Valid 70-410 Dumps shared by PassLeader for Helping Passing 70-410 Exam! PassLeader now offer the newest 70-410 VCE dumps and 70-410 PDF dumps, the PassLeader 70-410 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader 70-410 dumps with VCE and PDF here: http://www.passleader.com/70-410.html (512 Q&As Dumps –> 528 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader 70-410 dumps from Cloud Storage: https://drive.google.com/open?id=0B-ob6L_QjGLpfnJzOE1fWnlJOWVtaE93SnJNT3gtaTNYYnVpZkw5THBSMWRKbFlfaXh1azg
QUESTION 321
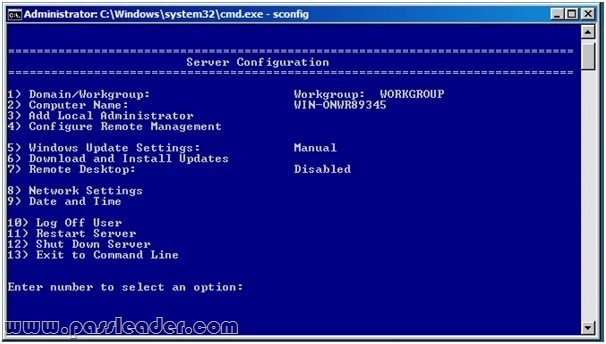
You have one server named Server1. Server1 runs a Server Core installation of Windows Server 2012 R2. The local area connection on Server1 has the following configuration:
– IP address: 10.1.1.1
– Subnet mask: 255.255.240.0
– Default gateway: 10.1.1.254
– Preferred DNS server: <none>
The network contains a DNS server that has an IPv4 address of 10.1.1.200. You need to configure Server1 to use 10.1.1.200 as the preferred DNS server. The solution must not change any other settings on Server1. Which command should you run?
A. sconfig.cmd
B. net.exe
C. Set-NetIPInterface
D. netsh.exe
Answer: A
Explanation:
In Windows Server 2012 R2, you can use the Server Configuration tool (Sconfig.cmd) to configure and manage several common aspects of Server Core installations. Network settings You can configure the IP address to be assigned automatically by a DHCP Server or you can assign a static IP address manually. This option allows you to configure DNS Server settings for the server as well. Sconfig.cmd interface:
QUESTION 322
You have a server named Server1 that runs Windows Server 2012 R2. On Server1, you open Computer Management as shown in the exhibit. (Click the Exhibit button.)

You need to ensure that you can create a 3-TB volume on Disk 1. What should you do first?
A. Create a storage pool.
B. Convert the disk to a GPT disk.
C. Create a VHD, and then attach the VHD.
D. Convert the disk to a dynamic disk.
Answer: B
Explanation:
The exhibit shows Disk1 to be a basic disk. The disk must be GPT since GPT disks allows for partitioning.
http://msdn.microsoft.com/en-us/library/windows/hardware/gg463525.aspx
QUESTION 323
You work as an administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers in the contoso.com domain, including domain controllers, have Windows Server 2012 R2 installed. contoso.com has a domain controller, named L2P-DC01. You have been instructed to make sure that the Group Policy Administrative Templates are available centrally. Which of the following actions should you take?
A. You should consider copying the policies folder to the PolicyDefinitions folder in the contoso.com domain’s SYSVOL folder.
B. You should consider copying the PolicyDefinitions folder to the policies folder in the contoso.com domain’s SYSVOL folder.
C. You should consider copying the PolicyDefinitions folder to the policies folder in the contoso.com domain’s systemroot folder.
D. You should consider copying the PolicyDefinitions folder to the policies folder in the contoso.com domain’s logonserver folder.
Answer: B
Explanation:
PolicyDefinitions folder within the SYSVOL folder hierarchy. By placing the ADMX files in this directory, they are replicated to every DC in the domain; by extension, the ADMX-aware Group Policy Management Console in Windows Vista, Windows 7, Windows Server 2008 and R2 can check this folder as an additional source of ADMX files, and will report them accordingly when setting your policies. By default, the folder is not created. Whether you are a single DC or several thousand, I would strongly recommend you create a Central Store and start using it for all your ADMX file storage. It really does work well. The Central Store To take advantage of the benefits of .admx files, you must create a Central Store in the SYSVOL folder on a domain controller. The Central Store is a file location that is checked by the Group Policy tools. The Group Policy tools use any .admx files that are in the Central Store. The files that are in the Central Store are later replicated to all domain controllers in the domain. To create a Central Store for .admx and .adml files, create a folder that is named PolicyDefinitions in the following location: \\FQDN\SYSVOL\FQDN\policies.
Note: FQDN is a fully qualified domain name.
http://tigermatt.wordpress.com/tag/policydefinitions/
http://support.microsoft.com/kb/929841/en-us
http://www.virtuallyimpossible.co.uk/how-to-create-a-group-policy-central-store/
http://support.microsoft.com/kb/2741591/en-us
QUESTION 324
Your network contains an Active Directory domain named contoso.com. The password policy for the domain is set to require a minimum password length of 10 characters. A user named User1 and a user named User2 work for the sales department. User1 is forced to create a domain password that has a minimum of 12 characters. User2 is forced to create a domain password that has a minimum of eight characters. You need to identify what forces the two users to have different password lengths. Which tool should you use?
A. Credential Manager
B. Security Configuration Wizard (SCW)
C. Group Policy Management
D. Active Directory Administrative Center
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/cc770842(v=ws.10).aspx
In Windows Server 2008, you can use fine-grained password policies to specify multiple password policies and apply different password restrictions and account lockout policies to different sets of users within a single domain. For example, to increase the security of privileged accounts, you can apply stricter settings to the privileged accounts and then apply less strict settings to the accounts of other users. Or in some cases, you may want to apply a special password policy for accounts whose passwords are synchronized with other data sources.


QUESTION 325
You work as an administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers in the contoso.com domain, including domain controllers, have Windows Server 2012 R2 installed. contoso.com has a Hyper-V server, named PL-SR13, which hosts multiple virtual machines. You have enabled the use of Single-root I/O virtualization. Which of the following is TRUE with regards to using Single-root I/O virtualization? (Choose all that apply.)
A. It maximizes network throughput, while minimizing network latency.
B. It maximizes network throughput, as well as network latency.
C. It avoids the virtual switch stack and allows the virtual machine direct access to the actual network switch.
D. It prevents the virtual machine from accessing the network switch directly.
Answer: AC
Explanation:
http://msdn.microsoft.com/en-us/library/windows/hardware/hh440148%28v=vs.85%29.aspx
QUESTION 326
You work as a senior administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers on the contoso.com network have Windows Server 2012 R2 installed. You are running a training exercise for junior administrators. You are currently discussing the use of Non-Uniform Memory Architecture (NUMA). Which of the following is TRUE with regards to Non-Uniform Memory Architecture (NUMA)? (Choose two.)
A. It is a computer architecture used in multiprocessor systems.
B. It is a computer architecture used in single processor systems.
C. It allows a processor to access local memory faster than it can access remote memory.
D. It allows a processor to access remote memory faster than it can access local memory.
Answer: AC
Explanation:
http://en.wikipedia.org/wiki/Non-Uniform_Memory_Access
http://www.aidanfinn.com/?p=11945
QUESTION 327
Hotspot Question
You have a server named DHCP1 that runs Windows Server 2012 R2. DHCP1 does not ave access to the Internet. All roles are removed completely from DHCP1. You mount a Windows Server 2012 R2 installation image to the C:\Mount folder. You need to install the DHCP Server server role on DHCP1 by using Server Manager. Which folder should you specify as the alternate path for the source files? To answer, select the appropriate folder in the answer area.

QUESTION 328
You have a server named Data1 that runs a Server Core Installation of Windows Server 2012 R2 Standard. You need to configure Data1 to run a Server Core Installation of Windows Server 2012 R2 Enterprise. You want to achieve this goal by using the minimum amount of administrative effort. What should you perform?
A. a clean installation of Windows Server 2012
B. an offline servicing by using Dism
C. an online servicing by using Dism
D. an upgrade installation of Windows Server 2012
Answer: C
Explanation:
http://technet.microsoft.com/en-us/library/hh825157.aspx
QUESTION 329
You have a server named Server1 that runs Windows Server 2012 R2. You need to enable access-based enumeration for a file share on Server1. Which tool should you use?
A. File Server Resource Manager (FSRM)
B. File Explorer
C. Share and Storage Management
D. Server Manager
Answer: D
Explanation:
Windows 2008 use Share and Storage Management and Windows 2012 use Server Manager.
QUESTION 330
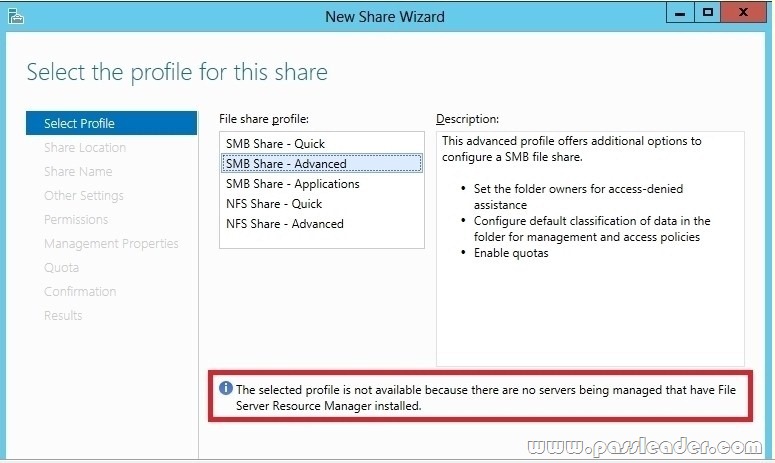
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1. Server1 runs Windows Server 2012 R2. You plan to create a shared folder. The shared folder will have a quota limit. You discover that when you run the New Share Wizard, you cannot select the SMB Share — Advanced option. You need to ensure that you can use SMB Share – Advanced to create the new share. What should you do on Server1 before you run the New Share Wizard?
A. Run the Set-SmbSharecmdlet.
B. Install the File Server Resource Manager role service.
C. Configure Dynamic Access Control and Apply a central access policy.
D. Configure the Advanced system settings.
QUESTION 331
Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2. A server named Server1 is configured to encrypt all traffic by using IPSec. You need to ensure that Server1 can respond to ping requests from computers that do not support IPSec. What should you do?
A. From a command prompt, run netsh set global autotuninglevel = restricted congestionprovider = ctcp.
B. From Windows Firewall with Advanced Security, exempt ICMP from IPSec.
C. From a command prompt, run netsh set global autotuninglevel highlyrestrictedcongestionprovider = none.
D. From Windows Firewall with Advanced Security, allow unicast responses for the Domain Profile.
QUESTION 332
Hotspot Question
Your network contains an Active Directory domain. The domain contains a server named Server28. The computer account of Server 28 is located in an organizational unit (OU) named OU1. A Group Policy Object (GPO) named Application Restriction Policy is linked to OU1. The settings of the GPO are configured as shown in the GPO Settings exhibit. (Click the Exhibit button.)

The Services console on Server28 is shown in the Services exhibit. (Click the Exhibit button.)

Select Yes if the statement can be shown to be true based on the available information; otherwise select No. Each correct selection is worth one point.

QUESTION 333
Drag and Drop Question
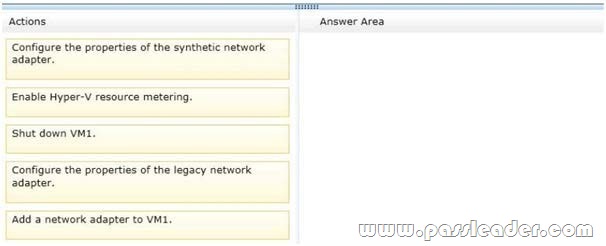
You have a Hyper-V host named Server1. Server1 hosts a virtual machine named VM1. You view the properties of VM1 as shown in the following exhibit. (Click the Exhibit button.)

You need to configure bandwidth management for VM1. Which three actions should you perform in sequence? (To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.)
QUESTION 334
You plan to deploy a file server to a temporary location. The temporary location experiences intermittent power failures. The file server will contain a dedicated volume for shared folders. You need to create a volume for the shared folders. The solution must minimize the likelihood of file corruption if a power failure occurs. Which file system should you use?
A. ReFS
B. NFS
C. NTFS
D. FAT32
Answer: A
Explanation:
The ReFS file system allows for resiliency against corruptions with the option to salvage amongst many other key features like Metadata integrity with checksums, Integrity streams with optional user data integrity, and shared storage pools across machines for additional failure tolerance and load balancing, etc.
QUESTION 335
Your company has a main office and four branch offices. The main office contains a server named Server1 that runs Windows Server 2012 R2. The IP configuration of each office is configured as shown in the following table.

You need to add a single static route on Server1 to ensure that Server1 can communicate with the hosts on all of the subnets. Which command should you run?
A. route.exe add -p 10.10.0.0 mask 255.255.252.0 10.10.0.1
B. route.exe add -p 172.16.16.0 mask 255.255.252.0 10.10.0.1
C. route.exe add -p 10.10.0.0 mask 255.255.252.0 172.16.0.0
D. route.exe add -p 172.16.18.0 mask 255.255.252.0 10.10.0.1
Answer: B
Explanation:
These parameters will allow communication with all the hosts.

QUESTION 336
You work as a senior administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers on the contoso.com network have Windows Server 2012 R2 installed. You are running a training exercise for junior administrators. You are currently discussing what happens when you run the Remove-NetLbfoTeam Windows PowerShell cmdlet. Which of the following describes the results of running this cmdlet?
A. It removes one or more network adapters from a specified NIC team.
B. It removes a team interface from a NIC team.
C. It removes a specified NIC team from the host.
D. It removes a network adapter member from a switch team.
Answer: C
Explanation:
The Remove-NetLbfoTeam cmdlet removes the specified NIC team from the host. This cmdlet disconnects all associated team members and providers from the team. You can specify the team to remove by using either a team object retrieved by Get-NetLbfoTeam, or by specifying a team name. You can use Remove-NetLbfoTeam to remove all NIC teams from the server. You need administrator privileges to use Remove-NetLbfoTeam.
http://technet.microsoft.com/en-us/library/jj130848%28v=wps.620%29.aspx
QUESTION 337
You work as a senior administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers in the contoso.com domain, including domain controllers, have Windows Server 2012 R2 installed. You are running a training exercise for junior administrators. You are currently discussing the Virtual Fibre Channel SAN feature. Which of the following is TRUE with regards to the Virtual Fibre Channel SAN feature? (Choose all that apply.)
A. It prevents virtual machines from connecting directly to Fibre Channel storage.
B. It allows for virtual machines to connect to Fibre Channel storage directly.
C. It includes support for virtual SANs, live migration, and multipath I/O.
D. It includes support for virtual SANs, and live migration, but not multipath I/O.
Answer: BC
Explanation:
http://technet.microsoft.com/en-us/library/hh831413.aspx
http://www.brocade.com/downloads/documents/technical_briefs/virtual-fibre-channel-hyperv-tb.pdf
QUESTION 338
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. On a server named Server2, you perform a Server Core Installation of Windows Server 2012 R2. You join Server2 to the contoso.com domain. You need to ensure that you can manage Server2 by using the Computer Management console on Server1. What should you do on Server2?
A. Install Remote Server Administration Tools (RSAT).
B. Install Windows Management Framework.
C. Run sconfig.exe and configure remote management.
D. Run sconfig.exe and configure Remote Server Administration Tools (RSAT).
Answer: C
Explanation:
In Windows Server 2012 R2, you can use the Server Configuration tool (Sconfig.cmd) to configure and manage several common aspects of Server Core installations. You must be a member of the Administrators group to use the tool. Sconfig.cmd is available in the Minimal Server Interface and in Server with a GUI mode.

QUESTION 339
You work as an administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers in the contoso.com domain, including domain controllers, have Windows Server 2012 R2 installed. When you recently added new workstations to the contoso.com manually, you found that that the computer accounts were created in the default container. You want to make sure that the default container for newly created computers is redirected to a specified, target organizational unit (OU). Which of the following actions should you take?
A. You should consider making use of the replace.exe command-line tool.
B. You should consider making use of the redircmp.exe command-line tool.
C. You should consider making use of the redirusr.exe command-line tool.
D. You should consider making use of the rexec.exe command-line tool.
Answer: B
Explanation:
http://technet.microsoft.com/pt-pt/library/cc770619%28v=ws.10%29.aspx
http://support.microsoft.com/kb/324949/en-us
http://support.microsoft.com/kb/555573/en-us
QUESTION 340
You work as an administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. contoso.com has a Windows Server 2012 R2 domain controller, named L2P-DC01, which has the Domain Naming master and the Schema master roles installed. contoso.com also has a Windows Server 2008 R2 domain controller, named L2P-DC02, which has the PDC Emulator, RID master, and Infrastructure master roles installed. You have deployed a new Windows Server 2012 server, which belongs to a workgroup, in contoso.com’s perimeter network. You then executed the djoin.exe command. Which of the following is the purpose of the djoin.exe command?
A. It sets up a computer account in a domain and requests an offline domain join when a computer restarts.
B. It sets up a user account in a domain and requests an online domain join when a computer restarts.
C. It sets up a computer account in a domain and requests an offline domain join immediately.
D. It sets up a computer account in a domain and requests an online domain join immediately.
Answer: A
Explanation:
http://technet.microsoft.com/en-us/library/offline-domain-join-djoin-step-by-step%28v=ws.10%29.aspx
QUESTION 341
You work as an administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers in the contoso.com domain have Windows Server 2012 R2 installed, while domain controllers have Windows Server 2008 R2 installed. You are then tasked with deploying a new Windows Server 2012 R2 domain controller. You are preparing to install the DNS Server role, and enable the global catalog server option. Which of the following actions should you take?
A. You should consider making use of Server Manager.
B. You should consider making use of the Active Directory Installation Wizard.
C. You should consider making use of the DHCP Installation Wizard.
D. You should consider making use of TS Manager.
Answer: A
Explanation:


http://kpytko.pl/2012/09/07/adding-first-windows-server-2012-domain-controller-within-windows-200320082008r2-network/
http://www.msserverpro.com/migrating-active-directory-domain-controller-from-windows-server-2008-r2-to-windows-server-2012/
QUESTION 342
You work as an administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. all servers in the contoso.com domain has Windows Server 2012 R2 nstalled. You have logged on to a server, named PL-SR07, and would like to obtain the IP configurations of a server, named PL-SR13. Which of the following actions should you take?
A. You should consider making use of the Winrs.exe command.
B. You should consider making use of the Winsat.exe command.
C. You should consider making use of the Winpop.exe command.
D. You should consider making use of the Dsrm.exe command.
Answer: A
Explanation:
Windows Remote Management allows you to manage and execute programs remotely. You can use WinRS to administer a Server Core installation remotely from the command line. WinRS is a command-line tool included in both Windows Vista and the Full installation of Windows Server 2008, which relies on Windows Remote Management (WinRM) to execute remote commands, especially for headless servers. WinRM is Microsoft’s implementation of the WS-Management protocol, a standard Simple Object Access Protocol (SOAP)-based, firewall-friendly protocol that enables hardware and operating systems from different vendors to interoperate. You can think of WinRM as the server side and WinRS the client side of WS-Management.
winrs -r:<some computer> ipconfig /all

http://technet.microsoft.com/en-us/library/dd163506.aspx
QUESTION 343
You have a domain controller named Server1 that runs Windows Server 2012 R2 and has the DNS Server server role installed. Server1 hosts a DNS zone named contoso.com and a GlobalNames zone. You discover that the root hints were removed from Server1. You need to view the default root hints of Server1. Which file should you open?
A. Netlogon.dns
B. Cache.dns
C. Globalnames.dns
D. Place.dns
Answer: B
Explanation:
DNS Server service implements root hints using a file, Cache.dns, stored in the systemroot\System32\Dns folder on the server. Thus viewing the Cache.dns file will show the root hints.
QUESTION 344
You work as an administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers on the contoso.com network have Windows Server 2008 R2 installed. Most of the contoso.com servers have 64 – bit CPU’s installed, while the rest have 32 bit CPU’s installed. You are informed that contoso.com wants to deploy Windows Server 2012 R2 on all their servers. You need to make recommendations to ensure that this is possible. Which of the following would you recommend?
A. You should inform contoso.com that the deployment can proceed without any changes.
B. You should inform contoso.com that the servers with 32 bit CPU’s must be upgraded to include 64 bit CPU’s for the deployment to proceed.
C. You should inform contoso.com that the servers with 64 bit CPU’s must be upgraded to include 32 bit CPU’s for the deployment to proceed.
D. You should inform contoso.com that the deployment is not in any way possible.
Answer: B
Explanation:
Windows Server 2012 is a 64-bit only operating system. Minimum: 1.4 GHz 64-bit processor.
http://technet.microsoft.com/en-us/library/jj134246.aspx
QUESTION 345
You work as an administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers on the contoso.com network have Windows Server 2012 installed. contoso.com has its headquarters in London, and several widespread satellite offices. When contoso.com releases a new written policy stating that the graphical user interface (GUI) should not be installed on any servers deployed to contoso.com’s satellite offices. It is reported that a server in one of the satellite offices are not compliant with the new written policy. You are required to remedy the situation, while using the least amount of user interaction. Which of the following actions should you take?
A. You should consider uninstalling the User Interfaces and Infrastructure feature using a PowerShell cmdlet.
B. You should consider uninstalling the User Interfaces and Infrastructure feature via TS Manager.
C. You should consider uninstalling the User Interfaces and Infrastructure feature via Server Manager.
D. You should consider uninstalling the User Interfaces and Infrastructure feature using the Dsrm.exe command from the command prompt.
Answer: A
Explanation:
Within the Powershell command-line you can use the tab key to complete the command and it helps you to select the correct options needed. If an answer talks about using Powershell it is the most obvious answer (from a MS perspective). You have to start server manager and add the server or make a RDP connection to that server and start server manager. Then click around the GUI to UN-install the GUI.
QUESTION 346
You work as an administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers in the contoso.com domain, including domain controllers, have Windows Server 2012 installed. contoso.com has a server, named PL-SR07, which has four network adapters. contoso.com has two SR07’s network adapters are connected to the one LAN, local area networks (LANs). Two of L2P…while the other two are connected to the other LAN. You are required to configure one of the network adapter pairs into a network adapter team. Which of the following actions should you take?
A. You should consider accessing the Group Policy Management Console (GPMC) on PL-SR07.
B. You should consider accessing the TS Manager console on PL-SR07.
C. You should consider accessing the Server Manager console on PL-SR07.
D. You should consider accessing the Remote Desktop Gateway Manager console on PL-SR07.
Answer: C
Explanation:
NIC teaming, also known as Load Balancing/Failover (LBFO), allows multiple network adapters tobe placed into a team for the purposes of bandwidth aggregation, and/or traffic failover to maintain connectivity in the event of a network component failure.
http://www.microsoft.com/en-us/download/details.aspx?id=30160
QUESTION 347
You work as an administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers on the contoso.com network have Windows Server 2012 installed. A server named, PL-SR13, has a Server Core Installation of Windows Server 2012 installed. SR13’s installation to a Server with GUI installation. You are instructed to convert L2P…You want to use a Windows PowerShell cmdlet that uses Windows Update as a source. Which of the following actions should you take?
A. You should consider making use of the Install-WindowsFeature Server-Gui-Mgmt-Infra, Server-Gui-Shell -Restart cmdlet.
B. You should consider making use of the Install-WindowsFeature Server-Gui-Mgmt-Infra, Server-Gui-Shell -Restart -Source c:\mountdir\windows\winsxs cmdlet.
C. You should consider making use of the Uninstall-WindowsFeature Server-Gui-Shell-Remove cmdlet.
D. You should consider making use of the Set-ExecutionPolicy cmdlet.
Answer: A
Explanation:
The Full GUI Server Interface provides you with the full GUI of Windows Server 2012 R2.
PowerShell Command: Install-WindowsFeature Server-Gui-Mgmt-Infra, Server-Gui-Shell
When its done, we will need to restart our server by using the Shutdown command:
shutdown -r -t 0
http://blogs.technet.com/b/bruce_adamczak/archive/2013/02/06/windows-2012-core-survival-guide-changing-the-gui-type.aspx
http://www.howtogeek.com/111967/how-to-turn-the-gui-off-and-on-in-windows-server-2012/
QUESTION 348
You work as a senior administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers on the contoso.com network have Windows Server 2012 installed. You are running a training exercise for junior administrators. You are currently discussing Storage Spaces. Which of the following is TRUE with regards to Storage Spaces?
A. Mirroring and parity are optional resilient storage modes of Storage Spaces.
B. Failover clustering is not supported by Storage Spaces.
C. Storage spaces are virtual disks with associated attributes such as a preferred level of resiliency, and thin or fixed provisioning.
D. Storage spaces are a collection of physical disks with associated attributes such as a preferred level of resiliency, and thin or fixed provisioning.
Answer: AC
Explanation:
Storage Spaces lets you group drives together in a storage pool. Then you can use pool capacity to create storage spaces. Storage spaces are virtual drives that appear in File Explorer. You can use them like any other drive, so it’s easy to work with files on them. You can create large storage spaces and add more drives to them when you run low on pool capacity. Storage Spaces includes the following features:
1. Storage pools. Storage pools are the fundamental building blocks for Storage Spaces. Administrators are already familiar with this concept, so they will not have to learn a new model. They can flexibly create storage pools based on the needs of the deployment. For example, given a set of physical disks, an administrator can create one pool (by using all the available physical disks) or multiple pools (by dividing the physical disks as required). Furthermore, to maximize the value from storage hardware, the administrator can map a storage pool to combinations of hard disks as well as solid-state drives (SSDs). Pools can be expanded dynamically by simply adding additional drives, thereby seamlessly scaling to cope with unceasing data growth.
2. Multitenancy. Administration of storage pools can be controlled through access control lists (ACLs) and delegated on a per-pool basis, thereby supporting hosting scenarios that require tenant isolation. Storage Spaces follows the familiar Windows security model; therefore, it can be fully integrated with Active Directory Domain Services.
3. Resilient storage. Storage Spaces support two optional resiliency modes: mirroring and parity. Per-pool support for disks that are reserved for replacing failed disks (hot spares), background scrubbing, and intelligent error correction allow continuous service availability despite storage component failures. In the event of a power failure or cluster failover, the integrity of data is preserved so that recovery happens quickly and does not result in data loss.
4. Continuous availability. Storage Spaces is fully integrated with failover clustering, which allows it to deliver continuously available service deployments. One or more pools can be clustered across multiple nodes within a single cluster. Storage spaces can then be instantiated on individual nodes, and the storage will seamlessly fail over to a different node when necessary (in response to failure conditions or due to load balancing). Integration with CSVs permits scale-out access to data.
5. Optimal storage use. Server consolidation often results in multiple data sets sharing the same storage hardware. Storage Spaces supports thin provisioning to allow businesses to easily share storage capacity among multiple unrelated data sets and thereby maximize capacity use.
6. Storage Spaces also supports trim, automatically running the Storage Optimizer to help reduce the physical footprint of data by consolidating data.
7. Operational simplicity. Fully remoteable and scriptable management is permitted through the Windows Storage Management API, WMI, and Windows PowerShell. Storage Spaces can be easily managed through the File and Storage Services role in Server Manager. Storage Spaces also provides notifications when the amount of available capacity in a storage pool hits a configurable threshold.
http://windows.microsoft.com/en-us/windows-8/storage-spaces-pools
http://technet.microsoft.com/en-us/library/hh831739.aspx
http://www.howtogeek.com/109380/how-to-use-windows-8s-storage-spaces-to-mirror-combine-drives/
QUESTION 349
You work as a senior administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers on the contoso.com network have Windows Server 2012 installed. You are running a training exercise for junior administrators. You are currently discussing NIC Teaming. Which of the following is TRUE with regards to NIC Teaming? (Choose all that apply.)
A. It allows for traffic failover to prevent connectivity loss if a network component fails.
B. It prevents bandwidth aggregation.
C. The Windows Server 2012 implementation of NIC Teaming supports a maximum of 5 NICs in a team.
D. The Windows Server 2012 implementation of NIC Teaming supports a maximum of 32 NICs in a team.
Answer: AD
QUESTION 350
You work as a senior administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers on the contoso.com network have Windows Server 2012 installed. You are running a training exercise for junior administrators. You are currently discussing spanned volumes. Which of the following is TRUE with regards to spanned volumes? (Choose all that apply.)
A. Spanned volumes do not provide fault tolerance.
B. Spanned volumes are a fault tolerant solution.
C. You can extend a spanned volume onto a maximum of 16 dynamic disks.
D. You cannot create a spanned volume using a system volume or boot volume.
Answer: AD
Explanation:
A spanned volume is a dynamic volume consisting of disk space on more than one physical disk. If a simple volume is not a system volume or boot volume, you can extend it across additional disks to create a spanned volume, or you can create a spanned volume in unallocated space on a dynamic disk. You need at least two dynamic disks in addition to the startup disk to create a spanned volume. You can extend a spanned volume onto a maximum of 32 dynamic disks. Spanned volumes are not fault tolerant.
http://technet.microsoft.com/en-us/library/cc772180.aspx
QUESTION 351
You work as an administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers in the contoso.com domain, including domain controllers, have Windows Server 2012 R2 installed. You have just executed the Uninstall-WindowsFeature Server-Gui-Shell contoso.com server, named PL-SR13. Which of the following is the reason for doing this?
A. To only remove Windows Explorer from PL-SR13.
B. To only remove the Windows Internet Explorer from PL-SR13.
C. To only remove the components and files related to Windows Explorer from PL-SR13.
D. To remove Windows Explorer, Windows Internet Explorer, and all associated components and files from PL-SR13.
Answer: D
Explanation:
Minimal Server Interface: If the server has a full installation of Windows Server, and I need to bring the server down to minimal server interface, I only need to remove the Server-GUI-Shell. The command is shown here:
Get-WindowsFeature Server-Gui-Shell | Uninstall-WindowsFeature – restart
Minimal Server Interface is situated between the Server Core and Server with a GUI modes, you can either install features on Server Core or remove features from Server with a GUI to reach the Minimal Server Interface installation state.
http://blogs.technet.com/b/heyscriptingguy/archive/2013/01/25/use-powershell-to-remove-the-gui-on-windows-server-2012.aspx
http://blogs.technet.com/b/server_core/archive/2012/05/09/configuring-the-minimal-server-interface.aspx
QUESTION 352
You work as an administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers in the contoso.com domain, including domain controllers, have Windows Server 2012 R2 installed. You have been instructed to add a new domain controller to contoso.com’s existing environment. Which of the following actions should you take?
A. You should consider making use of Server Manager.
B. You should consider making use of Authorization Manager.
C. You should consider making use of Remote Desktop Gateway Manager.
D. You should consider making use of Network Load Balancing Manager.
Answer: A
Explanation:
http://social.technet.microsoft.com/wiki/contents/articles/12370.step-by-step-guide-for-setting-up-windows-server-2012-domain-controller.aspx
QUESTION 353
You work as an administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers in the contoso.com domain, including domain controllers, have Windows Server 2012 installed. You have been instructed to modify an Active Directory computer object. Which of the following actions should you take?
A. You should consider making use of the Get-ADComputer Windows PowerShell cmdlet
B. You should consider making use of the Set-ADComputer Windows PowerShell cmdlet
C. You should consider making use of the New-ADComputer Windows PowerShell cmdlet
D. You should consider making use of the Get-ADComputerServiceAccount Windows PowerShell cmdlet
Answer: B
Explanation:
Set-ADComputer – Modifies an Active Directory computer object.
http://technet.microsoft.com/en-us/library/ee617263.aspx
QUESTION 354
You work as an administrator at contoso.com. The contoso.com network consists of an Active Directory forest that contains a root domain, named contoso.com, and two child domains, named us.contoso.com and uk.contoso.com. All servers on the contoso.com network have Windows Server 2012 R2 installed. The root domain hosts a domain local distribution group, named L2PGroup. You are preparing to issue L2PGroup read-only access to a shared folder hosted by the us.contoso.com domain. You want to make sure that L2PGroup is able to access the shared folder in the us.contoso.com domain. Which of the following actions should you take?
A. You should consider re-configuring L2PGroup as a universal Admins group.
B. You should consider re-configuring L2PGroup as a universal security group.
C. You should consider re-configuring L2PGroup as a global administrators group.
D. You should consider re-configuring L2PGroup as a local administrators group.
Answer: B
Explanation:
Group scope Universal can be assigned permissions in any domain or forest.

http://technet.microsoft.com/en-us/library/cc781446(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/cc755692(v=ws.10).aspx
QUESTION 355
You work as an administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. contoso.com has a domain controller, named L2P-DC01, which has Windows Server 2012 R2 installed. Another contoso.com domain controller, named L2P-DC02, has Windows Server 2008 R2 installed. You have deployed a server, named PL-SR15, on contoso.com’s perimeter network. PL-SR15 is running a Server Core Installation of Windows Server 2012 R2. You have been instructed to make sure that PL-SR15 is part of the contoso.com domain. Which of the following actions should you take?
A. You should consider making use of Set-Computer Windows PowerShell cmdlet on PL-SR15.
B. You should consider making use of Get-Computer Windows PowerShell cmdlet on PL-SR15.
C. You should consider making use of Test-Computer Windows PowerShell cmdlet on PL-SR15.
D. You should consider making use of Add-Computer Windows PowerShell cmdlet on PL-SR15.
Answer: D
Explanation:
Add-Computer – Add the local computer to a domain or workgroup.
http://technet.microsoft.com/en-us/library/hh849798.aspx
QUESTION 356
You work as an administrator at contoso.com. The contoso.com network consists of two Active Directory forests, named contoso.com and test.com. There is no trust relationship configured between the forests. A backup of Group Policy Object (GPO) from the test.com domain is stored on a domain controller in the contoso.com domain. You are informed that a GPO must be created in the contoso.com domain, and must be based on the settings of the GPO in the test.com domain. You start by creating the new GPO using the New-GPO Windows PowerShell cmdlet. You want to complete the task via a Windows PowerShell cmdlet. Which of the following actions should you take?
A. You should consider making use of the Invoke-GPUpdate Windows PowerShell cmdlet.
B. You should consider making use of the Copy-GPO Windows PowerShell cmdlet.
C. You should consider making use of the New-GPLink Windows PowerShell cmdlet.
D. You should consider making use of the Import-GPO Windows PowerShell cmdlet.
Answer: D
Explanation:
Import-GPO – Imports the Group Policy settings from a backed-up GPO into a specified GPO.
http://technet.microsoft.com/en-us/library/ee461044.aspx
QUESTION 357
You work as an administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers in the contoso.com domain, including domain controllers, have Windows Server 2012 R2 installed. contoso.com has a server, named PL-SR15, which is configured as a file server. You have received instructions to make sure that a user, named Mia Hamm, has the ability to generate a complete backup of PL-SR15 via Windows Server Backup. Which of the following actions should you take?
A. You should consider making use of Computer Management to configure the local groups.
B. You should consider making use of Computer Management to configure the domain local groups.
C. You should consider making use of Computer Management to configure the global groups.
D. You should consider making use of Computer Management to configure the administrator groups.
Answer: A
Explanation:
To perform backups or recoveries by using Windows Server Backup, you must be a member of the Administrators or Backup Operators groups.
http://technet.microsoft.com/en-us/library/ee849849%28v=ws.10%29.aspx
Notes:
You can only use Backup locally; you cannot backup a remote computer. You can only back up and restore System State data on a local computer. You cannot back up and restore System State data on a remote computer even if you are an administrator on the remote computer.
http://technet.microsoft.com/en-us/library/cc776822%28v=ws.10%29.aspx
QUESTION 358
You work as a senior administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers on the contoso.com network have Windows Server 2012 R2 installed. You are running a training exercise for junior administrators. You are currently discussing the Windows Firewall with Advanced Security feature. Which of the following is TRUE with regards to Windows Firewall with Advanced Security? (Choose all that apply.)
A. It provides host-based, two-way network traffic filtering for a computer.
B. It provides host-based, one-way network traffic filtering for a computer.
C. It blocks unauthorized network traffic flowing into or out of the local computer.
D. It only blocks unauthorized network traffic flowing into the local computer.
E. It only blocks unauthorized network traffic flowing out of the local computer.
Answer: AC
Explanation:
Windows Firewall with Advanced Security is an important part of a layered security model. By providing host-based, two-way network traffic filtering for a computer, Windows Firewall with Advanced Security blocks unauthorized network traffic flowing into or out of the local computer. Windows Firewall with Advanced Security also works with Network Awareness so that it can apply security settings appropriate to the types of networks to which the computer is connected. Windows Firewall and Internet Protocol Security (IPsec) configuration settings are integrated into a single Microsoft Management Console (MMC) named portant part of your network’s Windows Firewall with Advanced Security, so Windows Firewall is also an im isolation strategy.
http://technet.microsoft.com/en-us/library/hh831365.aspx
QUESTION 359
You work as a senior administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers on the contoso.com network have Windows Server 2012 R2 installed. You are running a training exercise for junior administrators. You are currently discussing connection security rules. Which of the following is TRUE with regards to connection security rules? (Choose all that apply.)
A. Connection security rules allows for traffic to be secured via IPsec.
B. Connection security rules do not allow the traffic through the firewall.
C. Connection security rules are applied to programs or services.
D. Connection security rules are applied between two computers.
Answer: ABD
Explanation:
Connection security involves the authentication of two computers before they begin communications and the securing of information sent between two computers. Windows Firewall with Advanced Security uses Internet Protocol security (IPsec) to achieve connection security by using key exchange, authentication, data integrity, and, optionally, data encryption.
How firewall rules and connection security rules are related?
Firewall rules allow traffic through the firewall, but do not secure that traffic. To secure traffic with IPsec, you can create Computer Connection Security rules. However, the creation of a connection securityrule does not allow the traffic through the firewall. You must create a firewall rule to do this, if the traffic is not allowed by the default behavior of the firewall. Connection security rules are not applied toprograms or services; they are applied between the computers that make up the two endpoints.
http://technet.microsoft.com/en-us/library/cc772017.aspx
http://technet.microsoft.com/en-us/library/cc772017%28v=ws.10%29.aspx
QUESTION 360
You work as an administrator at contoso.com. The contoso.com network consists of a single domain named contoso.com. All servers in the contoso.com domain, including domain controllers, have Windows Server 2012 R2 installed. You have been instructed to make sure that contoso.com users are not able to install a Windows Store application. You then create a rule for packaged apps. Which of the following is the rule based on? (Choose all that apply.)
A. The publisher of the package.
B. The publisher of the application.
C. The name of the package.
D. The name of the application.
E. The package version.
F. The application version.
Answer: ACE
Explanation:
Packaged apps (also known as Windows 8 apps) are new to Windows Server 2012 R2 and Windows 8. They are based on the new app model that ensures that all the files within an app package share the same identity. Therefore, it is possible to control the entire application using a single AppLocker rule as opposed to the non-packaged apps where each file within the app could have a unique identity. Windows does not support unsigned packaged apps which implies all packaged apps must be signed. AppLocker supports only publisher rules for Packaged apps. A publisher rule for a Packaged app is based on the following information:
– Publisher of the package
– Package name
– Package version
All the files within a package as well as the package installer share these attributes. Therefore, an AppLocker rule for a Packaged app controls both the installation as well as the running of the app. Otherwise, the publisher rules for Packaged apps are no different than the rest of the rule collections; they support exceptions, can be increased or decreased in scope, and can be assigned to users and groups.
http://technet.microsoft.com/en-us/library/hh994588.aspx
Get the newest PassLeader 70-410 VCE dumps here: http://www.passleader.com/70-410.html (512 Q&As Dumps –> 528 Q&As Dumps)
And, DOWNLOAD the newest PassLeader 70-410 PDF dumps from Cloud Storage for free: https://drive.google.com/open?id=0B-ob6L_QjGLpfnJzOE1fWnlJOWVtaE93SnJNT3gtaTNYYnVpZkw5THBSMWRKbFlfaXh1azg