Valid MS-102 Dumps shared by PassLeader for Helping Passing MS-102 Exam! PassLeader now offer the newest MS-102 VCE dumps and MS-102 PDF dumps, the PassLeader MS-102 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader MS-102 dumps with VCE and PDF here: https://www.passleader.com/ms-102.html (587 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader MS-102 dumps from Cloud Storage: https://drive.google.com/drive/folders/1EgG1HXOLli3rw4OX-3NpXshMm5dHpomY
NEW QUESTION 533
You have a Microsoft 365 subscription. From the Security & Compliance admin center, you create a role group named US eDiscovery Managers by copying the eDiscovery Manager role group. You need to ensure that the users in the new role group can only perform content searches of mailbox content for users in the United States.
Solution: From the Security & Compliance admin center, you modify the roles of the US eDiscovery Managers role group.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
You have to create a compliance security filter.
https://docs.microsoft.com/en-us/microsoft-365/compliance/permissions-filtering-for-content-search?view=o365-worldwide
NEW QUESTION 534
Your network contains an Active Directory domain named contoso.com that is synced to Microsoft Azure Active Directory (Azure AD). You manage Windows 10 devices by using Microsoft System Center Configuration Manager (Current Branch). You configure pilot co-management. You add a new device named Device1 to the domain. You install the Configuration Manager client on Device1. You need to ensure that you can manage Device1 by using Microsoft Intune and Configuration Manager.
Solution: Define a Configuration Manager device collection as the pilot collection. Add Device1 to the collection.
Does this meet the goal?
A. Yes
B. No
Answer: A
Explanation:
Device1 has the Configuration Manager client installed so you can manage Device1 by using Configuration Manager. To manage Device1 by using Microsoft Intune, the device has to be enrolled in Microsoft Intune. In the Co-management Pilot configuration, you configure a Configuration Manager Device Collection that determines which devices are auto-enrolled in Microsoft Intune. You need to add Device1 to the Device Collection so that it auto-enrols in Microsoft Intune. You will then be able to manage Device1 using Microsoft Intune.
https://docs.microsoft.com/en-us/configmgr/comanage/how-to-enable
NEW QUESTION 535
You have a Microsoft 365 subscription. You need to prevent users from accessing your Microsoft SharePoint Online sites unless the users are connected to your on-premises network.
Solution: From the Device Management admin center, you create a trusted location and a compliance policy.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
Conditional Access in SharePoint Online can be configured to use an IP Address white list to allow access.
https://techcommunity.microsoft.com/t5/Microsoft-SharePoint-Blog/Conditional-Access-in-SharePoint-Online-and-OneDrive-for/ba-p/46678
NEW QUESTION 536
You have a new Microsoft 365 subscription. You need to prevent users from sending email messages that contain Personally Identifiable Information (PII).
Solution: From the Azure portal, you create a Microsoft Azure Information Protection label and an Azure Information Protection policy.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
As of 8/31/2021, efforts to create DLP in Exchange Admin center are redirected to M365 Compliance Center. Currently, the only place to create a data loss prevention policy is through the M365 Compliance admin center (now known as the Microsoft 365 Compliance Center) where you can create a single DLP policy to help protect content in SharePoint, OneDrive, Exchange, Teams, and now Endpoint Devices.
https://docs.microsoft.com/en-us/microsoft-365/compliance/how-dlp-works-between-admin-centers?view=o365-worldwide
NEW QUESTION 537
You have a Microsoft 365 subscription. From the Security & Compliance admin center, you create a role group named US eDiscovery Managers by copying the eDiscovery Manager role group. You need to ensure that the users in the new role group can only perform content searches of mailbox content for users in the United States.
Solution: From the Azure Active Directory admin center, you create a conditional access policy.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
This will need to be done in the Compliance Portal.
https://docs.microsoft.com/en-us/microsoft-365/compliance/assign-ediscovery-permissions?view=o365-worldwide
NEW QUESTION 538
You have an Azure Active Directory (Azure AD) tenant that contains a user named User1. Your company purchases a Microsoft 365 subscription. You need to ensure that User1 is assigned the required role to create file policies and manage alerts in the Cloud App Security admin center.
Solution: From the Azure Active Directory admin center, you assign the Security administrator role to User1.
Does this meet the goal?
A. Yes
B. No
Answer: A
Explanation:
The Security administrator has Full access with full permissions in Defender for Cloud Apps.
https://docs.microsoft.com/en-us/cloud-app-security/manage-admins
NEW QUESTION 539
You have a Microsoft 365 subscription that contains a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com. In the tenant, you create a user named User1. You need to ensure that User1 can publish retention labels from the Microsoft 365 compliance center. The solution must use the principle of least privilege. To which role group should you add User1?
A. Security Administrator
B. Records Management
C. Compliance Administrator
D. eDiscovery Manager
Answer: B
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-with-retention?view=o365-worldwide
NEW QUESTION 540
Your company has 10 offices. The network contains an Active Directory domain named contoso.com. The domain contains 500 client computers. Each office is configured as a separate subnet. You discover that one of the offices has the following:
– Computers that have several preinstalled applications.
– Computers that use nonstandard computer names.
– Computers that have Windows 10 preinstalled.
– Computers that are in a workgroup.
You must configure the computers to meet the following corporate requirements:
– All the computers must be joined to the domain.
– All the computers must have computer names that use a prefix of CONTOSO.
– All the computers must only have approved corporate applications installed.
You need to recommend a solution to redeploy the computers. The solution must minimize the deployment time. What should you recommend?
A. a provisioning package
B. wipe and load refresh
C. Windows Autopilot
D. an in-place upgrade
Answer: A
Explanation:
By using a Provisioning, IT administrators can create a self-contained package that contains all of the configuration, settings, and apps that need to be applied to a device.
Incorrect Answers:
Not C: With Windows Autopilot the user can set up pre-configure devices without the need consult their IT administrator.
Not D: Use the In-Place Upgrade option when you want to keep all (or at least most) existing applications.
https://docs.microsoft.com/en-us/windows/deployment/windows-10-deployment-scenarios
https://docs.microsoft.com/en-us/windows/deployment/windows-autopilot/windows-autopilot
NEW QUESTION 541
You have a Microsoft 365 tenant. Company policy requires that all Windows 10 devices meet the following minimum requirements:
– Require complex passwords.
– Require the encryption of data storage devices.
– Have Microsoft Defender Antivirus real-time protection enabled.
You need to prevent devices that do not meet the requirements from accessing resources in the tenant. Which two components should you create? (Each correct answer presents part of the solution. Choose two.)
A. a configuration policy
B. a compliance policy
C. a security baseline profile
D. a conditional access policy
E. a configuration profile
Answer: BD
Explanation:
https://docs.microsoft.com/en-us/mem/intune/protect/device-compliance-get-started
NEW QUESTION 542
You have a Microsoft 365 E5 tenant. You need to ensure that when a document containing a credit card number is added to the tenant, the document is encrypted. Which policy should you use?
A. a retention policy
B. a retention label policy
C. an auto-labeling policy
D. an insider risk policy
Answer: C
Explanation:
First create the sensitivity label, then apply the label with auto-labeling policy using PCI Data Security Standard (PCI DSS) as a template.
https://docs.microsoft.com/en-us/microsoft-365/compliance/apply-sensitivity-label-automatically?view=o365-worldwide
NEW QUESTION 543
You have a Microsoft 365 E5 subscription that uses Microsoft SharePoint Online. You need to enable co-authoring for files that are encrypted by using sensitivity labels. What should you use?
A. the Microsoft 365 Defender portal
B. the SharePoint admin center
C. the Microsoft 365 admin center
D. the Microsoft 365 compliance center
Answer: D
Explanation:
Sign in to the Microsoft Purview Compliance Portal as a global admin for your tenant. From the navigation pane, select Settings –> Co-authoring for files with sensitivity files. Then select Turn on co-authoring for files with sensitivity labels, and Apply.
NEW QUESTION 544
You have a Microsoft 365 subscription. You need to integrate Microsoft Defender for Identity with Microsoft Defender for Cloud Apps. What should you configure in the Microsoft Defender for Cloud Apps portal?
A. the Threat Protection settings
B. a session policy
C. a log collector
D. an OAuth app policy
Answer: A
Explanation:
https://learn.microsoft.com/en-us/defender-cloud-apps/mdi-integration#enable-defender-for-identity
NEW QUESTION 545
You have a Microsoft 365 tenant. You plan to manage incidents in the tenant by using the Microsoft 365 Defender. Which Microsoft service source will appear on the Incidents page of the Microsoft 365 Defender?
A. Microsoft Defender for Cloud Apps
B. Microsoft Purview
C. Azure Information Protection
D. Azure Web Application Firewall
Answer: A
Explanation:
Microsoft 365 Defender alerts may come from solutions like Microsoft Defender for Endpoint, Microsoft Defender for Office 365, Microsoft Defender for Cloud Apps, and the app governance add-on for Microsoft Defender for Cloud Apps.
https://learn.microsoft.com/en-us/microsoft-365/security/defender/investigate-alerts?view=o365-worldwide
NEW QUESTION 546
You have a Microsoft 365 E5 subscription and an on-premises server named Server1 that runs Windows Server. You plan to implement Cloud Discovery in Microsoft Defender for Cloud Apps. You need to deploy a log collector to Server1. What should you install on Server1 first?
A. the Azure Monitor agent
B. Docker
C. the Azure Connected Machine agent
D. a Microsoft Defender for Identity sensor
Answer: C
Explanation:
The Log Collector supports the Container deployment mode. It runs as a Docker image on Windows, Ubuntu on-premises, Ubuntu in Azure, RHEL on-premises or CentOS.
https://learn.microsoft.com/en-us/defender-cloud-apps/discovery-docker
NEW QUESTION 547
You have a Microsoft 365 subscription. You need to investigate user activity in Microsoft 365, including from where users signed in, which applications were used, and increases in activity during the past month. The solution must minimize administrative effort. Which admin center should you use?
A. Azure ATP
B. Security & Compliance
C. Cloud App Security
D. Flow
Answer: C
Explanation:
To investigate user activity across Microsoft 365 – including sign-in locations, applications used, and unusual activity patterns – the best tool is Microsoft Cloud App Security (MCAS), now part of Microsoft Defender for Cloud Apps.
NEW QUESTION 548
You plan to use the Security & Compliance admin center to import several PST files into Microsoft 365 mailboxes. Which three actions should you perform before you import the data? (Each correct answer presents part of the solution. Choose three.)
A. From the Exchange admin center, create a public folder.
B. Copy the PST files by using AzCopy.
C. From the Exchange admin center, assign admin roles.
D. From the Microsoft Azure portal, create a storage account that has a blob container.
E. From the Microsoft 365 admin center, deploy an add-in.
F. Create a mapping file that uses the CSV file format.
Answer: BCF
Explanation:
You have to be assigned the Mailbox Import Export role in Exchange Online to import PST files to Office 365 mailboxes. By default, this role isn’t assigned to any role group in Exchange Online. You can add the Mailbox Import Export role to the Organization Management role group. Or you can create a role group, assign the Mailbox Import Export role, and then add yourself as a member.
NEW QUESTION 549
You deploy Microsoft Azure Information Protection. You need to ensure that a security administrator named SecAdmin1 can always read and inspect data protected by Azure Rights Management (Azure RMS). What should you do?
A. From the Security & Compliance admin center, add User1 to the eDiscovery Manager role group.
B. From the Azure Active Directory admin center, add User1 to the Security Reader role group.
C. From the Security & Compliance admin center, add User1 to the Compliance Administrator role group.
D. From Windows PowerShell, enable the super user feature and assign the role to SecAdmin1.
Answer: D
Explanation:
The super user feature of the Azure Rights Management service from Azure Information Protection ensures that authorized people and services can always read and inspect the data that Azure Rights Management protects for your organization. However, the super user feature is not enabled by default. The PowerShell cmdlet Enable-AadrmSuperUserFeature is used to manually enable the super user feature.
https://docs.microsoft.com/en-us/azure/information-protection/configure-super-users
NEW QUESTION 550
You have a Microsoft 365 tenant. All users are assigned the Enterprise Mobility + Security license. You need to ensure that when users join their device to Microsoft Azure Active Directory (Azure AD), the device is enrolled in Microsoft Intune automatically. What should you configure?
A. Enrollment restrictions from the Intune admin center.
B. Device enrollment managers from the Intune admin center.
C. MAM User scope from the Azure Active Directory admin center.
D. MDM User scope from the Azure Active Directory admin center.
Answer: D
Explanation:
https://docs.microsoft.com/en-us/intune/windows-enroll
NEW QUESTION 551
You have a Microsoft 365 subscription. Some users have iPads that are managed by your company. You plan to prevent the iPad users from copying corporate data in Microsoft Word and pasting the data into other applications. What should you create?
A. A conditional access policy.
B. A compliance policy.
C. An app protection policy.
D. An app configuration policy.
Answer: C
Explanation:
An App Protection Policy (APP) controls how corporate data is used within managed apps (such as Microsoft Word, Excel, Outlook, etc.) on mobile devices. To prevent users from copying corporate data from Microsoft 365 apps (like Word) into personal or unmanaged apps on mobile devices such as iPads, you need to use an App Protection Policy (APP) in Microsoft Intune.
NEW QUESTION 552
You create a new Microsoft 365 subscription and assign Microsoft 365 E3 licenses to 100 users. From the Security & Compliance admin center, you enable auditing. You are planning the auditing strategy. Which three activities will be audited by default? (Each correct answer presents a complete solution. Choose three.)
A. An administrator creates a new Microsoft SharePoint site collection.
B. An administrator creates a new mail flow rule.
C. A user shares a Microsoft SharePoint folder with an external user.
D. A user delegates permissions to their mailbox.
E. A user purges messages from their mailbox.
Answer: ABC
Explanation:
Although mailbox audit logging on by default is enabled for all organizations, only users with E5 licenses will return mailbox audit log events in audit log searches in the Security & Compliance Center or via the Office 365 Management Activity API by default. As the question says they only have E3 licenses, user actions on their mailboxes are not logged by default.
NEW QUESTION 553
You have a Microsoft 365 subscription. From the Security & Compliance admin center, you create a content search of a mailbox. You need to view the content of the mail messages found by the search as quickly as possible. What should you select from the Content search settings?
A. Export report.
B. Export results.
C. Re-run.
D. View results.
Answer: B
Explanation:
There is no “View Results” option. You can preview results but that will only show up to 100 emails. To guarantee you’re getting all results, you’ll need to export them to a PST file.
https://docs.microsoft.com/en-us/microsoft-365/compliance/limits-for-content-search
NEW QUESTION 554
You have a Microsoft 365 subscription and an on-premises Active Directory domain named contoso.com. All client computers run Windows 10 Enterprise and are joined to the domain. You need to enable Windows Defender Credential Guard on all the computers. What should you do?
A. From the Security & Compliance admin center, configure the DKIM signatures for the domain.
B. From a domain controller, create a Group Policy object (GPO) that enables the Restrict delegation of credentials to remote servers setting.
C. From the Security & Compliance admin center, create a device security policy.
D. From a domain controller, create a Group Policy object (GPO) that enabled the Turn On Virtualization Based Security setting.
Answer: D
Explanation:
https://docs.microsoft.com/en-us/windows/security/identity-protection/credential-guard/credential-guard-manage
NEW QUESTION 555
Your company has a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com. The company purchases a cloud app named App1 that supports Microsoft Cloud App Security monitoring. You configure App1 to be available from the My Apps portal. You need to ensure that you can monitor App1 from Cloud App Security. What should you do?
A. From the Azure Active Directory admin center, create a conditional access policy.
B. From the Azure Active Directory admin center, create an app registration.
C. From the Device Management admin center, create an app protection policy.
D. From the Device Management admin center, create an app configuration policy.
Answer: A
Explanation:
Microsoft Defender for Cloud Apps builds on Azure AD conditional access policies to enable real-time monitoring and control of granular actions with SaaS apps, such as blocking downloads, uploads, copy and paste, and printing.
https://learn.microsoft.com/en-us/security/zero-trust/zero-trust-identity-device-access-policies-workloads?view=o365-worldwide#saas-app-recommendations-for-zero-trust
NEW QUESTION 556
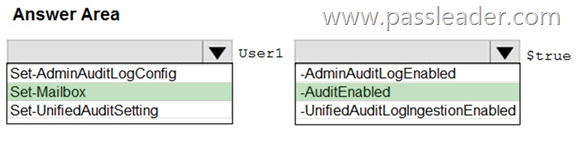
HotSpot
You have a new Microsoft 365 subscription. A user named User1 has a mailbox in Microsoft Exchange Online. You need to log any changes to the mailbox folder permissions of User1. Which command should you run? (To answer, select the appropriate options in the answer area.)
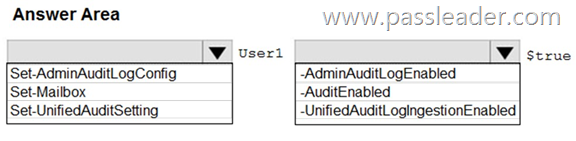
Explanation:
To enable auditing for a single mailbox (in this example, belonging to Holly Sharp), use this PowerShell command: Set-Mailbox username -AuditEnabled $true
https://support.microsoft.com/en-us/help/4026501/office-auditing-in-office-365-for-admins
https://docs.microsoft.com/en-us/powershell/module/exchange/mailboxes/set-mailbox?view=exchange-ps
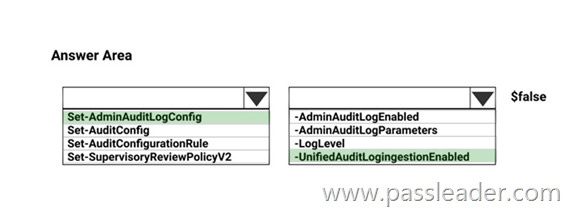
NEW QUESTION 557
HotSpot
You create a Microsoft 365 subscription. Your company’s privacy policy states that user activities must NOT be audited. You need to disable audit logging in Microsoft 365. How should you complete the command? (To answer, select the appropriate options in the answer area.)
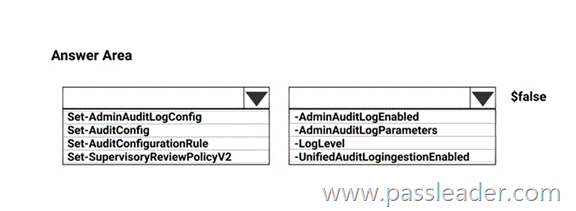
Explanation:
https://docs.microsoft.com/en-us/office365/securitycompliance/turn-audit-log-search-on-or-off
NEW QUESTION 558
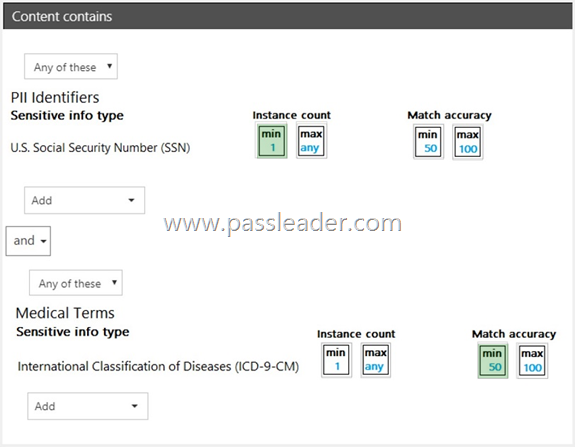
HotSpot
You have a data loss prevention (DLP) policy. You need to increase the likelihood that the DLP policy will apply to data that contains medical terms from the International Classification of Diseases (ICD-9-CM). The solution must minimize the number of false positives. Which two settings should you modify? (To answer, select the appropriate settings in the answer area.)
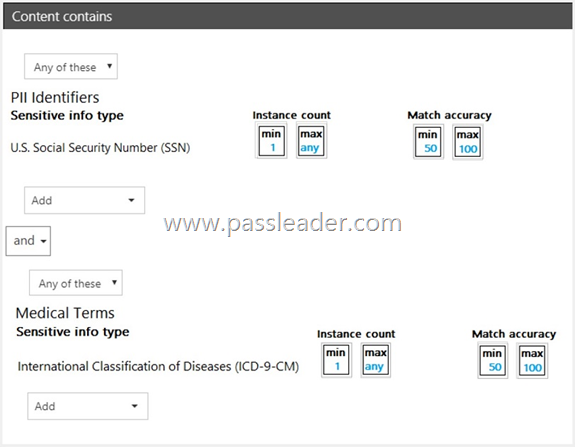
Explanation:
https://docs.microsoft.com/en-us/office365/securitycompliance/data-loss-prevention-policies
https://docs.microsoft.com/en-us/office365/securitycompliance/what-the-sensitive-information-types-look-for#international-classification-of-diseases-icd-9-cm
NEW QUESTION 559
……
Get the newest PassLeader MS-102 VCE dumps here: https://www.passleader.com/ms-102.html (587 Q&As Dumps)
And, DOWNLOAD the newest PassLeader MS-102 PDF dumps from Cloud Storage for free: https://drive.google.com/drive/folders/1EgG1HXOLli3rw4OX-3NpXshMm5dHpomY