specify the config parameter.
D. From a command prompt, run sc.exe and specify the privs parameter.
Answer: C
Explanation:
A. General settings only allow you to stop, start and set type/paramaters.
B. Set-Service provides a way for you to change the Description, StartupType, or DisplayName of a service.
C. Modifies service configuration.
D. Sets the response/action on service failure.
http://windows.microsoft.com/en-us/windows-vista/using-system-configuration
http://technet.microsoft.com/en-us/library/ee176963.aspx
http://technet.microsoft.com/en-us/library/cc990290(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/cc738230(v=ws.10).aspx
QUESTION 17
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012 R2. A user named User1 attempts to log on to DO, but receives the error message shown in the exhibit. (Click the Exhibit button.)
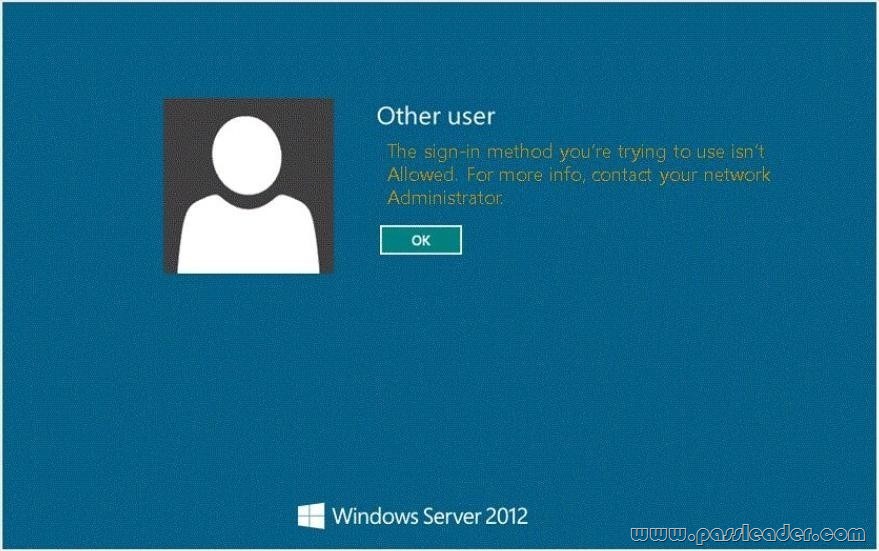
You need to ensure that User1 can log on to DC1. What should you do?
A. Modify the Account is sensitive and cannot be delegated setting of the User1 account.
B. Grant User1 the Allow log on locally user right.
C. Modify the Logon Workstations setting of the User1 account.
D. Add User1 to the Remote Management Users group.
Answer: B
Explanation:
Domain controllers, by default, restrict the types of user accounts that have the ability to log on locally. By default, only members of the Account Operators, Administrators, Backup Operators, Print Operators, andServer Operators groups have the Allowed logon locally system right. If you want to grant a user account theability to log on locally to a domain controller, you must either make that user a member of a group that alreadyhas the Allowed logon locally system right or grant the right to that user account. Edit Default Domain Controllers Policy Expand Computer Configuration, Policies, Windows Settings, Security Settings, Local Policies, click UserRights Assignment. Double-click Allow Logon Locally.
http://technet.microsoft.com/en-us/library/ee957044(v=ws.10).aspx
QUESTION 18
Your network contains a single Active Directory domain named contoso.com. The network contains two subnets. The subnets are configured as shown in the following table.

The network contains a member server named Server1 that runs Windows Server 2012 R2. Server1 has the DHCP Server server role installed. Server1 is configured to lease IP addresses to the two subnets. You discover that computers on the Warehouse subnet that have static IP addresses can communicate with the computers on the MainOffice subnet. Computers on the Warehouse subnet that obtain an IP address automatically can only communicate with other computers on the Warehouse subnet. You need to ensure that all of the computers on the Warehouse subnet can communicate with the computers on the MainOffice subnet. Which DHCP option should you configure on Server1?
A. 003 Router
B. 011 Resource Location Servers
C. 020 Nonlocal Source Routing
D. 019 IP Layer Forwarding
Answer: A
Explanation:
A. This option is normally used to assign a default gateway to DHCP clients on a subnet. A DHCP clientrequests this option.
B. This option specifies a list of IP addresses for resource location servers.
C. This option specifies whether the DHCP client enables or disables the forwarding at the IP Layer ofdatagrams that contain source routing information and were sent by a non-local host.
D. This option specifies whether the DHCP client should enable or disable forwarding of datagrams at the IP Layer.

http://technet.microsoft.com/en-us/library/dd145324(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/ee941211(v=ws.10).aspx
QUESTION 19
Your network contains an Active Directory domain named contoso.com. The network contains 500 client computers that run Windows 8. All of the client computers connect to the Internet by using a web proxy. You deploy a server named Server1 that runs Windows Server 2012 R2. Server1 has the DNS Server server role installed. You configure all of the client computers to use Server1 as their primary DNS server. You need to prevent Server1 from attempting to resolve Internet host names for the client computers. What should you do on Server1?
A. Configure the Security settings of the contoso.com zone.
B. Remove all root hints.
C. Create a primary zone named “.”.
D. Create a primary zone named “root”.
E. Create a primary zone named “GlobalNames”.
F. Create a forwarder that points to 169.254.0.1.
G. Create a stub zone named “root”.
H. Create a zone delegation for GlobalNames.contoso.com.
Answer: BC
Explanation:
Explanation:
B. necessary to remove the default root hints files.
C. Create a primary zone named “.” (dot zone, root).
When you install DNS on a Windows server that does not have a connection to the Internet, the zone for the domain is created and a root zone, also known as a dot zone, is also created. This root zone may prevent access to the Internet for DNS and for clients of the DNS. If there is a root zone, there are no other zones other than those that are listed with DNS, and you cannot configure forwarders or root hint servers.
Root Domain
This is the top of the tree, representing an unnamed level; it is sometimes shown as two empty quotation marks (“”), indicating a null value. When used in a DNS domain name, it is stated by a trailing period (.) to designate that the name is located at the root or highest level of the domain hierarchy. In this instance, the DNS domain name is considered to be complete and points to an exact location in the tree of names. Names stated this way are called fully qualified domain names (FQDNs).

http://technet.microsoft.com/en-us/library/cc772774%28v=ws.10%29.aspx
http://youtu.be/KjMDtlR6Mhk http://support.microsoft.com/kb/298148/en-us
QUESTION 20
Your company has a remote office that contains 600 client computers on a single subnet. You need to select a subnet mask for the network that will support all of the client computers. The solution must minimize the number of unused addresses. Which subnet mask should you select?
A. 255.255.252.0
B. 255.255.254.0
C. 255.255.255.0
D. 255.255.255.128
Answer: A
Explanation:
Using a subnet mask of 255.255.252.0 will result in the fewest number of unused IP addresses.
QUESTION 21
Your network contains three servers that run Windows Server 2012 R2. The servers are configured as shown in the following table.

Server3 is configured to obtain an IP address automatically. You need to prevent Server3 from receiving an IP address from Server1. What should you create on Server1?
A. A reservation
B. A filter
C. A scope option
D. An exclusion
Answer: B
Explanation:
A. For clients that require a constant IP address.
B. Filter to exclude MAC address of Server3.
C. Range of allowed IP’s to be assigned.
D. Exclude range of IP’s.
MAC address based filtering ensure that only a known set of devices in the system are able to obtain an IP Address from the DHCP.

Reservation and Exclusion, two incredibly different concepts. An exclusion is an address or range of addresses taken from a DHCP scope that the DHCP server is notallowed to hand out. For example, if you have set a DHCP server to exclude the address range 192.168.0.1-192.168.0.10 then the only way a computer on your network would get an address of 192.168.0.4 would be ifyou assigned it statically on that machine. This is because DHCP knows NOT to give this range of IP addresses out. A reservation is a specific IP addresses that is tied to a certain device through its MAC address. Forexample, if we have a workstation on the network that requires a certain IP address, but we don’t want to gothrough to trouble of assigning it statically, then we can create a reservation for it. So if the MAC address of theNIC on the computer is AA-BB-00FF-CC-AA and we want it to maintain the IP address of 192.168.0.100 thenwe would create a DHCP reservation under that particular scope saying that the IP address 192.168.0.100 is reserved only for the MAC address AA-BB-00-FF-CC-AA.
http://technet.microsoft.com/en-us/magazine/ff521761.aspx
http://technet.microsoft.com/en-us/library/cc726954(v=ws.10).aspx
http://www.windowsnetworking.com/kbase/WindowsTips/Windows2003/AdminTips/Network/DHCPReservationsandExclusions.html
QUESTION 22
Your network contains an Active Directory forest. The forest contains two domains named contoso.com and corp.contoso.com. The forest contains four domain controllers. The domain controllers are configured as shown in the following table.

All domain controllers are DNS servers. In the corp.contoso.com domain, you plan to deploy a new domain controller named DCS. You need to identify which domain controller must be online to ensure that DCS can be promoted successfully to a domain controller. Which domain controller should you identify?
A. DC1
B. DC2
C. DC3
D. DC4
Answer: C
Explanation:
A. Wrong Domain.
B. Wrong Domain.
C. Right domain, RID Master must be online.
D. Right domain, but Not needed to be online.
Relative ID (RID) Master
Allocates active and standby RID pools to replica domain controllers in the same domain. (corp.contoso.com) Must be online for newly promoted domain controllers to obtain a local RID pool that is required to advertise or when existing domain controllers have to update their current or standby RID pool allocation. The RID master is responsible for processing RID pool requests from all domain controllers in a particular domain. When a DC creates a security principal object such as a user or group, it attaches a unique Security ID (SID) to the object. This SID consists of a domain SID (the same for all SIDs created in a domain), and a relative ID (RID) that is unique for each security principal SID created in a domain. Each DC in a domain is allocated a pool of RIDs that it is allowed to assign to the security principals it creates. When a DC’s allocated RID pool falls below a threshold, that DC issues a request for additional RIDs to the domain’s RID master. The domain RID master responds to the request by retrieving RIDs from the domain’s unallocated RID pool and assigns them to the pool of the requesting DC At any one time, there can be only one domain controller acting as the RID master in the domain.

http://support.microsoft.com/kb/223346
QUESTION 23
Your network contains an Active Directory domain named contoso.com. You log on to a domain controller by using an account named Admin1. Admin1 is a member of the Domain Admins group. You view the properties of a group named Group1 as shown in the exhibit. Group1 is located in an organizational unit (OU) named OU1. You need to ensure that users from Group1 can modify the Security settings of OU1 only. What should you do from Active Directory Users and Computers?

A. Modify the Managed By settings on OU1.
B. Right-click contoso.com and select Delegate Control.
C. Right-click OU1 and select Delegate Control.
D. Modify the Security settings of Group1.
Answer: C
Explanation:
A. The distinguished name of the user that is assigned to manage this object.
B. Would delegate control to the whole domain.
C. Delegates control to the OU OU1 only.
D. Wrong Feature.
An organizational unit is the smallest scope or unit to which you can assign Group Policy settings or delegate administrative authority. A user can have administrative authority for all organizational units in a domain or for a single organizational unit. You can delegate administrative control to any level of a domain tree by creating organizational units within a domain and delegating administrative control for specific organizational units to particular users or groups. Administrative control can be assigned to a user or group by using the Delegation of Control Wizard or through the Authorization Manager console. Both of these tools allow you to assign rights or permissions to particular users or groups.
http://technet.microsoft.com/en-us/library/cc758565%28v=ws.10%29.aspx
http://technet.microsoft.com/en-us/library/cc778807%28v=ws.10%29.aspx
http://msdn.microsoft.com/en-us/library/windows/desktop/ms676857(v=vs.85).aspx
http://technet.microsoft.com/en-us/library/cc732524.aspx
QUESTION 24
Your network contains an Active Directory forest named contoso.com. All domain controllers currently run Windows Server 2008 R2. You plan to install a new domain controller named DC4 that runs Windows Server 2012 R2. The new domain controller will have the following configurations:
– Schema master
– Global catalog server
– DNS Server server role
– Active Directory Certificate Services server role
You need to identify which configurations Administrators by using the Active Directory Installation Wizard. Which two configurations should you identify? (Each correct answer presents part of the solution. Choose two.)
A. Transfer the schema master.
B. Enable the global catalog server.
C. Install the DNS Server role.
D. Install the Active Directory Certificate Services role.
Answer: AD
Explanation:
AD Installation Wizard will automatically install DNS and allows for the option to set it as a global catalog server. ADCS and schema must be done separately.

http://technet.microsoft.com/en-us/library/hh831457.aspx
QUESTION 25
Your network contains an Active Directory domain named contoso.com. The domain contains two domain controllers. The domain controllers are configured as shown in the following table.
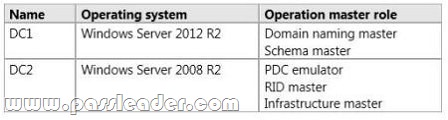
In the perimeter network, you install a new server named Server1 that runs Windows Server 2012 R2. Server1 is in a workgroup. You need to perform an offline domain join of Server1 to the contoso.com domain. What should you do first?
A. Transfer the PDC emulator role to DC1.
B. Run the djoin.exe command.
C. Run the dsadd.exe command.
D. Transfer the infrastructure master role to DC1.
Answer: B
Explanation:
A. Creates a new Active Directory computer.
B. Use djoin for offline join in the perimeter network.
C. Adds specific types of objects to the directory.
D. Add the local computer to a domain or workgroup.
To perform an offline domain join, you run commands by using a new tool named Djoin.exe. You use Djoin.exe to provision computer account data into AD DS. You also use it to insert the computer account data intothe Windows directory of the destination computer, which is the computer that you want to join to the domain. Create the account djoin /provision /domain winsrvtuts.wst /machine Win7 /savefile c:\yourFile.txt Run on the target systemdjoin /requestodj /loadfile c:\yourFile.txt /windowspath c:\Windows /localos.
http://technet.microsoft.com/en-us/library/ee617245.aspx
http://technet.microsoft.com/en-us/library/ff793312(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/cc753708(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/hh849798.aspx
http://winsrvtuts.com/2011/08/off-line-domain-join-with-djoin-exe/
http://technet.microsoft.com/en-us/library/offline-domain-join-djoin-step-bystep%28v=ws.10%29.aspx
QUESTION 26
Drag and Drop Question
Your network contains two Active Directory forests named adatum.com and contoso.com. Both forests contain multiple domains. A two-way trust exists between the forests. The contoso.com domain contains a domain local security group named Group1. Group1 contains contoso\user1 and adatum\user1. You need to ensure that Group1 can only contain users from the contoso.com domain. Which three actions should you perform? To answer, move three actions from the list of actions to the answer area and arrange them in the correct order.
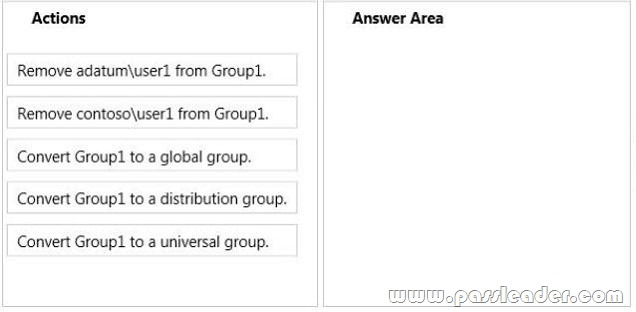
Answer:
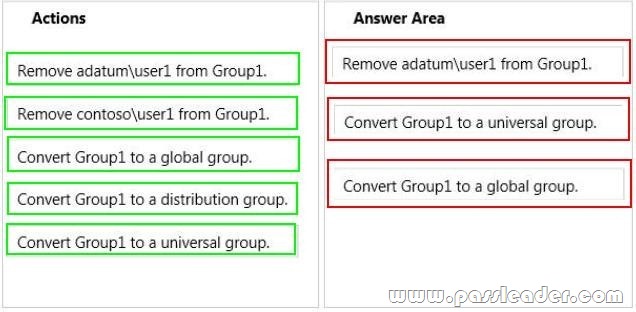
Explanation:
http://technet.microsoft.com/en-us/library/bb726978.aspx
http://technet.microsoft.com/en-us/library/cc755692(v=ws.10).aspx
QUESTION 27
Your network contains an Active Directory domain named contoso.com. You discover that when you join client computers to the domain manually, the computer accounts are created in the Computers container. You need to ensure that new computer accounts are created automatically in an organizational unit (OU) named Corp. Which tool should you use?
A. net.exe
B. redircmp.exe
C. regedit.exe
D. dsadd.exe
Answer: B
Explanation:
A. Used to stop/start protocols.
B. Redirects the default container for newly created computers to a specified, target organizational unit.
C. Modify local registry entries.
D. Adds specific types of objects to the directory.
Redirects the default container for newly created computers to a specified, target organizational unit (OU) so that newly created computer objects are created in the specific target OU instead of in CN=Computers. You must run the redircmp command from an elevated command prompt. Redircmp.exe is located in the C:\Windows\System32 folder. You must be a member of the Domain Admins group or the Enterprise Admins group to use this tool.
http://technet.microsoft.com/en-us/library/bb490949.aspx
http://technet.microsoft.com/en-us/library/cc770619(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/cc753708(v=ws.10).aspx
QUESTION 28
You have a server named Server2 that runs Windows Server 2012 R2. Server2 has the Hyper-V server role installed. The disks on Server2 are configured as shown in the exhibit. You create a virtual machine on Server2 named VM1. You need to ensure that you can configure a pass-through disk for VM1. What should you do?

A. Convert Disk 1 to a basic disk.
B. Take Disk 1 offline.
C. Create a partition on Disk 1.
D. Convert Disk 1 to a MBR disk.
Answer: B
Explanation:
http://blogs.technet.com/b/askcore/archive/2008/10/24/configuring-pass-through-disks-inhyperv.aspx
Pass-through Disk Configuration
Hyper-V allows virtual machines to access storage mapped directly to the Hyper-V server without requiring the volume be configured. The storage can either be a physical disk internal to the Hyper-V server or it can be a Storage Area Network (SAN) Logical Unit (LUN) mapped to the Hyper-V server. To ensure the Guest has exclusive access to the storage, it must be placed in an Offline state from the Hyper-V server perspective.
QUESTION 29
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed. Server1 is connected to two Fibre Channel SANs and is configured as shown in the following table.

You have a virtual machine named VM1. You need to configure VM1 to connect to SAN1. What should you do first?
A. Add one HBA.
B. Create a Virtual Fibre Channel SAN.
C. Create a Hyper-V virtual switch.
D. Configure network adapter teaming.
Answer: B
Explanation:
You need your virtualized workloads to connect easily and reliably to your existing storage arrays. WindowsServer 2012 provides Fibre Channel ports within the guest operating system, which allows you toconnect to Fibre Channel directly from within virtual machines. This feature protects your investments inFibre Channel, enables you to virtualize workloads that use direct access to Fibre Channel storage, allows youto cluster guest operating systems over Fibre Channel, and provides an important new storage option forservers hosted in your virtualization infrastructure. With this Hyper-V virtual Fibre Channel feature, you can connect to Fibre Channel storage from within a virtualmachine. This allows you to use your existing Fibre Channel investments to support virtualized workloads. Support for Fibre Channel in Hyper-V guests also includes support for many related features, such as virtualSANs, live migration, and MPIO.
http://technet.microsoft.com/en-us/library/hh831413.aspx
QUESTION 30
You work as a senior administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers on the contoso.com network have Windows Server 2012 installed, and all workstations have Windows 8 installed. You are running a training exercise for junior administrators. You are currently discussing the Always Offline Mode. Which of the following is TRUE with regards to the Always Offline Mode? (Choose all that apply.)
A. It allows for swifter access to cached files and redirected folders.
B. To enable Always Offline Mode, you have to satisfy the forest and domain functional-level requirements, as well as schema requirements.
C. It allows for lower bandwidth usage due to users are always working offline.
D. To enable Always Offline Mode, you must have workstations running Windows 7 or Windows Server 2008 R2.
Answer: AC
Explanation:
Offline Files have four modes of operation:
– Online
– Slow link
– Auto offline
– Manual offline
Offline Files transition between the three modes online, slow link and auto offline depending on connection speed. The user can always override the automatic mode selection by manually switching to manual offline mode. To determine the connection speed two pings with default packet size are sent to the file server. If the average round-trip time is below 80 ms (Windows 7) or 35 ms (Windows 8), the connection is put into online mode, otherwise into slow link mode. The latency value of 35/80 ms is configurable through the Group Policy setting Configure slow-link mode.
Reads, Writes and Synchronization
In online mode, changes to files are made on the file server as well as in the local cache (this induces a performance hit – see this article for details). Reads are satisfied from the local cache (if in sync). In slow link mode, changes to files are made in the local cache. The local cache is background-synchronized with the file server every 6 hours (Windows 7) or 2 hours (Windows 8), by default. This can be changed through the Group Policy setting Configure Background Sync. In auto offline mode, all reads and writes go to the local cache. No synchronization occurs. In manual offline mode, all reads and writes go to the local cache. No synchronization occurs by default, but background synchronization can be enabled through the Group Policy setting Configure Background Sync.
http://technet.microsoft.com/en-us/library/hh968298.aspx
http://helgeklein.com/blog/2012/04/windows-7-offline-files-survival-guide/
QUESTION 31
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012 R2. You need to configure a central store for the Group Policy Administrative Templates. What should you do on DC1?
A. From Server Manager, create a storage pool.
B. From Windows Explorer, copy the PolicyDefinitions folder to the SYSVOL\contoso.com\policies folder.
C. From Server Manager, add the Group Policy Management feature.
D. From Windows Explorer, copy the PolicyDefinitions folder to the NETLOGON share.
Answer: B
Explanation:
A. Create Disk Storage Pool.
B. PolicyDefinitions folder in SYSVOL.
C. Group Policy Management is a console for GPO Mgmt.
D. Folder is for logon scripts.
PolicyDefinitions folder within the SYSVOL folder hierarchy. By placing the ADMX files in this directory,they are replicated to every DC in the domain; by extension, the ADMX-aware Group Policy ManagementConsole in Windows Vista, Windows 7, Windows Server 2008 and R2 can check this folder as an additionalsource of ADMX files, and will report them accordingly when setting your policies. By default, the folder is not created. Whether you are a single DC or several thousand, I would stronglyrecommend you create a Central Store and start using it for all your ADMX file storage. It really does work well. The Central Store To take advantage of the benefits of .admx files, you must create a Central Store in the SYSVOL folder ona domain controller. The Central Store is a file location that is checked by the Group Policy tools. The GroupPolicy tools use any .admx files that are in the Central Store. The files that are in the Central Store are laterreplicated to all domain controllers in the domain. To create a Central Store for .admx and .adml files, create a folder that is named PolicyDefinitions in thefollowing location: \\FQDN\SYSVOL\FQDN\policies
Note: FQDN is a fully qualified domain name.
http://tigermatt.wordpress.com/tag/policydefinitions/
http://support.microsoft.com/kb/929841/en-us
http://www.virtuallyimpossible.co.uk/how-to-create-a-group-policy-central-store/
http://support.microsoft.com/kb/2741591/en-us
QUESTION 32
You install Windows Server 2012 R2 on a standalone server named Server1. You configure Server1 as a VPN server. You need to ensure that client computers can establish PPTP connections to Server1. Which two firewall rules should you create? (Each correct answer presents part of the solution. Choose two.)
A. An inbound rule for protocol 47
B. An outbound rule for protocol 47
C. An inbound rule for TCP port 1723
D. An inbound rule for TCP port 1701
E. An outbound rule for TCP port 1723
F. An outbound rule for TCP port 1701
Answer: AC
Explanation:
To enable VPN tunnels between individual host computers or entire networks that have a firewall between them, you must open the following ports:
– PPTP
* To allow PPTP tunnel maintenance traffic, open TCP 1723.
* To allow PPTP tunneled data to pass through router, open Protocol ID 47.
– L2TP over IPSec
* To allow Internet Key Exchange (IKE), open UDP 500.
* To allow IPSec Network Address Translation (NAT-T) open UDP 5500.
* To allow L2TP traffic, open UDP 1701.
http://windowsitpro.com/networking/which-ports-do-you-need-open-firewall-allow-pptp-and-l2tp-over-ipsec-vpn-tunnels
If you use a personal firewall or a broadband router, or if there are routers or firewalls between the VPN client and the VPN server, the following ports and protocol must be enabled for PPTP on all firewalls and routers that are between the VPN client and the VPN server:
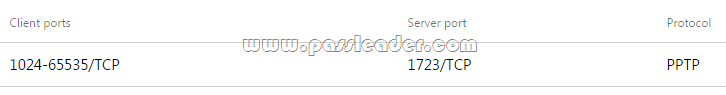
Additionally, you must enable IP PROTOCOL 47 (GRE).
https://support.microsoft.com/en-us/help/314076/how-to-configure-a-connection-to-a-virtual-private-network-vpn-in-windows-xp
QUESTION 33
Your network contains an Active Directory domain named adatum.com. The computer accounts for all member servers are located in an organizational unit (OU) named Servers. You link a Group Policy Object (GPO) to the Servers OU. You need to ensure that the domain’s Backup Operators group is a member of the local Backup Operators group on each member server. The solution must not remove any groups from the local Backup Operators groups. What should you do?
A. Add a restricted group named adatum\Backup Operators.
Add Backup Operators to the This group is a member of list.
B. Add a restricted group named adatum\Backup Operators.
Add Backup Operators to the Members of this group list.
C. Add a restricted group named Backup Operators.
Add adatum\Backup Operators to the This group is a member of list.
D. Add a restricted group named Backup Operators.
Add adatum\Backup Operators to the Members of this group list.
Answer: A
Explanation:
A. The Member Of list specifies which other groups the restricted group should belong to.
B. Needs to be added to member of list.
C. Wrong group.
D. Wrong group.
http://technet.microsoft.com/en-us/library/cc957640.aspx
QUESTION 34
Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2. An application named Appl.exe is installed on all client computers. Multiple versions of Appl.exe are installed on different client computers. Appl.exe is digitally signed. You need to ensure that only the latest version of Appl.exe can run on the client computers. What should you create?
A. An application control policy packaged app rule
B. A software restriction policy certificate rule
C. An application control policy Windows Installer rule
D. An application control policy executable rule
Answer: D
Explanation:
A. A publisher rule for a Packaged app is based on publisher, name and version.
B. You can create a certificate rule that identifies software and then allows or does not allow the software torun, depending on the security level.
C. For .msi or .msp.
D. Executable Rules, for .exe and can be based on Publisher, Product name, filename and version.
Use Certificate Rules on Windows Executables for Software Restriction Policies
This security setting determines if digital certificates are processed when a user or process attempts to runsoftware with an .exe file name extension. This security settings is used to enable or disable certificate rules, atype of software restriction policies rule. With software restriction policies, you can create a certificate rule thatwill allow or disallow software that is signed by Authenticode to run, based on the digital certificate that isassociated with the software. In order for certificate rules to take effect, you must enable this security setting. When certificate rules are enabled, software restriction policies will check a certificate revocation list (CRL) tomake sure the software’s certificate and signature are valid. This may decrease performance when start signedprograms. You can disable this feature. On Trusted Publishers Properties, clear the Publisher and Timestampcheck boxes.

http://technet.microsoft.com/en-us/library/dd759068.aspx
http://technet.microsoft.com/en-us/library/hh994588.aspx
http://www.grouppolicy.biz/2012/08/how-manage-published-a-k-a-metro-apps-in-windows8-using-grouppolicy/
http://technet.microsoft.com/en-us/library/hh994597.aspx#BKMK_Cert_Rules
http://technet.microsoft.com/en-us/library/cc782660%28v=ws.10%29.aspx
QUESTION 35
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. You need to ensure that the local Administrator account on all computers is renamed to L_Admin. Which Group Policy settings should you modify?
A. Security Options
B. User Rights Assignment
C. Restricted Groups
D. Preferences
Answer: A
Explanation:
http://technet.microsoft.com/en-us/library/cc747484(v=ws.10).aspx
QUESTION 36
You have a server that runs Windows Server 2012 R2. The disks on the server are configured as shown in the exhibit. You need to create a storage pool that contains Disk 1 and Disk 2. What should you do first?
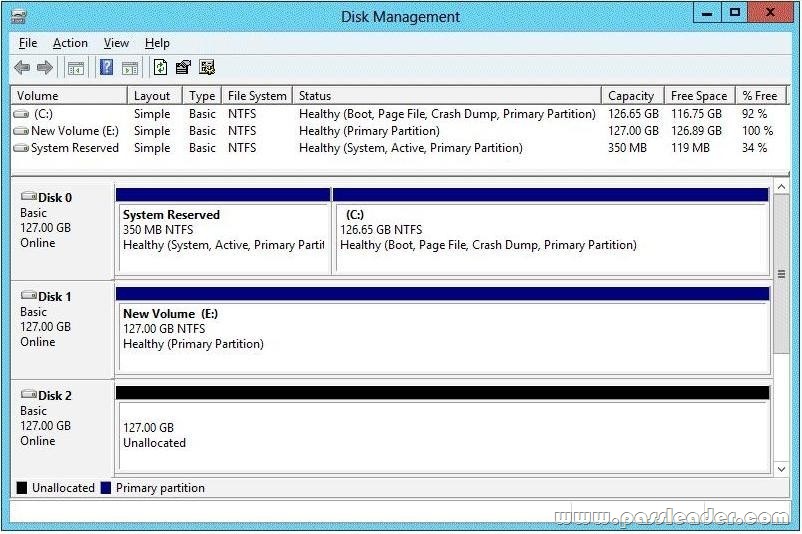
A. Delete volume E
B. Convert Disk 1 and Disk 2 to dynamic disks
C. Convert Disk 1 and Disk 2 to GPT disks
D. Create a volume on Disk 2
Answer: A
Explanation:
Storage Pools use unallocated space. There is no way to create a storage pool with existing data. Storage pools are only a collection ofdrives that are managed by windows.
http://technet.microsoft.com/en-us/library/ff399688.aspx
http://technet.microsoft.com/en-us/library/hh758075.aspx
QUESTION 37
You have a server named Server1 that runs Windows Server 2012 R2. You add a 4TB disk named Disk 5 to Server1. You need to ensure that you can create a 3TB volume on Disk 5. What should you do?
A. Create a storage pool.
B. Convert the disk to a dynamic disk.
C. Create a VHD, and then attach the VHD.
D. Convert the disk to a GPT disk.
Answer: D
Explanation:
MBR max is 2TB, the disk must be GPT. For any hard drive over 2TB, we need to use GPT partition. If you have a disk larger than 2TB size, the rest ofthe disk space will not be used unless you convert it to GPT. An existing MBR partition can’t be converted to GPT unless it is completely empty; you must either deleteeverything and convert or create the partition as GPT. It is not possible to boot to a GPT partition, impossible to convert MBR to GPT without data loss.
http://msdn.microsoft.com/en-us/library/windows/hardware/gg463525.aspx
QUESTION 38
You have a server named Server1 that has a Server Core installation of Windows Server 2008 R2. Server1 has the DHCP Server server role and the File Server server role installed. You need to upgrade Server1 to Windows Server 2012 R2 with the graphical user interface (GUI). The solution must meet the following requirements:
– Preserve the server roles and their configurations.
– Minimize Administrative effort.
What should you do?
A. On Server1, run setup.exe from the Windows Server 2012 R2 installation media and select Server with a GUI.
B. Start Server1 from the Windows Server 2012 R2 installation media and select Server Core Installation.
When the installation is complete, add the Server Graphical Shell feature.
C. Start Server1 from the Windows Server 2012 R2 installation media and select Server with a GUI.
D. On Server1, run setup.exe from the Windows Server 2012 R2 installation media and select Server Core Installation.
When the installation is complete, add the Server Graphical Shell feature.
Answer: D
Explanation:
A. Server is on 2008 R2 core, must install 2012 R2 core and then GUI.
B. Not least effort.
C. Not least effort.
D. Upgrade to 2012 R2 and install GUI shell.
http://technet.microsoft.com/en-us/library/jj574204.aspx
Upgrades that switch from a Server Core installation to the Server with a GUI mode of Windows Server 2012 R2 in one step (and vice versa) are not supported. However, after upgrade is complete, Windows Server 2012 R2 allows you to switch freely between Server Core and Server with a GUI modes.
For more information about these installation options, how to convert between them, and how to use the new Minimal Server Interface and Features on Demand, see:
http://technet.microsoft.com/library/hh831786
QUESTION 39
Your network contains two servers named Server1 and Server2 that run Windows Server 2012 R2. You need to install the Remote Desktop Services server role on Server2 remotely from Server1. Which tool should you use?
A. The dsadd.exe command
B. The Server Manager console
C. The Remote Desktop Gateway Manager console
D. The Install-RemoteAccess cmdlet
Answer: B
Explanation:
A. Adds specific types of objects to the directory.
B. You can manage remote server by Server Manager and install roles/features.
C. Remote Desktop Gateway (RD Gateway) is a role service that enables authorized remote users to connectto resources on an internal corporate or private network, from any Internet-connected device that can run theRemote Desktop Connection (RDC) client.
D. Performs prerequisite checks for DirectAccess (DA) to ensure that it can be installed, installs DA for remoteaccess (RA) (includes management of remote clients) or for management of remote clients only, and installsVPN (both Remote Access VPN and siteto-site VPN).

http://technet.microsoft.com/en-us/library/cc753708(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/hh831456.aspx
http://technet.microsoft.com/en-us/library/cc725706.aspx
http://technet.microsoft.com/en-us/library/hh918408(v=wps.620).aspx
QUESTION 40
You have a server named Server1 that runs a full installation of Windows Server 2012 R2. You need to uninstall the graphical user interface (GUI) on Server1. You must achieve this goal by using the minimum amount of Administrative effort. What should you do?
A. Reinstall Windows Server 2012 R2 on the server.
B. From Server Manager, uninstall the User Interfaces and Infrastructure feature.
C. From Windows PowerShell, run Uninstall-WindowsFeature PowerShell-ISE.
D. From Windows PowerShell, run Uninstall-WindowsFeature Desktop-Experience.
Answer: B
Explanation:
A. Not least effort.
B. Quick and Easy.
C. Uninstalls PS-ISE.
D. Doesn’t remove all GUI components.

http://www.petri.co.il/switching-gui-server-core-windows-server-2012.htm
Get the newest PassLeader 70-410 VCE dumps here: http://www.passleader.com/70-410.html (512 Q&As Dumps –> 528 Q&As Dumps)
And, DOWNLOAD the newest PassLeader 70-410 PDF dumps from Cloud Storage for free: https://drive.google.com/open?id=0B-ob6L_QjGLpfnJzOE1fWnlJOWVtaE93SnJNT3gtaTNYYnVpZkw5THBSMWRKbFlfaXh1azg


