Valid 70-486 Dumps shared by PassLeader for Helping Passing 70-486 Exam! PassLeader now offer the newest 70-486 VCE dumps and 70-486 PDF dumps, the PassLeader 70-486 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader 70-486 dumps with VCE and PDF here: http://www.passleader.com/70-486.html (232 Q&As Dumps –> 270 Q&As Dumps –> 291 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader 70-486 dumps from Cloud Storage: https://drive.google.com/open?id=0B-ob6L_QjGLpflNtUWtkNlk3ODJFY0pqOUhqVFEwc0lrd0QtamRxUHFLLUdWZEVDaGtlQWM
QUESTION 127
You are developing an ASP.NET MVC application that uses forms authentication. Authentication credentials must be encrypted and secure. You need to ensure that user credentials are persisted after users log on. Where should you store the credentials? (Each correct answer presents a complete solution. Choose all that apply.)
A. In TempData
B. In Session
C. In ViewData
D. In a cookie
Answer: BD
QUESTION 128
You are developing an ASP.NET MVC application to be used on the Internet. The environment uses Active Directory with delegation to access secure resources. Users must be able to log on to the application to maintain their personal preferences. You need to use the least amount of development effort to enable users to log on. What should you do?
A. Enable Windows authentication.
B. Generate server SSL certificates and install them in IIS.
C. Enable Digest authentication.
D. Enable Forms authentication.
Answer: A
Explanation:
Requirements for Delegation. Delegation relies on Integrated Windows authentication to access resources. There is no limit on the number of computers that you can delegate your account — you must correctly configure each of them. The Integrated Windows authentication method works only if the following two conditions exist:
– You set up your network to use the Kerberos authentication protocol that requires Active Directory.
– You set up the computers and accounts on your network as trusted for delegation.
QUESTION 129
You are desinging a distributed application. The application must store secure information that is specific to an individual user. The data must be automatically purged when the user logs off. You need to save transient information in a secure data store. Which date store should you use?
A. profile properties
B. session state
C. database storage
D. application state
Answer: B
Explanation:
Use ASP.NET session state to store and retrieve values for a user.
Secure Session-State Configuration
When storing sensitive information in a configuration file for an application, you should encrypt the sensitive values using Protected Configuration. Information that is especially sensitive includes the encryption keys stored in the machine Key configuration element and data source connection strings stored in the connection Strings configuration element.
QUESTION 130
You are developing an application. One requirement is that part of your data access layer needs to be available to a third party, that wants to get this information from a REST URL in XML. Your company does not have experience with web services, but you have several websites running ASP.NET MVC 4. How could you design and provide these new services? (Choose all that apply.)
A. Task an individual on staff to learn WCF, and have this individual develop and deploy these new services using WCF.
B. Use the Web API to create REST services using ApiController in which the serialization type is defined by the Accepts property of the browser.
C. Build a basic ASP.NET MVC 4 project in which the view simply passes through the information provided by the controller, and the controller manages the code for serializing the response.
D. Create an ASP.NET ASMX services file to get, serialize, and return the data.
Answer: BC
QUESTION 131
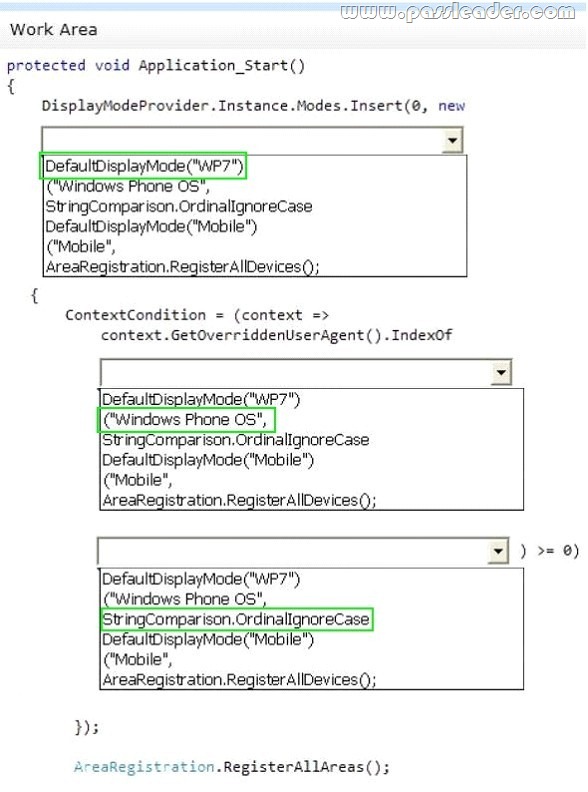
Hotspot Question
You are developing an ASP.NET MVC application that has pages for users who browse the site with Windows Phone 7. The pages for Windows Phone 7 include the following files:
– _Layout.WP7.cshtml
– Index.WP7.cshtml
You need to update the application so that it renders the customized files correctly to Windows Phone 7 users. How should you update the Application_Start method? (To answer, select the appropriate option from the drop-down list in the answer area.)
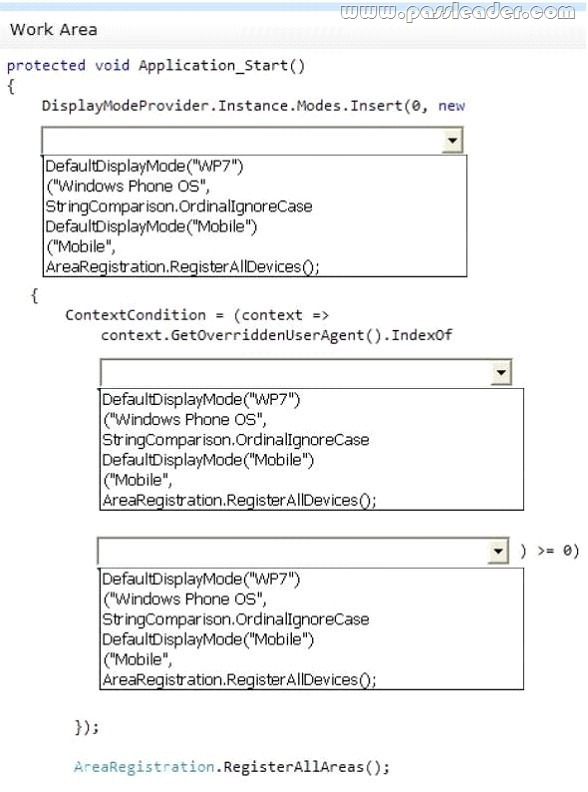
QUESTION 132
You are designing a distributed banking application that handles multiple customers. A user may log on to the site to perform activities such as checking balances, performing transactions, and other activities that must be done securely. The application must store secure information that is specific to an individual user. The data must be automatically and securely purged when the user logs off. You need to save transient information in a secure data store. Which data store should you use?
A. .NET session state
B. .NET profile properties
C. .NET application state
D. Shared database
Answer: A
QUESTION 133
You are developing an ASP.NET MVC application that supports multiple cultures and multiple languages. The application will be sold to international customers. The ASP.NET MVC application must store localized content in satellite assemblies for multiple languages. You need to generate the satellite assemblies during an automated build. Which tool should you use?
A. Gacutil.exe
B. Al.exe
C. Ildasm.exe
D. nasm.exe
Answer: B
Explanation:
Use the Assembly Linker (Al.exe) to compile .resources files into satellite assemblies. Al.exe creates an assembly from the .resources files that you specify. By definition, satellite assemblies can only contain resources. They cannot contain any executable code.The following Al.exe command creates a satellite assembly for the application MyApp from the file strings.de.resources. al /t:lib /embed:strings.de.resources /culture:de /out:MyApp.resources.dll
QUESTION 134
You are preparing for the deployment of an ASP.NET MVC application. You need to generate a deployment manifest. Which command-line tool should you use?
A. Mage.exe
B. Ngen.exe
C. AL.exe
D. Resgen.exe
Answer: A
Explanation:
https://msdn.microsoft.com/en-us/library/vstudio/dd233108(v=vs.100).aspx
QUESTION 135
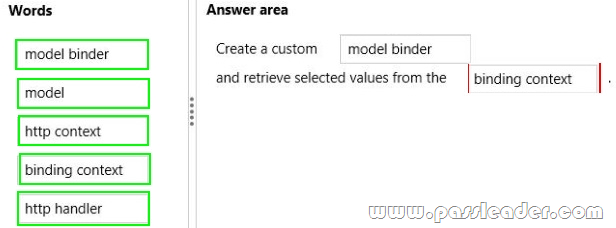
Drag and Drop Question
You are developing an ASP.NET MVC application. The application has a view that displays a list of orders in a multi-select list box. You need to enable users to select multiple orders and submit them for processing. What should you do? (To answer, drag the appropriate words to the correct targets. Each word may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)

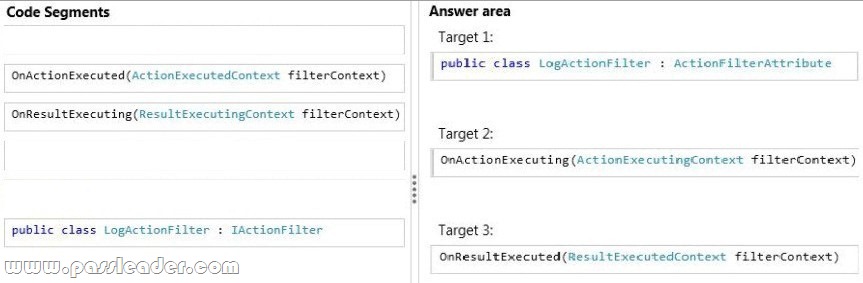
QUESTION 136
Drag and Drop Question
You are developing an ASP.NET MVC application. Before an action is executed, information about the action must be written to a log. After results are returned, information about the results also must be written to the log. You need to log the actions and results. You have the following code:

Which code segments should you include in Target 1, Target 2 and Target 3 to implement the LogActionFilter class? (To answer, drag the appropriate code segments to the correct targets. Each code segment may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
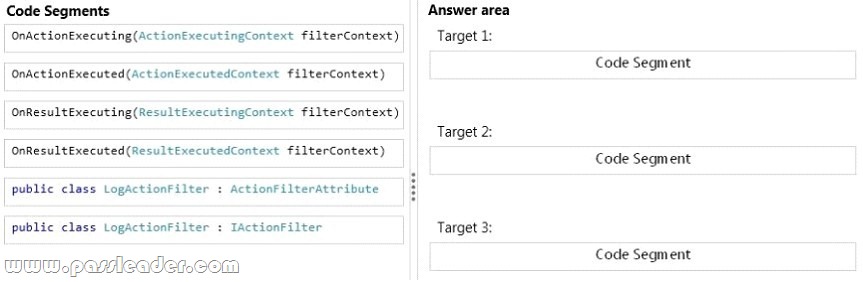
QUESTION 137
Hotspot Question
You are optimizing an Internet-facing website for search engine optimization. You are reading a Site Analysis Report from the SEO Toolkit. The report returns warnings that indicate the website HTML lacks key information necessary for search engine indexing. You need to improve the optimization of the site. What should you do? (To answer, select the appropriate option from the drop-down list in the answer area.)

QUESTION 138
You are designing a data-oriented application that features a variety of storage schemas. The application object model must be mapped to the various storage schemas. You need to enable developers to manipulate the data. Which ADO.NET data access strategy should you use? (Each correct answer presents a complete solution. Choose all that apply.)
A. LINQ to SQL
B. Entity Framework
C. DataAdapter
D. DataReader
Answer: ABC
QUESTION 139
You are developing an ASP.NET MVC application that provides instant messaging capabilities to customers. You have the following requirements:
– Messages must be able to be sent and received simultaneously.
– Latency and unnecessary header data must be eliminated.
– The application must comply with HTML5 standards.
You need to design the application to meet the requirements. What should you do?
A. Configure polling from the browser.
B. Implement long-running HTTP requests.
C. Implement WebSockets protocol on the client and the server.
D. Instantiate a MessageChannel object on the client.
Answer: D
QUESTION 140
You are developing an ASP.NET MVC application that uses forms authentication to verify that the user is logged in. Authentication credentials must be encrypted and secure so no user identity is exposed. You need to ensure that user credentials are persisted after users log on. Where should you store the credentials? (Each correct answer presents a complete solution. Choose all that apply.)
A. In Session on the server
B. In a cookie stored in the browser
C. In ViewData in the application
D. In TempData on the server
Answer: AB
QUESTION 141
You are developing an ASP.NET MVC application that uses forms authentication. The application uses SQL queries that display customer order data. Logs show there have been several malicious attacks against the servers. You need to prevent all SQL injection attacks from malicious users against the application. How should you secure the queries?
A. Check the input against patterns seen in the logs and other records.
B. Escape single quotes and apostrophes on all string-based input parameters.
C. Implement parameterization of all input strings.
D. Filter out prohibited words in the input submitted by the users.
Answer: C
Explanation:
SQL Injection Prevention, Defense Option 1: Prepared Statements (Parameterized Queries). The use of prepared statements (aka parameterized queries) is how all developers should first be taught how to write database queries. They are simple to write, and easier to understand than dynamic queries. Parameterized queries force the developer to first define all the SQL code, and then pass in each parameter to the query later. This coding style allows the database to distinguish between code and data, regardless of what user input is supplied.Prepared statements ensure that an attacker is not able to change the intent of a query, even if SQL commands are inserted by an attacker.
Reference: SQL Injection Prevention Cheat Sheet
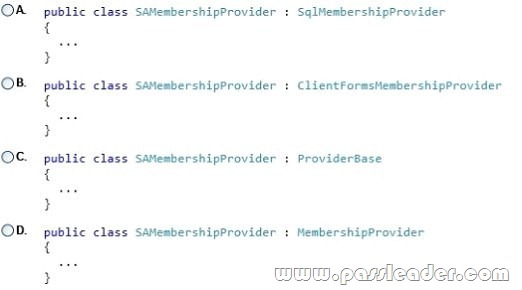
QUESTION 142
You are developing an ASP.NET MVC application that uses forms authentication against a third-party database. You need to authenticate the users. Which code segment should you use?
A. Option A
B. Option B
C. Option C
D. Option D
Answer: D
Explanation:
To implement a custom membership provider, you need to inherit the MembershipProvider abstract class from the System.Web.Security namespace. The MembershipProvider abstract class inherits the ProviderBase abstract class from the System.Configuration.Provider namespace, so you must implement the required members of the ProviderBase class as well.
QUESTION 143
You are designing an enterprise-level Windows Communication Foundation (WCF) application. User accounts will migrate from the existing system. The new system must be able to scale to accommodate the increasing load. You need to ensure that the application can handle large-scale role changes. What should you use for authorization? (Each correct answer presents a complete solution. Choose all that apply.)
A. Resource-based trusted subsystem model
B. Identity-based approach
C. Role-based approach
D. Resource-based impersonation/delegation model
Answer: BC
Explanation:
Advanced Maturity: Authorization as a Service
In the advanced level of maturity for authorization, role storage and management is consolidated and authorization itself is a service available to any solution that is service- enabled.

The Trusted Subsystems Model
Once authorization is available as an autonomous service, the need for impersonation is eliminated. Instead of assuming the identity of the user, the application uses its own credentials to access services and resources, but it captures the user’s identity and passes it as a parameter (or token) to be used for authorization when a request is made. This model is referred to as the trusted subsystem model, because the application acts as a trusted subsystem within the security domain.
QUESTION 144
Drag and Drop Question
You are building an ASP.NET MVC web application. The application will be viewed by users on their mobile phones. You need to ensure that the page fits within the horizontal width of the device screens. You have the following markup:

Which markup segments should you include in Target 1, Target 2 and Target 3 to complete the markup? (To answer, drag the appropriate markup segments to the correct targets. Each line of code may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
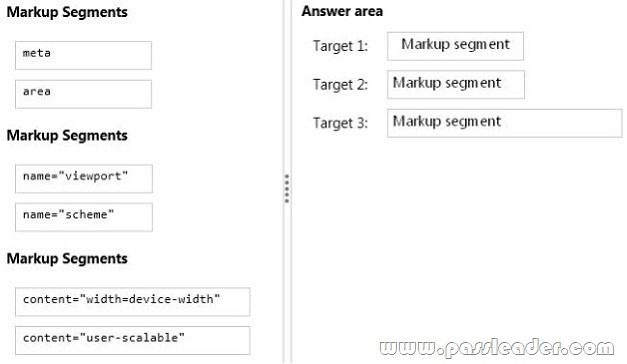
Get the newest PassLeader 70-486 VCE dumps here: http://www.passleader.com/70-486.html (232 Q&As Dumps –> 270 Q&As Dumps –> 291 Q&As Dumps)
And, DOWNLOAD the newest PassLeader 70-486 PDF dumps from Cloud Storage for free: https://drive.google.com/open?id=0B-ob6L_QjGLpflNtUWtkNlk3ODJFY0pqOUhqVFEwc0lrd0QtamRxUHFLLUdWZEVDaGtlQWM