Valid 70-243 Dumps shared by PassLeader for Helping Passing 70-243 Exam! PassLeader now offer the newest 70-243 VCE dumps and 70-243 PDF dumps, the PassLeader 70-243 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader 70-243 dumps with VCE and PDF here: http://www.passleader.com/70-243.html (185 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader 70-243 dumps from Cloud Storage: https://drive.google.com/open?id=0B-ob6L_QjGLpfmVaZDlXWUtVTTZVWWQ1Z3ZHdk1Gb0pBbWN4V2VOclZqcnFaUk5udTRUeGc
QUESTION 31
Note: This question is part of a series of questions that use the same set of answer choices. An answer choice may be correct for more than one question in the series.
Your network contains a System Center 2012 Configuration Manager environment. Your company develops a custom hardware device and installs the device on all of the client computers in the research department. You discover that information about the device fails to appear in any inventory queries or reports. Information about other hardware devices appears in the inventory queries and reports. You need to ensure that Configuration Manager data includes information about the custom hardware device. What should you do?
A. Enable a default WMI class in the Hardware Inventory Classes list.
B. Modify the Enable hardware inventory on clients setting.
C. Add a WMI class to the Hardware inventory Classes list.
D. Add a file name to the Software Inventory configuration.
E. Select Collect NOIDMIF files in Hardware Inventory.
F. Add a file name to the Hardware inventory configuration.
G. Add a file name to Software Metering.
H. Add a WMI class to the Sms_def.mof file.
I. Modify the Enable software inventory on clients setting.
Answer: C
Explanation:
Adding new device/class to hardware inventory:
– In the hardware inventory class window click the add button
– Next click the ‘Connect’ button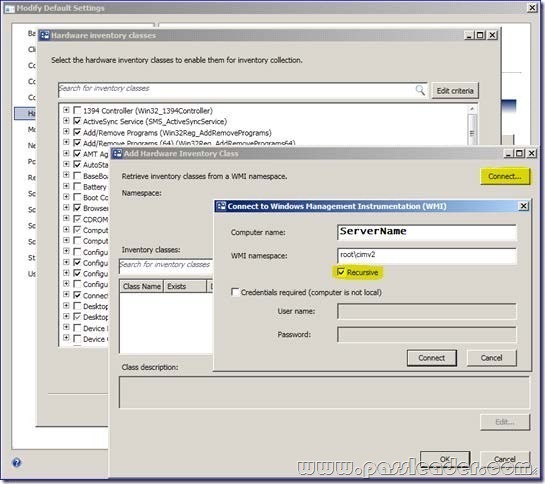
– Select the desired class and click ‘Edit’
– Give your new device/class a friendly name (instead of the default class name)
You can also set the unit size:
Now you can select the properties you want to add (as you did in the previous section).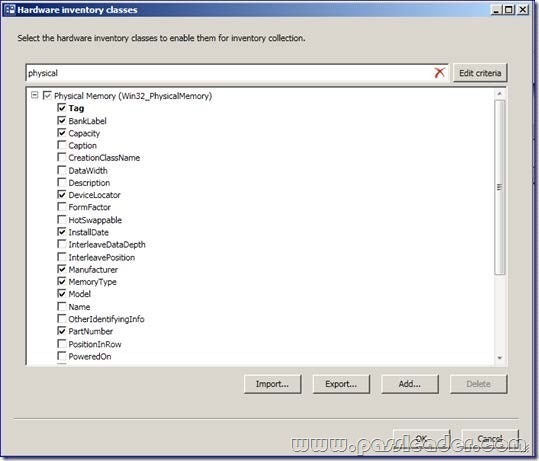
You can see the result in the resource explorer: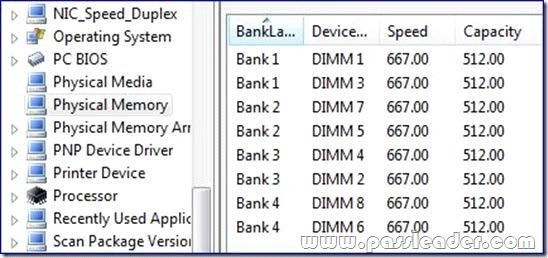
Hardware inventory works by querying Windows Management Instrumentation (WMI) for all data from certain WMI classes. WMI includes classes for operating system configuration and entities (such as user accounts), installed software, software configuration, and other objects (such as for the logged on user). These classes are supplements to hardware classes. Hardware inventory collects information about many things besides hardware. For example, it can inventory software by collecting details about programs listed in Add or Remove Programs in Control Panel or programs that have been installed using Windows Installer. Most of your inventory needs can be served by hardware inventory collection alone.
QUESTION 32
Note: This question is part of a series of questions that use the same set of answer choices. An answer choice may be correct for more than one question in the series. Your network contains a System Center 2012 Configuration Manager environment. Your company deploys a custom Application to 2,000 client computers by using Configuration Manager. The Application is not listed in Add Remove Programs. You discover that information about the Application fails to appear in the inventory queries and inventory reports. You verify that information about other Applications appear in the inventory reports. You need to ensure that Configuration Manager data includes installation information about the custom Application. What should you do?
A. Add a file name to Software Metering
B. Add a WMI class to the Hardware Inventory Classes fat
C. Add a file name to the Hardware Inventory configuration
D. Enable a default WMI Cass in the Hardware Inventory Classes list
E. Select Collect NOIDMIF files .n Hardware Inventory
F. Add a file name to the Software Inventory configuration
G. Modify the Enable hardware inventory on Cents setting
H. Add a WMI class to the Sms_def.mof file
Answer: F
Explanation:
http://technet.microsoft.com/en-us/library/cc180952.aspx#EBAA
QUESTION 33
Note: This question is part of a series of questions that use the same set of answer choices. An answer choice may be correct for more than one question in the series. Your network contains a System Center 2012 Configuration Manager environment. Your company deploys a third-party Application to 10,000 client computers. You need to ensure that you can run a report that lists all of the client computers that ran the Application last month. What should you do?
A. Modify the Enable hardware inventory on clients setting.
B. Enable a default WMI class in the Hardware Inventory Classes list.
C. Modify the Enable software inventory on clients setting.
D. Add a file name to the Hardware Inventory configuration.
E. Add a WMI class to the Hardware Inventory Classes list.
F. Add a file name to the Software Inventory configuration.
G. Add a file name to Software Metering.
H. Add a WMI class to the Sms_def.mof file.
I. Select Collect NOIDMIF files in Hardware Inventory.
Answer: G
Explanation:
http://technet.microsoft.com/en-us/library/gg682005.aspx
Introduction to Software Metering in Configuration Manager.
Use software metering in System Center 2012 Configuration Manager to monitor and collect software usage data from Configuration Manager clients. To collect this usage data, configure software metering rules or use the Configuration Manager inventory to generate these rules automatically. Client computers evaluate these rules and collect metering data to send to the site.
QUESTION 34
Your network contains a System Center 2012 Configuration Manager environment. You need to create a report that lists all of the client computers that do not have an Application named App1 instated. Which query should you use to create the report?
A. SELECT SYS.Netbios_Name0, ARP.DisplayName0
FROM v_R_System AS SYS INNER JOIN
v_GS_ADD_REMOVE_PROGRAMS AS ARP ON SYS.ResourceID = ARP.
ResourceID WHERE ARP.DisplayName0 NOT IN (‘App1’)
B. SELECT SYS.Netbios_Name0 from v_R_System SYS
WHERE SYS.ResourceID IN
(SELECT SYS.ResourceID
FROM v_R_System AS SYS INNER JOIN
v_GS_ADD_REMOVE_PROGRAMS AS ARP ON SYS.ResourceID = ARP.
ResourceID. WHERE ARP.
DisplayName0 = ‘App1’)
C. SELECT SYS.Netbios_Name0 from v_R_System SYS
WHERE SYS.ResourceID NOT IN
(SELECT SYS.ResourceID
FROM v_R_System AS SYS INNER JOIN
v_GS_ADD_REMOVE_PROGRAMS AS ARP ON SYS.ResourceID = ARP.
ResourceID WHERE ARP.
DisplayName0 = ‘App1’)
D. SELECT SYS.Netbios_Name0, ARP.DisplayName0
FROM v_R_System AS SYS INNER JOIN
V_GS_ADD_REMOVE_PROGRAMS AS ARP ON SYS.ResourceID = ARP.
ResourceID WHERE ARP.
DisplayName0 NOT LIKE ‘App1’
Answer: C
Explanation:
http://www.w3schools.com/sql/sql_join_inner.asp
QUESTION 35
Network contains a System Center 2012 Configuration Manager environment. You have the following query:
Select
R.Name
U.UserName
from
SMS_R_System R
join SMS_R_User U
on R.LastLogonUserName = U.UserName
You need to ensure that all of the client computers are listed in the query results. Which join type should you use?
A. LEFT
B. FULL
C. INNER
D. RIGHT
Answer: A
Explanation:
http://www.w3schools.com/sql/sql_join_left.asp
SQL LEFT JOIN Keyword. The LEFT JOIN keyword returns all rows from the left table (table_name1), even if there are no matches in the right table (table_name2).
Further information:
http://www.w3schools.com/sql/sql_join_full.asp
SQL FULL JOIN Keyword. The FULL JOIN keyword return rows when there is a match in one of the tables.
http://www.w3schools.com/sql/sql_join_inner.asp
SQL INNER JOIN Keyword. The INNER JOIN keyword returns rows when there is at least one match in both tables.
http://www.w3schools.com/sql/sql_join_right.asp
SQL RIGHT JOIN Keyword. The RIGHT JOIN keyword returns all the rows from the right table (table_name2), even if there are no matches in the left table (table_name1).
QUESTION 36
You have a System Center 2012 Configuration Manager environment. You use Active Directory System Discovery to discover computers that are located in the Sales organizational unit (OU) and in all child OUs under the Sales OU. Discovering computers in all the child OUs is requiring a significant amount of time to complete. You need to configure discovery for only computers in the Sales OU. What should you do?
A. Clear the Recursive check box for the Sales OU discovery.
B. Clear the Include Groups check box for the Sales OU discovery.
C. Create a custom LDAP query to LDAP://OU=Sales,DC=SCCMDEMO,DC=COM.
Select the Recursive check box.
D. Select the option to browse to the Sales OU, and then select the Sales OU.
Select the Recursive check box.
Answer: A
QUESTION 37
You have a System Center 2012 Configuration Manager environment. You need to install the Configuration Manager client software by using a logon script. What should you configure the logon script to run?
A. CCMSetup.exe
B. CCMSetup.msi
C. Capinst.exe
D. Client.msi
Answer: A
QUESTION 38
You have a System Center 2012 Configuration Manager environment running in native mode. You have a perimeter network for your Internet-based site systems. You block the SMB traffic from the perimeter network to your intranet. You configure the site systemsproperties to allow only site server initiated data transfers from the site systems. You need to configure site system communications between the perimeter network and the site server. What should you do?
A. Configure the fallback status points.
B. Configure a server locator point.
C. Configure a Client Connection account.
D. Configure a Site System Installation account.
Answer: D
QUESTION 39
You have a System Center 2012 Configuration Manager environment. You deploy Microsoft Office 2007 to client computers in a collection named Coll1. You run the Configuration Manager Web report for Add or Remove Programs, and you query for Office 2007. No computers are found to have Office 2007 installed. You need to identify computers that have Office 2007 installed. What should you do?
A. Configure software inventory to run daily.
B. Configure hardware inventory to run daily.
C. Configure Coll1 to update membership daily.
D. Configure Coll1 to have a collection-specific polling interval.
Answer: B
QUESTION 40
You have a System Center 2012 Configuration Manager environment. You want to create a new package for an application. In the Configuration Manager console, you right-click the Packages node. You do not see the option to create a new package. You need to be able to create packages. What should you do?
A. Request Package Class Create rights for your user account.
B. Request Package Instance Create rights for your user account.
C. Request Package Instance Class Modify rights for your user account.
D. Request that your user account be added to the SMS Admins local group on the site server.
Answer: A
QUESTION 41
You have a System Center 2012 Configuration Manager environment. You need to view the installation progress of an advertisement from a client computer. Which log file should you view?
A. policyevaluator.log
B. ccmexec.log
C. execmgr.log
D. offermgr.log
Answer: C
QUESTION 42
Your network contains a System Center 2012 Configuration Manager environment. You write the following query:
select SYS.Name from SMS_R_System SYS
join SMS_G_Syatem_ADD_REMOVE_PROGRAMS ARP
on ARP.ResourceId = SYS.ResourceId
You need to create a list of all the client computers that have a version of Visual Studio installed. What should you add to the query?
A. where ARP.DisplayName like “Visual Studio*”
B. where ARP.DisplayName = “*Visual Studio*”
C. where ARP.DisplayNarae = “%%Visual Studio”
D. where ARP.DisplayName like “Visual studio%”
Answer: D
Explanation:
You need to use “Like” not “=” otherwise the WildCard “%” is seen as a real identifier. Better to use % compared to *. With % you would only get different versions of Visual Studio and not other applications with names starting with Visual Studio.
QUESTION 43
Your network contains a System Center 2012 Configuration Manager environment. You need to receive an email message every day that lists all non-compliant clients. What should you do?
A. Create an alert subscription.
B. Configure a Microsoft SQL Server Reporting Services (SSRS) report.
C. Configure an in-console alert.
D. Create a ConfigMgr query.
Answer: B
Explanation:
Configure report subscription is with the same procedure as standard SQL report service.
http://be.enhansoft.com/post/2013/08/14/How-to-Set-up-an-Email-Subscription-in-SSRS.aspx
QUESTION 44
Note: This question is part of a series of questions that use the same set of answer choices. An answer choice may be correct for more than one question in the series.
Your network contains a System Center 2012 Configuration Manager environment as shown in the exhibit. (Click the Exhibit button.)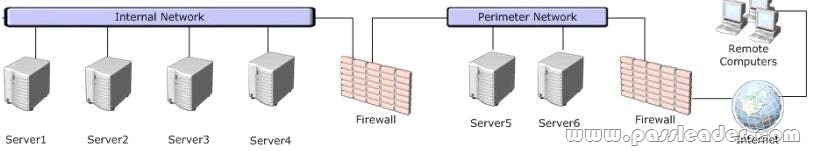
The network contains six servers. The servers are configured as shown in the following table.
You plan to deploy servers to the perimeter network by using Configuration Manager. The operating system for each server will be instated over the network. The installations will begin automatically, as soon as each server starts for the first time. You need to recommend a solution to minimize the amount of network traffic between the perimeter network and the internal network during the installation of the operating systems. What should you do?
A. Install a software update point on Server3.
B. Configure IIS to support only HTTP on Server3.
C. Install a PXE-enabled protected distribution point on Server5.
D. Install a management point on Server5.
E. Install Windows Server Update Services (WSUS) on Server3.
F. Install Network Load Balancing (NLB) on Server6.
G. Install the Windows Cluster service on Server6.
H. Install a PXE-enabled protected distribution point on Server4.
I. Install a management point on Server2.
J. Install a protected distribution point on Server1.
K. Install the Windows Cluster service on Server3.
L. Install Network Load Balancing (NLB) on Server3.
M. Configure the Exchange connector on Server3.
N. Configure IIS to support only HTTPS on Server5.
O. Install an enrollment proxy point on Server6.
Answer: C
Explanation:
Administration, Site config, Servers and Site System Roles, DP role, properties, PXE tab.

Topology Sample: http://technet.microsoft.com/en-us/library/bb633059.aspx
QUESTION 45
Note: This question is part of a series of questions that use the same set of answer choices. An answer choice may be correct for more than one question in the series.
Your network contains a System Center 2012 Configuration Manager environment as shown in the exhibit. (Click the Exhibit button.)
The network contains six servers. The servers are configured as shown in the following table.
A corporate security policy states that remote computers are forbidden to communicate directly with servers on the internal network. You need to ensure that you collect inventory data from the remote computers. What should you do?
A. Install Windows Server Update Serves (WSUS) on Server3.
B. Configure the Exchange connector on Server3.
C. Install a management point on Server2.
D. Install a PXE-enabled protected distribution point on Servers.
E. Install a software update point on Server3.
F. Install Network Load Balancing (NLB) on Server6.
G. Install an enrollment proxy point on Server6.
H. Install the Windows Cluster service on Server3.
I. Install a protected distribution point on Server1.
J. Configure IIS to support only HTTPS on Servers.
K. Install a management point on Server5.
L. Install the Windows Cluster service on Server6.
M. Configure IIS to support only HTTP on Servers.
N. Install Network Load Balancing (NLB) on Server3.
O. Install a PXE-enabled protected distribution point on Server4.
Answer: K
Explanation:
http://technet.microsoft.com/en-us/library/gg712701.aspx
Planning for Communications in Configuration Manager.
Planning for Communications Across Forests in Configuration Manager.
Note: Two exceptions are the out of band service point and the Application Catalog web service point. Each must be installed in the same forest as the site server. When the site system role accepts connections from the Internet, as a security best practice, install these site system roles in an untrusted forest (for example, in a perimeter network) so that the forest boundary provides protection for the site server. When you specify a computer to be a site system server, you must specify the Site System Installation Account. This account must have local administrative credentials to connect to, and then install site system roles on the specified computer. When you install a site system role in an untrusted forest, you must select the site system option Require the site server to initiate connections to this site system. This configuration enables the site server to establish connections to the site system server to transfer data. This prevents the site system server that is in the untrusted location from initiating contact with the site server that is inside your trusted network. These connections use the Site System Installation Account that you use to install the site system server. The management point and enrollment point site system roles connect to the site database. By default, when these site system roles are installed, Configuration Manager configures the computer account of the new site system server as the connection account and adds the account to the appropriate SQL Server database role. When you install these site system roles in an untrusted domain, you must configure the site system role connection account to enable the site system role to obtain information from the database. If you configure a domain user account for these connection accounts, ensure that the account has appropriate access to the SQL Server database at that site:
* Management point: Management Point Database Connection Account
* Enrollment point: Enrollment Point Connection Account
Consider the following additional information when you plan for site system roles in other forests:
* If you run a Windows Firewall, configure the applicable firewall profiles to pass communications between the site database server and computers that are installed with remote site system roles.
* When the Internet-based management point trusts the forest that contains the user accounts, user policies are supported. When no trust exists, only computer policies are supported.
Get the newest PassLeader 70-243 VCE dumps here: http://www.passleader.com/70-243.html (185 Q&As Dumps)
And, DOWNLOAD the newest PassLeader 70-243 PDF dumps from Cloud Storage for free: https://drive.google.com/open?id=0B-ob6L_QjGLpfmVaZDlXWUtVTTZVWWQ1Z3ZHdk1Gb0pBbWN4V2VOclZqcnFaUk5udTRUeGc