Valid SC-401 Dumps shared by PassLeader for Helping Passing SC-401 Exam! PassLeader now offer the newest SC-401 VCE dumps and SC-401 PDF dumps, the PassLeader SC-401 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader SC-401 dumps with VCE and PDF here: https://www.passleader.com/sc-401.html (237 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader SC-401 dumps from Cloud Storage: https://drive.google.com/drive/folders/13683SpK3sRCjLQqgxAcbbmi8fxAV-smt
NEW QUESTION 201
You have a Microsoft 365 E5 subscription that contains a device named Device1. You need to enable Endpoint data loss prevention (Endpoint DLP) for Device1. What should you do first in the Microsoft Purview portal?
A. Turn on device onboarding.
B. Enable Microsoft Priva Privacy Risk Management.
C. Create a Microsoft Purview Information Barriers (IBs) segment.
D. Add a Microsoft Purview Information Protection scanner cluster.
E. Onboard Device1 to Microsoft Purview.
Answer: A
Explanation:
https://learn.microsoft.com/en-us/purview/endpoint-dlp-getting-started
https://learn.microsoft.com/en-us/purview/device-onboarding-overview
NEW QUESTION 202
You need to create a retention policy to delete content after seven years from the following locations:
– Exchange Online email.
– SharePoint Online sites.
– OneDrive accounts.
– Microsoft 365 Groups.
– Teams channel messages.
– Teams chats.
What is the minimum number of retention policies that you should create?
A. 1
B. 2
C. 3
D. 4
Answer: B
NEW QUESTION 203
You have a Microsoft 365 E5 subscription that contains 500 Windows devices. You plan to deploy Microsoft Purview Data Security Posture Management for AI (DSPM for AI). You need to ensure that you can monitor user activities on third-party generative AI websites. Which two prerequisites should you complete for DSPM for AI? (Each correct answer presents part of the solution. Choose two.)
A. Create an Endpoint data loss prevention (Endpoint DLP) policy.
B. Onboard the devices to Microsoft Purview.
C. Install the Microsoft Purview extension on the devices.
D. Create a communication compliance policy.
E. Enroll the devices in Microsoft Intune.
F. Create a data leaks policy.
Answer: AB
Explanation:
Required for monitoring interactions with third-party generative AI sites:
[B] * Devices are onboarded to Microsoft Purview, required for:
– Gaining visibility into sensitive information that’s shared with third-party generative AI sites. For example, a user pastes credit card numbers into ChatGPT.
[A]- Applying endpoint DLP policies to warn or block users from sharing sensitive information with third-party generative AI sites. For example, a user identified as elevated risk in Adaptive Protection is blocked with the option to override when they paste credit card numbers into ChatGPT.
https://learn.microsoft.com/en-us/purview/dspm-for-ai-considerations
NEW QUESTION 204
You have a Microsoft 365 E5 subscription. You are implementing insider risk management. You need to maximize the amount of historical data that is collected when an event is triggered. What is the maximum number of days that historical data can be collected?
A. 30
B. 60
C. 90
D. 180
Answer: C
NEW QUESTION 205
You have a Microsoft 365 E5 subscription that contains a user named User1. You need to ensure that all email messages that contain attachments are encrypted automatically by using Microsoft Purview Message Encryption. What should you create?
A. a mail flow rule
B. a sensitivity label
C. a data loss prevention (DLP) policy
D. an information barrier segment
Answer: A
Explanation:
One way to enable Microsoft Purview Message Encryption is for Exchange Online and Exchange Online Protection administrators to define mail flow rules. These rules determine under what conditions email messages should be encrypted. When an encryption action is set for a rule, any messages that match the rule conditions are encrypted before they’re sent. Mail flow rules are flexible, letting you combine conditions so you can meet specific security requirements in a single rule. For example, you can create a rule to encrypt all messages that contain specified keywords and are addressed to external recipients. Microsoft Purview Message Encryption also encrypts replies from recipients of encrypted email.
https://learn.microsoft.com/en-us/purview/ome
NEW QUESTION 206
You have a Microsoft 365 subscription. You configure a Microsoft Purview insider risk management policy named Policy1. You need to ensure that you will receive real-time recommendations on how to configure the indicator thresholds for Policy1. The solution must ensure that the recommendations are based on a user’s activity from the past 10 days. What should you do first?
A. Create an Insider Risk Indicators connector.
B. Configure the Insider Risk Management Data sharing settings.
C. Create a data loss prevention (DLP) policy.
D. Enable insider risk management analytics.
Answer: D
Explanation:
To use real-time analytics (preview), you must enable insider risk analytics insights. After analytics is enabled, it can take 24 to 48 hours for insights and recommendations to appear.
https://learn.microsoft.com/en-us/purview/insider-risk-management-settings-policy-indicators
NEW QUESTION 207
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1. You need to deploy a Microsoft Purview insider risk management solution that will generate an alert when users share sensitive information on Site1 with external recipients. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Turn on analytics.
B. Turn on indicators.
C. Configure adaptive protection.
D. Create an insider risk policy.
E. Create a data loss prevention (DLP) policy.
Answer: BD
Explanation:
– Turning on indicators is required to enable the monitoring of user activities, such as file sharing and access to sensitive data, which are used by insider risk policies to evaluate risk.
– Creating an insider risk policy allows you to define risk scenarios, such as data leaks to external users, and trigger alerts when the policy conditions are met, including sensitive info sharing from SharePoint Online (Site1).
https://learn.microsoft.com/en-us/purview/insider-risk-management-settings-policy-indicators
NEW QUESTION 208
You have a Microsoft 365 E5 subscription that contains a user named User1. You deploy Microsoft Purview insider risk management. You need ensure that insider risk management events related to User1 are visible only to specific users. What should you create?
A. a detection group
B. a global exclusion
C. an indicator variant
D. a priority user group
Answer: D
Explanation:
To restrict management of Microsoft Purview Insider Risk Management events to specific users, you can utilize Priority User Groups and Administrative Units. Priority User Groups allow you to designate which users can view data related to specific users in Insider Risk Management, while Administrative Units enable you to scope user permissions to geographical areas or departments.
Priority User Groups (PUGs):
– Purpose:
PUGs allow you to create groups of users who are deemed high-risk and designate which users (e.g., investigators, analysts) can view data related to those high-risk users.
– How to use:
Create a PUG in the Insider Risk Management settings. When creating the PUG, you’ll designate which users (or Insider Risk Management role groups) can view data related to the users within that PUG. This ensures that only authorized personnel can access and manage alerts and cases associated with those high-risk users.
https://learn.microsoft.com/en-us/purview/insider-risk-management-users
NEW QUESTION 209
You have a Microsoft 365 subscription linked to a Microsoft Entra tenant that contains a user named User1. You need to grant User1 permission to search Microsoft 365 audit logs. The solution must use the principle of least privilege. Which role should you assign to User?
A. the Compliance Management role in the Exchange admin center
B. the Security Reader role in the Microsoft Entra admin center
C. the View-Only Audit Logs role in the Exchange admin center
D. the Reviewer role in the Microsoft Purview portal
Answer: C
NEW QUESTION 210
You have a Microsoft 365 E5 subscription. You plan to use insider risk management to collect and investigate forensic evidence. You need to enable forensic evidence capturing. What should you do first?
A. Configure the information protection scanner.
B. Claim capacity.
C. Enable Adaptive Protection.
D. Create priority user groups.
Answer: B
NEW QUESTION 211
You have a Microsoft 365 subscription. You create and run a content search from the Microsoft Purview portal. You need to download the results of the content search. What should you obtain first?
A. a certificate
B. a password
C. a pin
D. an export key
Answer: D
NEW QUESTION 212
You have a Microsoft 365 tenant that uses Microsoft Purview Message Encryption. You need to ensure that any emails containing attachments and sent to [email protected] are encrypted automatically by using Microsoft Purview Message Encryption. What should you do?
A. From the Exchange admin center, create a mail flow rule.
B. From the Exchange admin center, create a new sharing policy.
C. From the Microsoft Defender portal, create a Safe Attachments policy.
D. From the Microsoft Purview portal, configure an auto-apply retention label policy.
Answer: A
Explanation:
One way to enable Microsoft Purview Message Encryption is for Exchange Online and Exchange Online Protection administrators to define mail flow rules. These rules determine under what conditions email messages should be encrypted. When an encryption action is set for a rule, any messages that match the rule conditions are encrypted before they’re sent. Mail flow rules are flexible, letting you combine conditions so you can meet specific security requirements in a single rule. For example, you can create a rule to encrypt all messages that contain specified keywords and are addressed to external recipients. Microsoft Purview Message Encryption also encrypts replies from recipients of encrypted email.
https://learn.microsoft.com/en-us/purview/ome
NEW QUESTION 213
You have a data loss prevention (DLP) policy that applies to the Devices location. The policy protects documents that contain United States passport numbers. Users report that they cannot upload documents to a travel management website because of the policy. You need to ensure that the users can upload the documents to the travel management website. The solution must prevent the protected content from being uploaded to other locations. Which Microsoft 365 Endpoint data loss prevention (Endpoint DLP) setting should you configure?
A. Service domains.
B. Unallowed apps.
C. Unallowed browsers.
D. File path exclusions.
Answer: A
Explanation:
You can control whether sensitive files protected by your policies can be uploaded to specific service domains from Microsoft Edge.
– If the list mode is set to Block, then user will not be able to upload sensitive items to those domains. When an upload action is blocked because an item matches a DLP policy, DLP will either generate a warning or block the upload of the sensitive item.
– If the list mode is set to Allow, then users will be able to upload sensitive items only to those domains, and upload access to all other domains is not allowed.
https://docs.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-using
NEW QUESTION 214
You plan to implement Microsoft Purview Advanced Message Encryption. You need to ensure that encrypted email sent to external recipients expires after seven days. What should you create first?
A. a mail flow rule
B. an X.509 version 3 certificate
C. a custom branding template
D. a remote domain in Microsoft Exchange
E. a connector in Microsoft Exchange
Answer: C
Explanation:
You can use message expiration on emails that your users send to external recipients who use the OME Portal to access encrypted emails. You force recipients to use the OME portal to view and reply to encrypted emails sent by your organization by using a *custom branded template* that specifies an expiration date in PowerShell.
https://learn.microsoft.com/en-us/purview/ome-advanced-expiration
NEW QUESTION 215
You have a Microsoft 365 subscription that contains 100 users and a Microsoft 365 group named Group1. All users have Windows 11 devices and use Microsoft SharePoint Online and Exchange Online. A sensitivity label named Label1 is published as the default label for Group1. You add two sublabels named Sublabel1 and Sublabel2 to Label1. You need to ensure that the settings in Sublabel1 are applied by default to Group1. What should you do?
A. Modify the policy of Label1.
B. Duplicate all the settings from Sublabel1 to Label1.
C. Delete the policy of Label1 and publish Sublabel1.
D. Change the order of Sublabel1.
Answer: C
Explanation:
To ensure a sublabel is applied by default to a Microsoft 365 group when the parent label is the default, you must publish the desired sublabel and set it as the default for the group in the Microsoft Purview compliance portal, rather than trying to manipulate the parent label’s policy. The original parent label should not be set as the default for the group anymore, as sublabels override the parent’s default status.
https://learn.microsoft.com/en-us/purview/sensitivity-labels
NEW QUESTION 216
You have a Microsoft 365 E5 subscription. You plan to create an exact data match (EDM) classifier named EDM1. You need to grant permissions to hash and upload the sensitive information source table for EDM1. What should you create first?
A. a Microsoft 365 group named EDM_DataUploaders
B. a Microsoft Entra enterprise application named EDM_DataUploaders
C. a Microsoft Entra app registration named EDM_DataUploaders
D. a Microsoft Purview role group named EDM_DataUploaders
E. a security group named EDM_DataUploaders
Answer: C
Explanation:
When creating an Exact Data Match (EDM) classifier in Microsoft Purview, you must first hash and upload the sensitive information source table. This operation is performed using the EDM Upload Agent, which requires an app registration in Microsoft Entra ID (formerly Azure AD).
https://learn.microsoft.com/en-us/purview/sit-get-started-exact-data-match-hash-upload
NEW QUESTION 217
You have a Microsoft 365 E5 tenant that contains a user named User1. User1 is assigned the Compliance Administrator role. User1 cannot view the regular expression in the IP Address sensitive info type. You need to ensure that User1 can view the regular expression. What should you do?
A. Assign User1 the Global Reader role.
B. Assign User1 to the Reviewer role group.
C. Create a copy of the IP Address sensitive info type and instruct User1 to edit the copy.
D. Instruct User1 to use the Test function on the sensitive info type.
Answer: C
Explanation:
To allow a Compliance Administrator to view the IP Address sensitive info type’s regular expression, create a copy of the built-in “IP Address” sensitive info type in the Microsoft Purview compliance portal and grant the Compliance Administrator role access to that copied custom sensitive info type. You cannot directly edit built-in sensitive info types, but by copying it, you create a custom version that the administrator can then view and modify.
https://learn.microsoft.com/en-us/purview/sit-create-a-custom-sensitive-information-type
NEW QUESTION 218
You are creating a custom trainable classifier to identify organizational product codes referenced in Microsoft 365 content. You identify 300 files to use as seed content. Where should you store the seed content?
A. an Azure file share
B. a Microsoft OneDrive folder
C. a Microsoft SharePoint Online folder
D. a Microsoft Exchange Online shared mailbox
Answer: C
Explanation:
Seed content files for a custom trainable classifier should be stored in a SharePoint Online folder (or folders) that is dedicated to holding only that seed content. You’ll need to create a separate folder for positive examples and another for negative examples. After placing the files, make note of the full URL of the SharePoint site, library, and folder for each set of content.
https://learn.microsoft.com/en-us/purview/trainable-classifiers-get-started-with
NEW QUESTION 219
You have a Microsoft 365 E5 subscription. You have a Microsoft SharePoint Online document library that contains Microsoft Word and Excel documents. The documents contain the following types of information:
– Credit card numbers.
– Physical addresses in the UK.
– National health service numbers from the UK.
– Sensitive projects that contain the following words: Project Tailspin, Project Contoso, and Project Falcon.
You have email messages in Microsoft Exchange Online that contain the following information types:
– Credit card numbers.
– User sign-in credentials.
– National health service numbers from the UK.
You plan to use sensitive information types (SITs) for compliance policies. What is the minimum number of SITs required to classify all the information types?
A. 2
B. 5
C. 7
D. 10
Answer: B
Explanation:
https://learn.microsoft.com/en-us/purview/sit-sensitive-information-type-learn-about
NEW QUESTION 220
You have a Microsoft 365 E5 subscription. You need to create a Microsoft Defender for Cloud Apps policy that will detect data loss prevention (DLP) violations. What should you create?
A. an access policy
B. an activity policy
C. a file policy
D. a session policy
Answer: C
Explanation:
To create a Data Loss Prevention (DLP) policy in Microsoft Defender for Cloud Apps, go to the Microsoft Defender Portal, navigate to Cloud Apps –> Policies –> Policy management, and create a new File policy. Define the conditions by selecting a file filter and configuring the Data Classification Service for content inspection, then choose an Action for violations, such as creating an alert, and optionally, implementing a governance action like moving the file to quarantine. You can optionally set a policy severity, link it to risk types, and use sensitivity labels to ensure accurate file filtering.
https://learn.microsoft.com/en-us/training/modules/create-configure-data-loss-prevention-policies/3-integrate-data-loss-prevention-with-microsoft-cloud-app-security
NEW QUESTION 221
You have a Microsoft 365 E5 subscription that contains two Microsoft SharePoint Online sites named Site1 and Site2. You plan to configure a retention label named Label1 and apply Label1 to all the files in Site1. You need to ensure that two years after a file is created in Site1, the file moves automatically to Site2. How should you configure the Choose what happens after the retention period setting for Label1?
A. Deactivate retention settings.
B. Run a Power Automate flow.
C. Start a disposition review.
D. Change the label.
Answer: B
Explanation:
https://learn.microsoft.com/en-us/purview/retention-settings
NEW QUESTION 222
You have a Microsoft 365 E5 subscription. Users access their mailbox by using the following apps:
– Outlook for Microsoft 365.
– Outlook on the web.
– Outlook Mobile (IOS, Android).
You create a data loss prevention (DLP) policy named DLP1 that has the following settings:
– Location: Exchange email.
– Status: On.
– User notifications: On.
– Notify users with a policy tip: Enabled.
Which apps display a policy tip when content is matched by using DLP1?
A. Outlook for Microsoft 365 only.
B. Outlook on the web only.
C. Outlook for Microsoft 365 and Outlook on the web only.
D. Outlook for Microsoft 365 and Outlook Mobile (iOS, Android) only.
E. Outlook for Microsoft 365, Outlook on the web, and Outlook Mobile (iOS, Android).
Answer: C
Explanation:
https://support.microsoft.com/en-us/office/compare-outlook-for-pc-outlook-on-the-web-and-outlook-for-ios-android-b26a7bf5-0ac7-48ba-97af-984e0645dde5
NEW QUESTION 223
You have a Microsoft 365 E5 subscription. You need to apply data loss prevention (DLP) policies to the following:
– Microsoft Exchange Online mailboxes.
– Microsoft SharePoint Online sites.
– Microsoft Power BI workspaces.
– Microsoft OneDrive accounts.
– On-premises repositories.
What is the minimum number of DLP policies required to achieve the goal?
A. 1
B. 2
C. 3
D. 4
E. 5
Answer: B
NEW QUESTION 224
You have a Microsoft 365 E5 subscription. You plan to use Microsoft Purview insider risk management. You need to create an insider risk management policy that will detect data theft from Microsoft SharePoint Online by users that submitted their resignation or are near their employment termination date. What should you do first?
A. Configure Office indicators.
B. Onboard devices to Microsoft Defender for Endpoint.
C. Configure a Physical badging connector.
D. Configure a HR data connector.
Answer: D
Explanation:
To detect data theft from SharePoint Online by departing employees, create an insider risk management policy in Microsoft Purview, select the “Data theft by departing users” template, and add indicators for high-volume downloads or suspicious file activity from SharePoint. Configure the policy to trigger alerts based on these activities and integrate with a HR data connector to identify users near their termination date. To incorporate the HR Connector:
1. Set up the HR Connector: follow the steps to set up a connector in Purview, which involves creating an app registration in Entra ID, creating an app secret, and using a provided PowerShell script to import HR scenario data.
2. Import employee data: this script imports data from your HR system into the insider risk management solution, including information about employees who have submitted their resignations or are nearing their termination date.
https://learn.microsoft.com/en-us/purview/insider-risk-management-policies
NEW QUESTION 225
You have a Microsoft 365 E5 subscription that contains two users named User1 and Admin1. Admin1 manages audit retention policies for the subscription. You need to ensure that the audit logs of User1 will be retained for 10 years. What should you do first?
A. Assign a Microsoft Purview Audit (Premium) add-on license to Admin1.
B. Assign a 10-year audit log retention add-on license to Admin1.
C. Assign a Microsoft Purview Audit (Premium) add-on license to User1.
D. Assign a 10-year audit log retention add-on license to User1.
Answer: D
Explanation:
To retain a user’s Microsoft 365 audit logs for 10 years, you need the 10-Year Audit Log Retention add-on license, which must be assigned to that specific user in addition to an existing Microsoft 365 E5 license or Microsoft 365 E5 Compliance add-on license.
https://learn.microsoft.com/en-us/purview/audit-log-retention-policies
NEW QUESTION 226
You have a Microsoft 365 E5 subscription that contains a user named User1. All users are assigned Microsoft 365 Copilot licenses. You deploy Microsoft Purview Data Security Posture Management for AI (DSPM for Al). You need to ensure that User1 can analyze prompts and responses for AI interaction events. The solution must follow the principle of least privilege. To which two role groups should you add User1? (Each correct answer presents part of the solution. Choose two.)
A. Security Reader
B. Content Explorer List Viewer
C. Insider Risk Management Investigators
D. Information Protection Analysts
E. Content Explorer Content Viewer
Answer: AE
Explanation:
To view prompts and responses for AI interaction events in Microsoft Purview Data Security Posture Management for AI, a user must be assigned the Microsoft Purview Content Explorer Content Viewer role. This role provides the necessary permissions to drill down into activity explorer details and display the actual text of prompts and responses.
https://learn.microsoft.com/en-us/purview/ai-microsoft-purview-permissions
NEW QUESTION 227
HotSpot
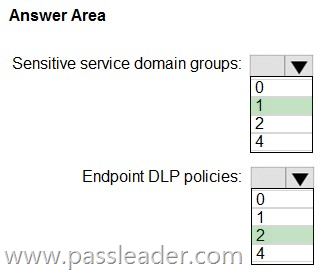
You have a Microsoft 365 E5 subscription. You need to implement Endpoint data loss prevention (Endpoint DLP) to meet the following requirements:
– Ensure that users can upload data to only two sites named Site1 and Site2.
– Prevent users from pasting data to two search engines named Search1 and Search2.
– Minimize the number of policies and groups.
What is the minimum number of sensitive service domain groups and Endpoint DLP policies required? (To answer, select the appropriate options in the answer area.)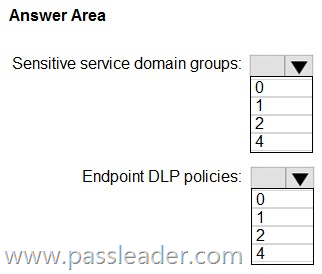
Explanation:
https://learn.microsoft.com/en-us/purview/endpoint-dlp-using
NEW QUESTION 228
HotSpot
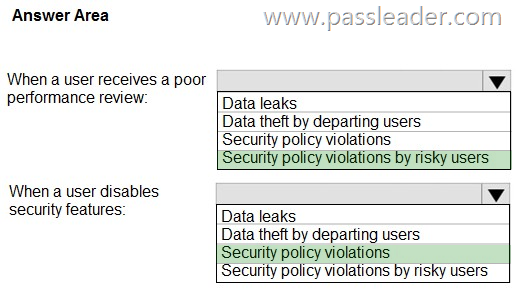
You have a Microsoft 365 E5 subscription. You plan to implement Microsoft Purview insider risk management. You need to recommend policy templates that meet the following requirements:
– Contain risk indicators and scoring for when a user receives a poor performance review.
– Contain risk indicators and scoring for when a user disables security features on a device.
Which template should you use for each requirement? (To answer, select the appropriate options in the answer area.)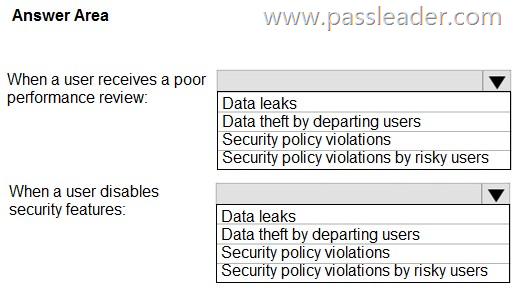
Explanation:
Box 1: Security policy violations by risky users. Contain risk indicators and scoring for when a user receives a poor performance review.
Box 2: Security policy violations. Contain risk indicators and scoring for when a user disables security features on a device.
https://learn.microsoft.com/en-us/purview/insider-risk-management-policy-templates
NEW QUESTION 229
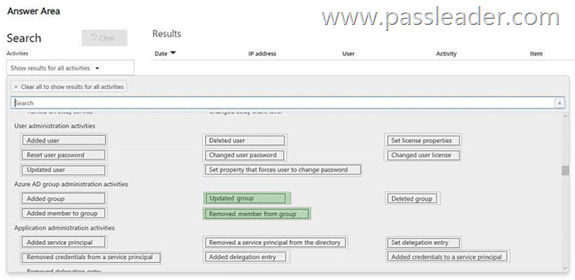
HotSpot
You have a Microsoft 365 subscription. Auditing is enabled. A user named User1 is a member of a dynamic security group named Group1. You discover that User1 is no longer a member of Group1. You need to search the audit log to identify why User1 was removed from Group1. Which two activities should you use in the search? (To answer, select the appropriate activities in the answer area.)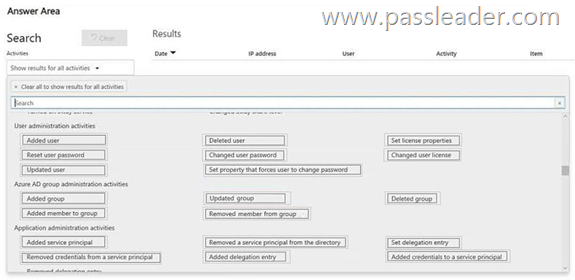
Explanation:
https://learn.microsoft.com/en-us/purview/audit-log-activities
NEW QUESTION 230
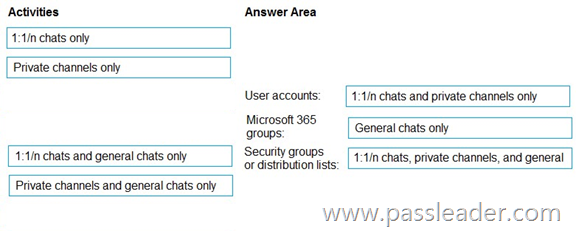
Drag and Drop
You have a Microsoft 365 E5 subscription. You need to prevent the sharing of sensitive information in Microsoft Teams. Which entities can you protect by applying a data loss prevention (DLP) policy to each resource? (To answer, drag the appropriate activities to the correct entity. Each activity may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)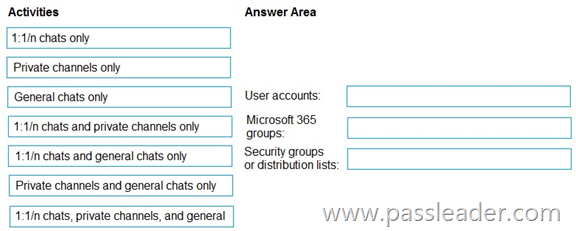
Explanation:
https://learn.microsoft.com/en-us/purview/dlp-microsoft-teams
NEW QUESTION 231
Drag and Drop
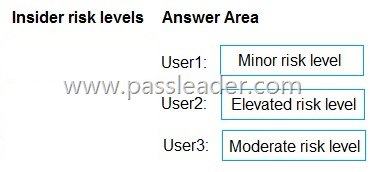
You have a Microsoft 365 5 subscription that uses Microsoft Purview insider risk management and contains three users named User1, User2, and User3. All insider risk management policies have adaptive protection enabled and the default conditions for insider risk levels configured. The users perform the following activities, which trigger insider risk policy alerts:
– User1 performs at least one data exfiltration activity that results in a high severity risk score.
– User2 performs at least three risky user activities within seven days, that each results in a high severity risk score.
– User3 performs at least two data exfiltration activities within seven days, that each results in a high severity risk score.
Which insider risk level is assigned to each user? (To answer, drag the appropriate levels to the correct users. Each level may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)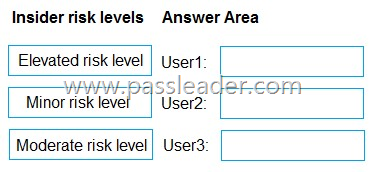
Explanation:
Box 1: Minor risk level. User1 performs at least one data exfiltration activity that results in a high severity risk score.
– Minor: this is the lowest risk level, assigned to users with low-severity alerts or those with at least one high-severity exfiltration activity.
Box 2: Elevated risk level. User2 performs at least three risky user activities within seven days, that each results in a high severity risk score.
– Elevated: this is the highest risk level, assigned to users with high-severity alerts, multiple high-severity insights, or confirmed high-severity alerts.
Box 3: Moderate risk level. User3 performs at least two data exfiltration activities within seven days, that each results in a high severity risk score.
– Moderate: this level indicates a medium risk, assigned to users with medium-severity alerts or those with at least two high-severity exfiltration activities.
https://learn.microsoft.com/en-us/purview/insider-risk-management-adaptive-protection
NEW QUESTION 232
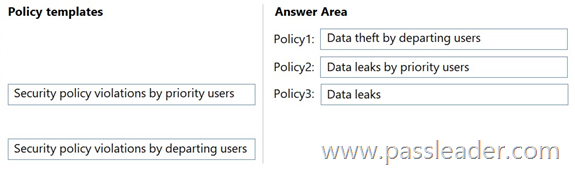
Drag and Drop
You have a Microsoft 365 E5 subscription. You need to create the Microsoft Purview insider risk management policies shown in the following table: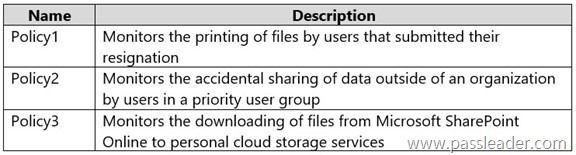
Which policy template should you use for each policy? (To answer, drag the appropriate policy templates to the correct policies. Each template may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)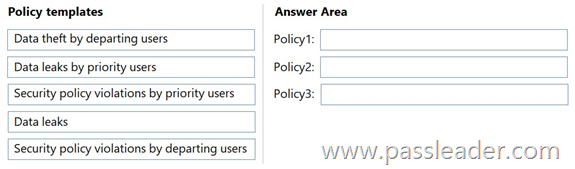
Explanation:
Box 1: Data theft by departing users.
– For Policy1: Monitors the printing of files by users that submitted their resignation. To monitor file printing by departing employees in Microsoft Purview, you should use the Data theft by departing users template and configure a Microsoft 365 HR connector for resignation dates, then add printing as a specific indicator. This template is designed to detect unusual activity from employees who are leaving, and adding the printing indicator will allow you to see specific printing actions in their activity.
Box 2: Data leaks by priority users.
– For Policy2: Monitors the accidental sharing of data of an organization by users in a priority user group. To detect accidental data sharing by users in a priority user group, you should use the Data leaks by priority users policy template in Microsoft Purview Insider Risk Management. This template is specifically designed to trigger alerts for data leak activities performed by members of a priority user group, making it the most appropriate choice for your scenario.
Box 3: Data leaks.
– For Policy2: Monitors the downloading of files from Microsoft SharePoint Online to personal cloud storage services. To monitor downloading files from SharePoint Online to personal cloud storage, you should use the Data leaks or Data leaks by priority users policy templates and then configure the policy to use Data Loss Prevention (DLP) indicators. You’ll need to create or select an existing DLP policy that identifies the sensitive data being downloaded and configure it to generate alerts for the insider risk management policy.
https://learn.microsoft.com/en-us/purview/insider-risk-management-policy-templates
NEW QUESTION 233
……
Get the newest PassLeader SC-401 VCE dumps here: https://www.passleader.com/sc-401.html (237 Q&As Dumps)
And, DOWNLOAD the newest PassLeader SC-401 PDF dumps from Cloud Storage for free: https://drive.google.com/drive/folders/13683SpK3sRCjLQqgxAcbbmi8fxAV-smt