Valid MS-102 Dumps shared by PassLeader for Helping Passing MS-102 Exam! PassLeader now offer the newest MS-102 VCE dumps and MS-102 PDF dumps, the PassLeader MS-102 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader MS-102 dumps with VCE and PDF here: https://www.passleader.com/ms-102.html (509 Q&As Dumps –> 563 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader MS-102 dumps from Cloud Storage: https://drive.google.com/drive/folders/1EgG1HXOLli3rw4OX-3NpXshMm5dHpomY
NEW QUESTION 471
You are deploying Microsoft Intune. You successfully enroll Windows 10 devices in Intune. When you try to enroll an iOS device in Intune, you get an error. You need to ensure that you can enroll the iOS device in Intune.
Solution: You create an Apple Configurator enrollment profile.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
Apple configurator it is just an enrollment method not a pre requisite for enrolling apple devices.
NEW QUESTION 472
You have a Microsoft 365 subscription. You discover that some external users accessed content on a Microsoft SharePoint site. You modify the SharePoint sharing policy to prevent sharing outside your organization. You need to be notified if the SharePoint sharing policy is modified in the future.
Solution: From the Security & Compliance admin center, you create a threat management policy.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/compliance/alert-policies
https://protection.office.com/alertpolicies
NEW QUESTION 473
Your network contains an Active Directory domain named contoso.com that is synced to Microsoft Azure Active Directory (Azure AD). You manage Windows 10 devices by using Microsoft System Center Configuration Manager (Current Branch). You configure pilot co-management. You add a new device named Device 1 to the domain. You install the Configuration Manager client on Device1. You need to ensure that you can manage Device1 by using Microsoft Intune and Configuration Manager.
Solution: You add Device1 to a Configuration Manager device collection.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
Device collection needs to be defined as a pilot device collection for co-management.
NEW QUESTION 474
You have a Microsoft 365 tenant. You plan to manage incidents in the tenant by using the Microsoft Defender XDR. Which Microsoft service source will appear on the Incidents page of the Microsoft Defender portal?
A. Azure Information Protection
B. Azure Web Application Firewall
C. Microsoft Sentinel
D. Microsoft Defender for Cloud Apps
Answer: C
Explanation:
Alerts in the Microsoft Defender portal come from many sources. These sources include the many services that are part of Microsoft Defender XDR, as well as other services with varying degrees of integration with the Microsoft Defender portal. For example, when Microsoft Sentinel is onboarded to the Microsoft Defender portal, the correlation engine in the Defender portal has access to all the raw data ingested by Microsoft Sentinel, which you can find in Defender’s Advanced hunting tables.
https://learn.microsoft.com/en-us/defender-xdr/incidents-overview
NEW QUESTION 475
You have a Microsoft 365 subscription. You need to view a list of known tools used by malicious actors. What should you use in the Microsoft Defender portal?
A. Intel explorer.
B. Threat analytics.
C. Intel profiles.
D. Intel projects.
Answer: B
Explanation:
To view a list of known tools used by malicious actors within the Microsoft Defender portal, you can utilize the Threat Analytics feature. This feature provides detailed information about current threats, including the tactics, techniques, and procedures (TTPs) employed by attackers, which often include specific tools.
https://learn.microsoft.com/en-us/defender-xdr/microsoft-365-defender-portal
NEW QUESTION 476
You have a Microsoft 365 subscription that uses a third-party multifactor authentication (MFA) product. While reviewing Microsoft Secure Score, you discover that there are no points listed for the Ensure multifactor authentication is enabled for all users recommendation. You need to ensure that you receive all the points for the recommendation. The solution must minimize administrative effort. What should you do?
A. Deploy a Microsoft Defender for Identity sensor.
B. Modify the recommendation tags.
C. Modify the status of the recommendation.
D. Configure a data connector.
Answer: B
Explanation:
In Azure, recommendation tags are used to categorize and filter security recommendations within Microsoft Defender for Cloud and are related to Microsoft Secure Score. These tags are metadata that help users understand and prioritize security improvements. Recommendations are suggestions for improving security posture, and the Secure Score reflects how well an organization is implementing these recommendations.
https://learn.microsoft.com/en-us/azure/defender-for-cloud/secure-score-security-controls
NEW QUESTION 477
You have a Microsoft 365 E5 subscription. You are evaluating Microsoft Defender for Cloud Apps. Which two types of policy rely on Conditional Access App Control? (Each correct answer presents a complete solution. Choose two.)
A. app discovery policy
B. OAuth app policy
C. access policy
D. file policy
E. session policy
F. activity policy
Answer: CE
Explanation:
For Microsoft Defender for Cloud Apps, both access policies and session policies rely on Conditional Access App Control. These policies allow you to monitor and control user access and sessions to cloud apps based on real-time conditions defined in your Conditional Access policies.
– Access Policies:
These policies control whether users are granted access to a cloud application based on various conditions, such as user location, device state, and risk level.
– Session Policies:
These policies focus on controlling user activities within a cloud application session, such as blocking file downloads, restricting copy-paste actions, or protecting downloaded files with Azure Information Protection.
https://learn.microsoft.com/en-us/defender-cloud-apps/proxy-intro-aad
NEW QUESTION 478
You have a Microsoft 365 E5 subscription that uses Microsoft Intune. You need to ensure that during device enrollment in Intune, users are prevented from using their device until all assigned apps and profiles are installed. What should you configure?
A. a Conditional Access policy
B. a Windows Autopilot deployment profile
C. an enrollment restriction
D. an Enrollment Status Page profile
Answer: D
Explanation:
https://learn.microsoft.com/en-us/mem/intune/enrollment/windows-enrollment-status
NEW QUESTION 479
You have an Azure AD tenant. You have 1,000 computers that run Windows 10 Pro and are joined to Azure AD. You purchase a Microsoft 365 E3 subscription. You need to deploy Windows 10 Enterprise to the computers. The solution must minimize administrative effort. What should you do?
A. From the Microsoft Endpoint Manager admin center, create a Windows Autopilot deployment profile.
Assign the profile to all the computers.
Instruct users to restart their computer and perform a network restart.
B. Enroll the computers in Microsoft Intune.
Create a configuration profile by using the Edition upgrade and mode switch template.
From the Microsoft Endpoint Manager admin center, assign the profile to all the computers and instruct users to restart their computer.
C. From Windows Configuration Designer, create a provisioning package that has an EditionUpgrade configuration and upload the package to a Microsoft SharePoint Online site.
Instruct users to run the provisioning package from SharePoint Online.
D. From the Azure Active Directory admin center, create a security group that has dynamic device membership.
Assign licenses to the group and instruct users to sign in to their computer.
Answer: B
Explanation:
https://learn.microsoft.com/en-us/mem/intune/configuration/edition-upgrade-configure-windows-10
NEW QUESTION 480
You have a Microsoft 365 E5 subscription that contains 500 users. Two hundred users have personal devices that run either Android, Windows 10, or macOS. Three hundred users have corporate-owned devices that run either Windows 10 or macOS. You plan to configure device enrollment. You need to ensure that you can apply separate policies to the corporate-owned devices and the personal devices. The solution must minimize administrative effort. What should you create first?
A. a dynamic device group
B. a dynamic user group
C. a deployment package
D. a Microsoft 365 group
Answer: A
Explanation:
To apply different policies to corporate-owned and personally owned devices in Microsoft Intune (part of Microsoft Endpoint Manager, included with Microsoft 365 E5), you need a way to separate those devices logically. The most efficient way to do this – with minimal administrative effort – is to use dynamic device groups in Microsoft Entra ID (formerly Azure AD).
NEW QUESTION 481
You have a Microsoft 365 tenant. You plan to implement device configuration profiles in Microsoft Intune. Which platform can you manage by using the profiles?
A. Windows 8.1
B. CentOS Linux
C. Windows 10
D. Android Enterprise
Answer: ACD
Explanation:
When you create a profile (Configuration profiles –> Create profile), choose your platform:
– Android device administrator
– Android Enterprise
– iOS/iPadOS
– macOS
– Windows 10 and later
– Windows 8.1 and later
https://learn.microsoft.com/en-us/mem/intune/configuration/device-profile-create
NEW QUESTION 482
You have a Microsoft 365 subscription. You need to be notified if users receive email containing a file that has a virus. What should you do?
A. From the Exchange admin center, create an in-place eDiscovery & hold.
B. From the Security & Compliance admin center, create a safe attachments policy.
C. From the Security & Compliance admin center, create a data loss prevention (DLP) policy.
D. From the Security & Compliance admin center, create an alert policy.
Answer: D
Explanation:
https://docs.microsoft.com/en-us/office365/securitycompliance/alert-policies
NEW QUESTION 483
You have a Microsoft 365 E5 subscription. You plan to deploy Microsoft Defender for Cloud Apps. You need to ensure that Microsoft Defender for Cloud Apps can differentiate between internal and external users. What should you do?
A. From the Microsoft 365 admin center, configure the Org settings.
B. From the Microsoft 365 admin center, configure the default domain.
C. From the Microsoft Defender for Cloud Apps portal, add a list of managed domains.
D. From the Microsoft Defender for Cloud Apps portal, configure the Organization details.
Answer: C
Explanation:
Make sure you add a list of your Managed domains to identify internal users. Adding managed domains is a crucial step. Defender for Cloud Apps uses the managed domains to determine which users are internal, external, and where files should and shouldn’t be shared. This information is used for reports and alerts.
https://docs.microsoft.com/en-us/defender-cloud-apps/general-setup
NEW QUESTION 484
You have a Microsoft Azure Active Directory (Azure AD) tenant. The organization needs to sign up for Microsoft Store for Business. The solution must use the principle of least privilege. Which role should you assign to the user?
A. Global administrator.
B. Cloud application administrator.
C. Application administrator.
D. Service administrator.
Answer: A
Explanation:
To sign up your organization for the Microsoft Store for Business (or its successor, Microsoft Store for Business and Education), the first registration must be performed by a user with global administrator permissions in Azure Active Directory (now Microsoft Entra ID). This is required because:
– The Microsoft Store for Business links to your Azure AD tenant during setup.
– Only a Global administrator can consent to this integration on behalf of the organization.
– After the initial setup, other users can be assigned lower roles (e.g., Store administrators, purchasers, etc.) within the Store itself.
NEW QUESTION 485
You have a Microsoft 365 subscription. Your company purchases a new financial application named App1. From Cloud Discovery in Microsoft Defender for Cloud Apps, you view the Discovered apps page and discover that many applications have a low score because they are missing information about domain registration and consumer popularity. You need to prevent the missing information from affecting the App1 score. What should you configure from the Cloud Discover settings?
A. Organization details.
B. Default behavior.
C. Score metrics.
D. App tags.
Answer: C
Explanation:
We should modify the score metric and give less weight to the domain registration and consumer popularity fields. Go to Settings –> Cloud Discovery –> Score metrics and there you can lower the score weight of “Consumer popularity” and “Domain registration” fields. These are located at the General category inside Score Metrics.
https://docs.microsoft.com/en-us/cloud-app-security/risk-score#customizing-the-risk-score
NEW QUESTION 486
Your network contains an on-premises Active Directory domain. Your company has a security policy that prevents additional software from being installed on domain controllers. You need to monitor a domain controller by using Microsoft Defender for Identity. What should you do?
A. Deploy a Microsoft Defender for identity sensor, and then configure port mirroring.
B. Deploy a Microsoft Defender for identity sensor, and then configure detections.
C. Deploy a Microsoft Defender for Identity standalone sensor, and then configure detections.
D. Deploy a Microsoft Defender for Identity standalone sensor, and then configure port mirroring.
Answer: D
Explanation:
We cannot install additional software on the domain controllers. Azure ATP Standalone Sensor is a full agent installed on a dedicated server that can monitor traffic from multiple domain controllers. This is an alternative to those that do not wish to install an agent directly on a domain controller.
https://docs.microsoft.com/en-us/azure-advanced-threat-protection/install-atp-step5
https://docs.microsoft.com/en-us/defender-for-identity/configure-port-mirroring
NEW QUESTION 487
Your company has a Microsoft 365 E5 subscription. Users in the research department work with sensitive data. You need to prevent the research department users from accessing potentially unsafe websites by using hyperlinks embedded in email messages and documents. Users in other departments must not be restricted. What should you do?
A. Create a data toss prevention (DLP) policy that has a Content is shared condition.
B. Modify the default safe links policy.
C. Create a data loss prevention (DLP) policy that has a Content contains condition.
D. Create a new safe links policy.
Answer: D
Explanation:
ATP Safe Links, a feature of Office 365 Advanced Threat Protection (ATP), can help protect your organization from malicious links used in phishing and other attacks. If you have the necessary permissions for the Office 365 Security & Compliance Center, you can set up ATP Safe Links policies to help ensure that when people click web addresses (URLs), your organization is protected. Your ATP Safe Links policies can be configured to scan URLs in email and URLs in Office documents.
https://docs.microsoft.com/en-us/office365/securitycompliance/set-up-atp-safe-linkspolicies#policies-that-apply
NEW QUESTION 488
You have a Microsoft 365 tenant. You have a line-of-business application named App1 that users access by using the My Apps portal. After some recent security breaches, you implement a conditional access policy for App1 that uses Conditional Access App Control. You need to be alerted by email if impossible travel is detected for a user of Appl. The solution must ensure that alerts are generated for App1 only. What should you do?
A. From Microsoft Cloud App Security, create a Cloud Discovery anomaly detection policy.
B. From Microsoft Cloud App Security, modify the impossible travel alert policy.
C. From Microsoft Cloud App Security, create an app discovery policy.
D. From the Azure Active Directory admin center, modify the conditional access policy.
Answer: B
Explanation:
If you click on create policy and then “Create Cloud Discovery anomaly detection policy” you have two templates “Anomalous behavior in discovered users” and “Anomalous behavior of discovered IP addresses”. None of these permits the creation of a impossible travel policy. But if you go the policies page, you can modify the built-in “Impossible travel” policy, inside the category “Anomaly detection” policy.
https://docs.microsoft.com/en-us/cloud-app-security/cloud-discovery-anomaly-detection-policy
NEW QUESTION 489
The users at your company use Dropbox Business to store documents. The users access Dropbox Business by using the MyApps portal. You need to ensure that user access to Dropbox Business is authenticated by using a Microsoft 365 identity. The documents must be protected if the data is downloaded to a device that is not trusted. What should you do?
A. From the Azure Active Directory admin center, configure conditional access settings.
B. From the Azure Active Directory admin center, configure the Organizational relationships settings.
C. From the Endpoint Manager admin center, configure device enrollment settings.
D. From the Azure Active Directory admin center, configure the Devices settings.
Answer: A
Explanation:
A Conditional Access policy specifies the app or services you want to protect, the conditions under which the apps or services can be accessed, and the users the policy applies to.
https://docs.microsoft.com/en-us/mem/intune/protect/create-conditional-access-intune
NEW QUESTION 490
Your network contains an Active Directory domain named contoso.com. The domain contains 100 Windows 8.1 devices. You plan to deploy a custom Windows 10 Enterprise image to the Windows 8.1 devices. You need to recommend a Windows 10 deployment method. What should you recommend?
A. a provision g package
B. an in place upgrade
C. wipe and load refresh
D. Windows Autopilot
Answer: C
Explanation:
To deploy a custom image, you must use the wipe and load refresh method. You cannot deploy a custom image by using an in-place upgrade, Windows Autopilot or a provisioning package.
https://docs.microsoft.com/en-us/windows/deployment/windows-10-deployment-scenarios
NEW QUESTION 491
You have Windows 10 Pro devices that are joined to an Active Directory domain. You plan to create a Microsoft 365 tenant and to upgrade the devices to Windows 10 Enterprise. You are evaluating whether to deploy Windows Hello for Business. What are two prerequisites of the deployment? (Each correct answer presents a complete solution. Choose two.)
A. Microsoft Azure Active Directory (Azure AD)
B. smartcards
C. Microsoft Intune enrollment
D. TPM-enabled devices
E. computers that have biometric hardware features
Answer: AC
Explanation:
Windows Hello for Business definitely possible without TPM or Smart card.
https://docs.microsoft.com/en-us/windows/security/information-protection/tpm/tpm-recommendations
NEW QUESTION 492
Your company has a Microsoft 365 E3 subscription. All devices run Windows 10 Pro and are joined to Microsoft Azure Active Directory (Azure AD). You need to change the edition of Windows 10 to Enterprise the next time users sign in to their computer. The solution must minimize downtime for the users. What should you use?
A. Windows Autopilot
B. Windows Update
C. Subscription Activation
D. an in-place upgrade
Answer: C
Explanation:
It would only require assigning the license and then having the user sign in. Autopilot is used for new/reset devices that are at the OOBE screen.
https://docs.microsoft.com/en-us/windows/deployment/windows-10-subscription-activation
NEW QUESTION 493
Your company has a Microsoft 365 subscription. You need to identify which users performed the following privileged administration tasks:
– Deleted a folder from the second-stage Recycle Bin of Microsoft SharePoint.
– Opened a mailbox of which the user was not the owner.
– Reset a user password.
What should you use?
A. Microsoft Azure Active Directory (Azure AD) audit logs.
B. Microsoft 365 compliance content search.
C. Microsoft Azure Active Directory (Azure AD) sign-ins.
D. Microsoft 365 compliance audit log search.
Answer: D
Explanation:
The M365 Compliance audit log (now found at compliance.microsoft.com) contains everything required in order to ascertain who made the changes specified within the question.
https://docs.microsoft.com/en-us/microsoft-365/compliance/search-the-audit-log-in-security-and-compliance?view=o365-worldwide
NEW QUESTION 494
You have a Microsoft 365 subscription. You have a user named User1. You need to ensure that User1 can place a hold on all mailbox content. What permission should you assign to User1?
A. e Discovery Manager from the Security & Compliance admin center
B. compliance management from the Exchange admin center
C. User management administrator from the Microsoft 365 admin center
D. Information Protection administrator from the Azure Active Directory admin center
Answer: A
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/compliance/assign-ediscovery-permissions?view=o365-worldwide#rbac-roles-related-to-ediscovery
NEW QUESTION 495
You have a Microsoft 365 subscription. All users are assigned a Microsoft 365 E3 License. You enable auditing for your organization. What is the maximum amount of time data will be retained in the Microsoft 365 audit log?
A. 2 years
B. 1 year
C. 30 days
D. 90 days
Answer: D
Explanation:
For users assigned any other (non-E5) Office 365 or Microsoft 365 license, audit records are retained for 90 days. For users assigned an Office 365 E5 or Microsoft 365 E5 license for up to one year.
https://docs.microsoft.com/en-us/microsoft-365/compliance/search-the-audit-log-in-security-and-compliance?view=o365-worldwide
NEW QUESTION 496
You have a Microsoft 365 subscription. You configure a data loss prevention (DIP) policy. You discover that users are incorrectly marking content as false positive and bypassing the OLP policy. You need to prevent the users from bypassing the DLP policy. What should you configure?
A. incident reports
B. actions
C. exceptions
D. user overrides
Answer: D
Explanation:
A DLP policy can be configured to allow users to override a policy tip and report a false positive.
https://docs.microsoft.com/en-us/office365/securitycompliance/data-loss-prevention-policies
NEW QUESTION 497
You have a Microsoft 365 subscription. From the Security & Compliance admin center, you create a content search of all the mailboxes that contain the word Project X. You need to export the results of the content search. What do you need to download the report?
A. a certification authority (CA) certificate
B. an export key
C. a password
D. a user certificate
Answer: B
Explanation:
https://docs.microsoft.com/en-us/office365/securitycompliance/export-search-results
NEW QUESTION 498
You have a Microsoft 365 subscription. You recently configured a Microsoft SharePoint Online tenant in the subscription. You plan to create an alert policy. You need to ensure that an alert is generated only when malware is detected in more than five documents stored in SharePoint Online during a period of 10 minutes. What should you do first?
A. Enable Microsoft Office 365 Defender for Cloud Apps.
B. Deploy Windows Defender Advanced Threat Protection (Windows Defender ATP).
C. Enable Microsoft Office 365 Analytics.
Answer: A
Explanation:
https://docs.microsoft.com/en-us/cloud-app-security/use-case-admin-quarantine
NEW QUESTION 499
You have a Microsoft 365 subscription. You plan to enable Microsoft Azure Information Protection. You need to ensure that only the members of a group named PilotUsers can protect content. What should you do?
A. Run the Add-AadrmRoleBasedAdministrator cmdlet.
B. Create an Azure Information Protection policy.
C. Configure the protection activation status for Azure Information Protection.
D. Run the Set-AadrmOnboardingControlPolicy cmdlet.
Answer: D
Explanation:
If you don’t want all users to be able to protect documents and emails immediately by using Azure Rights Management, you can configure user onboarding controls by using the Set-AadrmOnboardingControlPolicy.
https://docs.microsoft.com/en-us/azure/information-protection/activate-service
NEW QUESTION 500
HotSpot
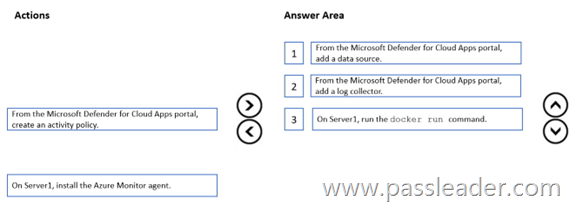
You have a Microsoft 365 E5 subscription. You need to use Microsoft Defender XDR to identify the following:
– Information-about known malicious organizations.
– Weekly open-source intelligence (OSINT) highlights.
Which two settings should you use in the Microsoft Defender portal? (To answer, select the appropriate settings in the answer area.)
Explanation:
Box 1: Microsoft Defender XDR provides information about known malicious organizations through its Threat Intelligence capabilities, specifically within the Threat Analytics dashboard. This dashboard offers insights into emerging threats, attack techniques, prevalent malware, and information about threat actors and campaigns.
Box 2: In Microsoft Defender XDR, weekly Open Source Intelligence (OSINT) highlights are available through Microsoft Defender Threat Intelligence (Defender TI). Specifically, Defender TI provides a feed of OSINT indicators, including file hashes, domains, IPs, and URLs, which can be downloaded and scanned against your environment. You can access Defender TI within the Microsoft Defender portal under Threat intelligence.
https://learn.microsoft.com/en-us/defender-xdr/investigate-incidents
https://www.microsoft.com/en-us/security/business/siem-and-xdr/microsoft-defender-threat-intelligence
NEW QUESTION 501
Drag and Drop
You have a Microsoft 365 E5 subscription and an on-premises server named Server1. You plan to configure automatic log upload for continuous reports in Microsoft Defender for Cloud Apps. You download a Docker log collector image to Server1. You need integrate Defender for Cloud Apps with the log collector. Which three actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
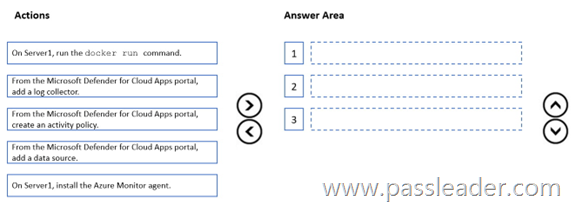
Explanation:
https://learn.microsoft.com/en-us/defender-cloud-apps/discovery-docker-windows
NEW QUESTION 502
……
Get the newest PassLeader MS-102 VCE dumps here: https://www.passleader.com/ms-102.html (509 Q&As Dumps –> 563 Q&As Dumps)
And, DOWNLOAD the newest PassLeader MS-102 PDF dumps from Cloud Storage for free: https://drive.google.com/drive/folders/1EgG1HXOLli3rw4OX-3NpXshMm5dHpomY