Valid 98-366 Dumps shared by PassLeader for Helping Passing 98-366 Exam! PassLeader now offer the newest 98-366 VCE dumps and 98-366 PDF dumps, the PassLeader 98-366 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader 98-366 dumps with VCE and PDF here: https://www.passleader.com/98-366.html (220 Q&As Dumps –> 261 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader 98-366 dumps from Cloud Storage: https://drive.google.com/open?id=0B-ob6L_QjGLpVVhXZTVKdDJpSnc
QUESTION 61
A node within a local area network (LAN) must have which two of the following? (Choose two.)
A. Username and password
B. Share name
C. NIC
D. IP address
E. Table of all network nodes
Answer: CD
Explanation:
A node must be able to access the LAN through a network interface. A node must also have an IP address.
QUESTION 62
Hotspot
You are configuring a wireless network with the Wireless Network Properties that are shown in the following image:

Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.
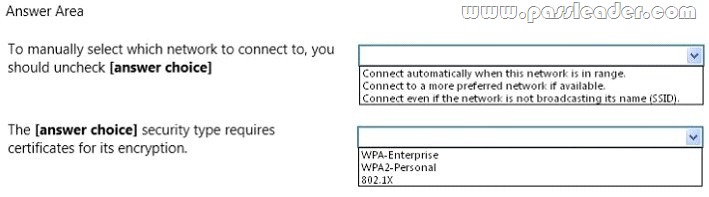
Answer:
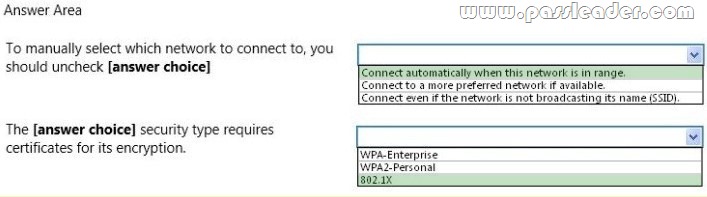
Explanation:
– Connect automatically when this network is in range. If you want to have a network in the list, but don’t want Windows to connect to it automatically, you can open up the properties from the Manage Wireless Networks dialog, and then uncheck the box for “Connect automatically when this network is in range”.
– 802.1x. This deployment scenario requires server certificates for each NPS server that performs 802.1X authentication.
QUESTION 63
This question requires that you evaluate the underlined text to determine if it is correct. Select the correct answer if the underlined text does not make the statement correct. Select ‘No change is needed” if the underlined text makes the statement correct.
A/anvirtual private network (VPN) protects a network’s perimeter by monitoring traffic as it enters and leaves.
A. Extranet
B. Firewall
C. Intranet
D. No change is needed
Answer: B
Explanation:
A firewall is software or hardware that checks information coming from the Internet or a network, and then either blocks it or allows it to pass through to your computer, depending on your firewall settings.
QUESTION 64
This question requires that you evaluate the underlined text to determine if it is correct. Select the correct answer if the underlined text does not make the statement correct. Select ‘No change is needed” if the underlined text makes the statement correct.
The loopback address of your computer is 127.0.0.1.
A. 10.0.1.1
B. 169.254.0.5
C. 192168.1.1
D. No change is needed
Answer: D
Explanation:
127.0.0.1 is the IPv4 loopback address.
QUESTION 65
You run the ipconfig command. The output is shown in the following image:

From these settings, you can tell that the computer ____.
A. will have limited Internet access
B. will have full Internet access
C. will not be able to access the Internet
D. will not be able to access the local network
Answer: A
QUESTION 66
Which IEEE 802.11 Wi-Fi networking standard requires dual antennas so it can run in all of its supported frequencies?
A. 802.11a
B. 802.11b
C. 802.11g
D. 802.11n
Answer: D
Explanation:
IEEE 802.11n-2009, commonly shortened to 802.11n, is a wireless networking standard that uses multiple antennas to increase data rates.
QUESTION 67
What is the bit rate for a North American T3 circuit?
A. 6.312 Mbit/s
B. 44.736 Mbit/s
C. 274.176 Mbit/s
D. 400.352 Mbit/s
Answer: B
Explanation:
Data Rates. DS3/T3 = 44.7 Mbps.
QUESTION 68
Hotspot
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

Answer:

Explanation:
– Dynamic Routing. A router with dynamically configured routing tables is known as a dynamic router. Dynamic routing consists of routing tables that are built and maintained automatically through an ongoing communication between routers.
– Most of the dominant routing algorithms are dynamic routing algorithms, which adjust to changing network circumstances by analyzing incoming routing update messages. If the message indicates that a network change has occurred, the routing software recalculates routes and sends out new routing update messages. These messages permeate the network, stimulating routers to rerun their algorithms and change their routing tables accordingly.
– When there are multiple routes to the same destination, a router must have a mechanism for calculating the best path. A metric is a variable assigned to routes as a means of ranking them from best to worst or from most preferred to least preferred.
QUESTION 69
Which feature of Category 5e STP cable reduces external interference?
A. Crosstalk
B. Shielding
C. Length
D. Twisting
Answer: D
Explanation:
Twisted pair cabling is a type of wiring in which two conductors of a single circuit are twisted together for the purposes of canceling out electromagnetic interference (EMI) from external sources.
QUESTION 70
What is an example of a network device that associates a network address with a port?
A. Switch
B. Router
C. Hub
D. DSL modem
Answer: B
Explanation:
A router is a Layer 3 gateway device, meaning that it connects two or more networks and that the router operates at the network layer of the OSI model.
Incorrect:
Not switch: Any switch that provides this ‘basic’ functionality, operates at the 2nd OSI layer also known as the Datalink Layer.
Not hub: A network hub, or a repeater, is a simple network device that does not manage any of the traffic coming through it. Any packet entering a port is flooded out or “repeated” on every other port, except for the port of entry.
QUESTION 71
Which wireless communication problem is caused by electromagnetic waves?
A. Fading
B. Attenuation
C. Interference
D. Diffraction
Answer: C
Explanation:
Because the air is shared by all transmitters, transmissions by any device at the same frequency as an access point’s radio can cause interference. Because 802.11 wireless networks operate in unlicensed bands used by many technologies, such as microwave ovens, video surveillance cameras, cordless phones, they are subject to interference.
QUESTION 72
An Action Center alert recommends that you enable Windows Firewall. After enabling the firewall, you can no longer access websites. Which two TCP ports should you add exceptions for on the firewall? (Choose two.)
A. Port 21
B. Port 23
C. Port 25
D. Port 80
E. Port 443
Answer: DE
Explanation:
– Port 80: HTTP.
– Port 443: HTTPS.
QUESTION 73
What are two advantages of using star topology rather than ring topology in a computer lab workgroup? (Choose two.)
A. Failure of a central connectivity device does not bring down the entire network.
B. A central connection point allows for flexibility and scalability.
C. Data travels on redundant paths, so one cable cannot stop its transmission.
D. A cable problem within the group affects two nodes, at most.
Answer: BD
QUESTION 74
What are three characteristics of Ethernet network topology? (Choose three.)
A. It uses tokens to avoid collisions on the network.
B. It can use coaxial, twisted pair, and fiber optic media.
C. It comprises the largest share of the networks in place today.
D. It is a non-switching protocol.
E. It can negotiate different transmission speeds.
Answer: BCE
Explanation:
B: Ethernet networks can use coax, twisted-pair, or fiber optic cabling.
C: Ethernet is the most widely used network topology.
E: Speed can be negotiated on Ethernet network.
Incorrect:
Not A: Tokes is used in ring topologies. The two possible topologies for Ethernet are bus and star.
Not D: A network topology is not a protocol. Switching can be performed on Ethernet networks.
QUESTION 75
This question requires that you evaluate the underlined text to determine if it is correct. Select the correct answer if the underlined text does not make the statement correct. Select ‘No change is needed” if the underlined text makes the statement correct.
Plain old telephone service (POTS), most ISDN lines, and switched T1 lines are all examples of Message Switching.
A. Circuit Switching
B. Packet Switching
C. FDDI Switching
D. No change is needed
Answer: A
QUESTION 76
Hotspot
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

Answer:

Explanation:
In computer security, a DMZ or demilitarized zone (sometimes referred to as a perimeter network) is a physical or logical subnetwork that contains and exposes an organization’s external-facing services to a larger and untrusted network, usually the Internet. The purpose of a DMZ is to add an additional layer of security to an organization’s local area network (LAN); an external network node only has direct access to equipment in the DMZ, rather than any other part of the network.
QUESTION 77
Hotspot
You are an intern for Contoso Ltd. Your supervisor asks you to configure the security zones for three new PCs so that they are able to connect to two web servers. The servers connect to the three new PCs as shown in the following image:
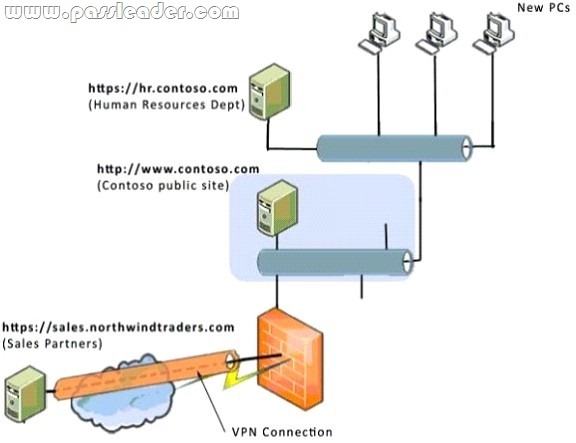
Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.

Answer:

Explanation:
– Trusted sites: The level of security set for Trusted sites is applied to sites that you have specifically indicated to be ones that you trust not to damage your computer or information.
– Local intranet: The level of security set for the Local intranet zone is applied to websites and content that is stored on a corporate or business network.
QUESTION 78
Your home computer is having problems accessing the Internet. You suspect that your Internet router’s DHCP service is not functioning, so you check your computer’s IP address. Which address indicates that your router’s DHCP service is NOT functioning?
A. 169.254.1.15
B. 172.16.1.15
C. 192.168.1.15
D. 10.19.1.15
Answer: A
Explanation:
169.254.1.15 is an APIPA address. An APIPA address is used when the DHCP server is not available.
QUESTION 79
Which of these is a public address space?
A. 192.168.0.0/16
B. 197.16.0.0/12
C. 10.0.0.0/8
D. 172.16.0.0/12
Answer: B
QUESTION 80
This question requires that you evaluate the underlined text to determine if it is correct. Select the correct answer if the underlined text does not make the statement correct. Select ‘No change is needed” if the underlined text makes the statement correct.
In a wireless network that requires an SSL certificate, WEP handles the SSL certificate.
A. 802.1X
B. WPA2-PSK
C. WPA-PSK
D. No change is needed
Answer: A
Explanation:
This deployment scenario requires server certificates for each NPS server that performs 802.1X authentication.
Get the newest PassLeader 98-366 VCE dumps here: https://www.passleader.com/98-366.html (220 Q&As Dumps –> 261 Q&As Dumps)
And, DOWNLOAD the newest PassLeader 98-366 PDF dumps from Cloud Storage for free: https://drive.google.com/open?id=0B-ob6L_QjGLpVVhXZTVKdDJpSnc