Valid 70-341 Dumps shared by PassLeader for Helping Passing 70-341 Exam! PassLeader now offer the newest 70-341 VCE dumps and 70-341 PDF dumps, the PassLeader 70-341 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader 70-341 dumps with VCE and PDF here: http://www.passleader.com/70-341.html (261 Q&As Dumps –> 272 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader 70-341 dumps from Cloud Storage: https://drive.google.com/open?id=0B-ob6L_QjGLpfjZ2U1ZfVEZvU0ZreTJkNG1xdmxjS0xUYkdHWVMxWFNRVDhOYTlyRzBjOXM
QUESTION 21
Drag and Drop Question
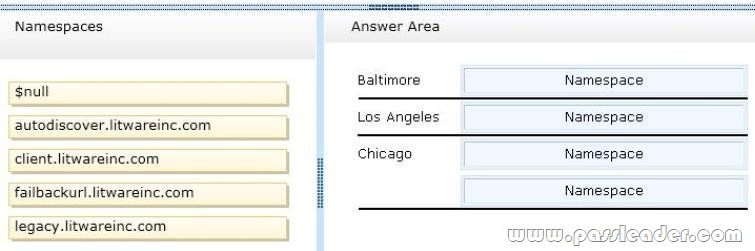
You need to identify which external namespaces must be used for the Exchange servers in each office. Which external namespaces should you identify for each office? To answer, drag the appropriate namespace to the correct office in the answer area. Each namespace may be used once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.
Case Study 3: A.Datum Corporation (QUESTION 22 ~ QUESTION 30)
Overview
A. Datum Corporation is an airline catering company that has 8,000 users. A. Datum has three main offices. The offices are located in Detroit, Chicago, and New York.
Existing Environment
Active Directory Environment
The network contains an Active Directory forest named adatum.com. The forest contains a single domain. All domain controllers run Windows Server 2012. Each main office contains two domain controllers. Each office is configured as an Active Directory site. The functional level of the forest is Windows Server 2012.
Network Infrastructure
The offices connect to each other by using a dedicated WAN link. Only the office in New York and the office in Detroit connect directly to the Internet. Each office has a firewall. The public DNS records for A. Datum are configured as shown in the following table.
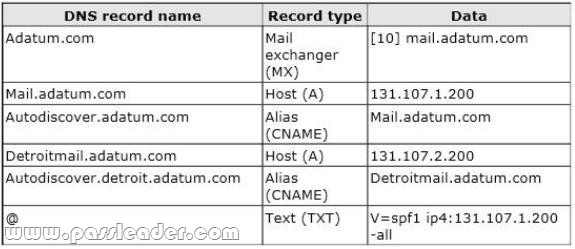
The external interface for the firewall in the New York office is configured to use an IP address of 131.107.1.200 and to pass inbound traffic on port 25 and port 443 to EX2. The external interface for the firewall in the Detroit office is configured to use an IP address of 131.107.2.200 and to pass inbound traffic on port 443 to EX4. The Active Directory site is configured as shown in the Sites exhibit. (Click the Exhibit button.)
Exchange Server Organization
A. Datum has an Exchange Server 2013 organization that contains two servers. The servers are configured as shown in the following table.

Each server contains 15 mailbox databases. Users use the name mail.adatum.com to connect to their mailbox from the Internet. The users use the FQDN of the servers to connect from the internal network. AM of the users in the Detroit office have a mailbox hosted on EX2. The default email address policy contains a single email address format of @adatum.com. A separate Send connector exists for the Chicago office and the New York office. The local servers in each office are the only source servers in each Send connector. The New York office is configured as a hub site. Antimalware filtering is disabled on EX1 and EX2.
Problem Statements
A. Datum identifies the following issues:
– Users in the Detroit office report that sometimes, Microsoft Outlook takes a long time to open.
– During a recent storage failure, administrators failed to restore the latest backup and lost all of the email messages from the previous 48 hours.
– Users report that the email messages sent to some Internet domains are not received. Users in the Chicago office report that some of their email messages generate a non-delivery report (NDR).
– The help desk in the New York office reports that its most common Exchange-related task is to restore email messages that were deleted by users more than 14 days ago. The task requires time-consuming restore operations by the help desk.
Requirements
Business Requirements
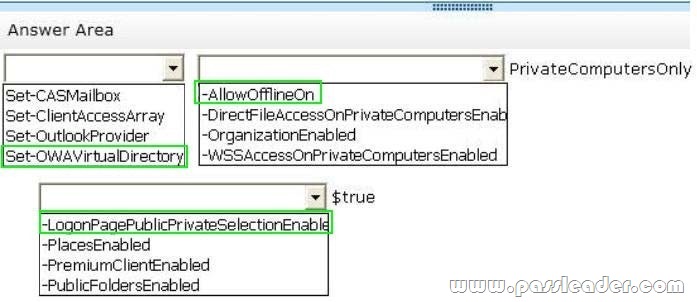
A. Datum wants to provide users with the ability to access their email from Internet Explorer 10, even when the users are disconnected from the network. This ability must only be available if the users log on to Outlook Web Access by using the Private option.
Planned Changes
You plan to deploy three additional Exchange Server 2013 servers. The servers will be configured as shown in the following table.

After the planned deployment, all of the mailboxes of the Detroit office users will be moved to EX3. All of the Detroit office users will use the name detroitmail.adatum.com when they connect from the Internet and the name ex4.adatum.com when they connect from the internal network.
Technical Requirements
A. Datum identifies the following technical requirements:
– All existing and future mailboxes must be limited to 5 GB of storage.
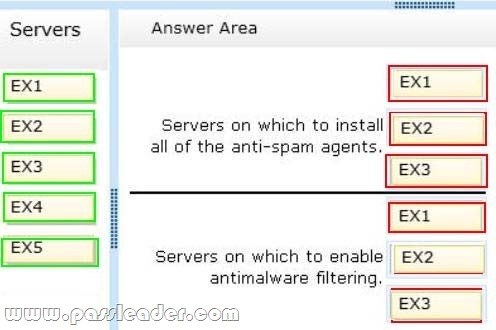
– Antimalware and anti-spam filtering must be enabled for the entire Exchange Server organization.
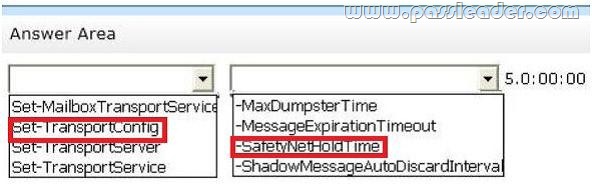
– If storage for the mailbox database fails, administrators must be able to recover email messages handled by transport services for to the last five days.
– Only the members of a group named Executives must be able to schedule meetings in a room mailbox named Boardroom. Meeting requests must not be moderated.
– All of the servers in the New York office that have the Client Access server role installed must be accessed by using a load balancing solution that can mark a server as down ifa specific URL on the server is unavailable.
Mailbox Creation Requirements
A. Datum identifies the following requirements for creating new mailboxes:
– All mailboxes must automatically have single item recovery enabled.
– All mailboxes must automatically have the Exchange ActiveSync feature disabled.
QUESTION 22
Hotspot Question
You need to recommend a solution to meet the technical requirements for mailbox size restrictions.
Which command should you include in the recommendation? (To answer, select the appropriate options in the answer area.)

QUESTION 23
Drag and Drop Question
You need to recommend a solution to meet the technical requirements for email message recovery. Which command should you include in the recommendation? (To answer, configure the appropriate options in the answer area.)

QUESTION 24
You are evaluating the planned deployment of the additional Exchange Server 2013 servers. You need to recommend changes to the DNS records to ensure that email messages are routed to the Detroit site if the servers in the New York site are unavailable. What should you recommend adding?
A. An MX record that has a preference value of 10 that points to EX4
B. An MX record that has a preference value of 20 that points to EX4
C. An MX record that has a preference value of 10 that points to EX3
D. An MX record that has a preference value of 20 that points to EX3
Answer: B
Explanation:
NOT ACD
Need to change the value of the MX record to achieve the desired result. Need to have a preference value greater for the 2nd preferred exchange mail server (Detroit) than the 1st preferred mail server (New York). That is it needs to point to the Detroit mail server (EX4) only if the New York mail server is unavailable.
B
Need to point to EX4 and have a higher preference value than 10 (The default value of New York mail server MX record).
QUESTION 25
You need to recommend a solution to resolve the issue of email messages not being received on the Internet. What should you include in the solution?
A. Modify the CNAME record.
B. Add an MX record.
C. Modify the TXT record.
D. Add a pointer (PTR) record.
Answer: D
Explanation:
Detroit and New York users have direct connection to the internet but not Chicago users. It appears that via a Send Connector Chicago email is sent to New York mail server. Given this then the spf txt record listing the New York mail server is correct (131.107.1.200) and there should not be any issues with the Chicago email Once the planned changes have been implemented then the DNS txt record would have to accommodate the Detroit Mail server (EX3) (131.107.2.200) in order for the email to function correctly for Detroit users. However the question relates to Chicago users not Detroit users.
CNAME record.
A Canonical Name or CNAME record is a type of DNS record that links an alias name to another canonical domain name. You’ll need to configure CNAME records if you want to use URL forwarding to create a custom web address, forward a URL to Google Sites, or forward a naked domain URL, as well as verify your site with your domain name provider. Lastly, you may need to use CNAME records to reset the administrator password if you can’t access the Google Apps control panel because you’ve forgotten the administrator password. Your CNAME records are stored in the DNS Zone File as pairs of key values. The value of a CNAME record is always a domain name. CNAME records are often used to create subdomains. CNAME records are useful because they allow you to set up an alias to a server without using its IP address, through an intermediary standard domain name.
MX Record.
MX records are DNS settings associated with your domain that direct its mail to the servers hosting your users’ mail accounts. These settings are managed by your domain host, not by Google. To make sure mail always gets delivered, you typically create records for multiple servers, all of which can deliver mail to users. That way, if one server is down, mail can be routed to another server, instead. You determine which servers get tried first by assigning priorities, using values like 10, 20, 30, and so on. The lowest value gets highest priority.
PTR Record.
A DNS PTR record -for those of you who are wondering -is a special entry in the Domain Name System (DNS) that basically maps an IP address (like 65.55.12.249) to a domain name (like wwwco2vip.microsoft.com). Having a DNS PTR record for your IP address is (somewhat) a sign of reliability in the Internet, since only the owner of a specific network zone has the ability to create and edit these DNS records. Today, most mail exchangers will check this record for each incoming connection and may abort the communication if they find your IP address does not have an associated DNS PTR entry: because of this reason, always suggest to make sure your public servers IP addresses have DNS PTR records configured properly. While EmailVerify.NET can validate email addresses even without a DNS PTR entry configured, the quality of the validation results in this event may be suboptimal.
TXT Record.
A TXT record is an entry within the Domain Name System (DNS) that provides supplemental information about your domain. A TXT (text) record is used to hold some text information. You can put virtually any free text you want within a TXT record. A TXT record has a hostname so that you can assign the free text to a particular hostname/zone. The most common use for TXT records is to store SPF (sender policy framework) records and to prevent emails being faked to appear to have been sent from you. The name field of the SPF record should be left blank unless mail is sent from a subdomain such as [email protected]. If this was the case “mail” would be entered in the name field of the record. Alternatively, of email is sent from [email protected], the name field is left blank. The data field of the record is populated with the list of hosts that are permitted to send email for the domain in SPF record format. There are wizards which can assist in generating an SPF record available. The data field of the record must be enclosed in quotations so servers will read the value as a single string. Below is a default SPF record for example-1.com.

NOT A
Today, most mail exchangers will check this record for each incoming connection and may abort the communication if they find your IP address does not have an associated DNS PTR entry: need a ptr record.
NOT B
Today, most mail exchangers will check this record for each incoming connection and may abort the communication if they find your IP address does not have an associated DNS PTR entry: need a ptr record.
NOT C
Need to modify the txt record for Detroit email users but not apparently for chicago email users.
D
Today, most mail exchangers will check this record for each incoming connection and may abort the communication if they find your IP address does not have an associated DNS PTR entry: need a ptr record. Managing DNS Records.
QUESTION 26
You need to recommend a solution for the New York office that meets the technical requirements for client access. What should you include in the recommendation? (Each correct answer presents a complete solution. Choose all that apply.)
A. A Layer 4 hardware load balancer
B. A Client Access server array
C. A Layer 7 hardware load balancer
D. The Network Load Balancing (NLB) feature
E. DNS round robin
Answer: AC
Explanation:
Load Balancing: Exchange 2013 Help.
QUESTION 27
You need to recommend a solution to meet the mailbox creation requirements. Which three actions should you recommend performing in sequence? (To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.)

Answer:

Explanation:
Edit the ScriptingAgentConfig.xml.sample file, and then rename the file as ScriptingAgentConfig.xml. Copy the ScriptingAgentConfig.xml file to all of the Mailbox servers Run the Enable-CmdletExtensionAgent “Scripting Agent” command.
http://technet.microsoft.com/en-us/library/dd335054(v=exchg.150).aspx
Cmdlet Extension Agents.
Cmdlet extension agents are components in Microsoft Exchange Server 2013 invoked by Exchange cmdlets when the cmdlets run. As the name implies, cmdlet extension agents extend the capabilities of the cmdlets that invoke them by assisting in processing data or performing additional actions based on the requirements of the cmdlet. Cmdlet extension agents are available on any server role. Agents can modify, replace, or extend functionality of Exchange Management Shell cmdlets. An agent can provide a value for a required parameter that isn’t provided on a command, override a value provided by a user, perform other actions outside of the cmdlet workflow while a cmdlet runs, and more. You can use the Scripting agent cmdlet extension agent in Exchange 2013 to insert your own scripting logic into the execution of Exchange cmdlets. Using the Scripting agent, you can add conditions, override values, and set up reporting. Every time an Exchange cmdlet is run, the cmdlet invokes the Scripting agent cmdlet extension agent. When this agent is invoked, the cmdlet checks whether any scripts are configured to be invoked by the cmdlet. If a script should be run for a cmdlet, the cmdlet tries to invoke any APIs defined in the script. The Scripting agent configuration file contains all the scripts that you want the Scripting agent to run. Scripts in the configuration file are contained within XML tags that define the beginning and end of the script and various input parameters required to pass data to the script. Scripts are written using Windows PowerShell syntax. The configuration file is an XML file that uses the elements or attributes in the following table. Every Exchange 2013 server includes the file ScriptingAgentConfig.xml.sample in the <installation path>\V15\Bin\CmdletExtensionAgents folder. This file must be renamed to ScriptingAgentConfig.xml on every Exchange 2013 server if you enable the Scripting Agent cmdlet extension agent. The sample configuration file contains sample scripts that you can use to help you understand how to add scripts to the configuration file. After you add a script to the configuration file, or if you make a change to the configuration file, you must update the file on every Exchange 2013 server in your organization. This must be done to make sure that each server contains an up-to-date version of the scripts that the Scripting Agent cmdlet extension agent runs.
ScriptingAgentConfig.xml
Renamed from ScriptingAgentConfig.xml.sample on every Exchange 2013 server if you enable the Scripting Agent cmdlet extension agent.
ScrptingAgentConfig.xml.sample
Every Exchange 2013 server includes the file ScriptingAgentConfig.xml.sample in the <installation path>\V15\Bin\CmdletExtensionAgents folder. This file must be renamed to ScriptingAgentConfig.xml on every Exchange 2013 server if you enable the Scripting Agent cmdlet extension agent. The sample configuration file contains sample scripts that you can use to help you understand how to add scripts to the configuration file.
Enable-CmdletExtensionAgent “Scripting Agent” command.
Use the Enable-CmdletExtensionAgent cmdlet on a server running Microsoft Exchange Server 2013 to enable a cmdlet extension agent.
EXAMPLE 1
This example enables the Scripting Agent cmdlet extension agent. Before you enable the Scripting Agent, you need to make sure that you’ve first deployed the ScriptingAgentConfig.xml configuration file to all the servers in your organization. If you don’t deploy the configuration file first and you enable the Scripting Agent, all non-Get cmdlets fail when they’re run.
Enable-CmdletExtensionAgent “Scripting Agent”
Run the Set-CmdletExtensionAgent “Scripting Agent” command Use the Set-CmdletExtensionAgent cmdlet on a server running Microsoft Exchange Server 2013 to modify a cmdlet extension agent.
EXAMPLE 1
This example changes the priority of the fictitious “Validation Agent” cmdlet extension agent to 9. Set-CmdletExtensionAgent “Validation Agent” -Priority 9 STEPS
1. Edit the ScriptingAgentConfig,xml.sample file, and then rename the file as ScriptingAgentConfig.xml. Need to add in your own appropriate scripts.
2. Copy the ScriptingAgentConfig.xml file to all of the Mailbox Servers The question refers to mailbox creation requirements but according to the above information – After you add a script to the configuration file, or if you make a change to the configuration file, you must update the file on every Exchange 2013 server in your organization. In the absence of further information, accept updating the mailbox servers over the client access servers.
3. Enable- CmdletExtensionAgent “Scripting Agent” command Have to enable the cmdlet extension agent.
QUESTION 28
Hotspot Question
You need to recommend a solution to meet the business requirements for users accessing their email messages. Which command should you include in the recommendation? (To answer, select the appropriate options in the answer area.)
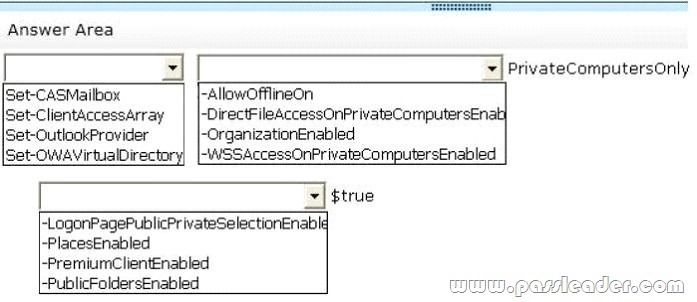
QUESTION 29
Drag and Drop Question
You are evaluating the planned deployment of the additional Exchange Server 2013 servers. You need to meet the technical requirement for installing all of the anti-spam agents and for enabling antimalware filtering. What should you do? (To answer, drag the appropriate servers to the correct locations. Each server may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
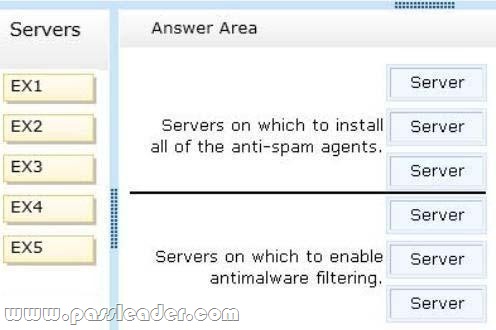
QUESTION 30
You are evaluating the deployment of the additional Exchange Server 2013 servers. You need to recommend changes to the transport configurations to ensure that all email messages sent from the Detroit office are routed through EX2. What should you include in the recommendation?
A. Increase the cost of the CHI-NY site link to 15.
B. Specify an Exchange-specific cost of 20 for the CHI-DET site link.
C. Decrease the cost of the CHI-NY and the DET-NY site links to 4.
D. Increase the cost of the DET-NY site link to 15.
Answer: B
Explanation:
Exchange-specific cost.
By default, Exchange uses the cost assigned to an IP site link for Active Directory replication purposes to compute a routing topology.

Route Mail Between Active Directory Sites: Exchange 2013 Help.
NOT ACD
Need to introduce an exchange specific cost not change and AD cost B. You need to recommend changes to the transport configurations to ensure that all email messages sent from the Detroit office are routed through EX2. All of the Detroit Users have a mailbox hosted on EX2 currently (New York). After the planned changes all of Detroit mailboxes would be shifted to EX3 (Detroit). The office in New York and Detroit connect to the internet directly. In order to change the transport configuration to ensure that all email messages sent from the Detroit office are routed through EX2 an exchange specific cost has to be implemented. B is the only answer option which achieves this.
[A40]
1. Run the New-Mailbox cmdlet
2. Run the New-ManagementRole -ParentMyContactInformation -Name Role1
3. Run the Remove-ManagementRoleEntryRole1 Set-User command
4. Run the Add-ManagementRoleEntry Role1Set-User-Parameters Office, Homephone
5. Run the New-RoleAssignmentPolicy -Name Policy1 -Roles MyBaseOptions, Role1, MyVoiceMail, MyTextMessages, MyTeamMailboxes, MyMarketPlaceApps, MyDistributionGroupMembership
Case Study 4: Proseware, Inc. (QUESTION 31 ~ QUESTION 37)
Overview
General Overview
Proseware, Inc., is an international manufacturing company that has 3,000 users. Proseware has a sales department, a marketing department, a research department, and a human resources department. Proseware recently purchased a small competitor named Contoso, Ltd.
Physical Locations
Proseware has two offices. The offices are located in New York and London. The offices connect to each other by using a WAN link. Each office connects directly to the Internet. Contoso has one office in Chicago.
Existing Environment
Active Directory Environment
The network of Proseware contains an Active Directory forest named proseware.com. The forest contains a single domain and two sites named London and New York. Each site contains two domain controllers that run Windows Server 2008 R2. The domain controllers in the New York site are named DC1 and DC2. The domain controllers in the London site are named DC3 and DC4. All FSMO roles are hosted on DC3 and DC4. The network of Contoso contains an Active Directory forest named contoso.com. The forest contains five domain controllers and one site.
Exchange Server Organization
Proseware has an Exchange Server 2013 organization that contains two database availability groups (DAGs) named DAG-NYC and DAG-LON. The DAGs are configured as shown in the following table.
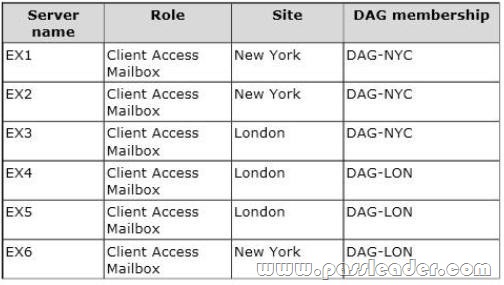
The certificate used for Exchange Server 2013 has a subject name of mail.proseware.com and a Subject Alternative Name (SAN) of autodiscover.proseware.com. Each mailbox database has three copies. All users connect to an active copy of the database on a server in their respective office. Native data protection is implemented. NTLM communication is used exclusively for Outlook Anywhere both internally and externally.
Problem Statements
Proseware identifies the following issues:
– Users report that sometimes, they fail to access the free/busy information of the other users. You also discover that some users fail to retrieve Autodiscover settings.
– Users in the London office report that during a 24-hour WAN outage, they could see only new users in the global address list (GAL) from Outlook Web App.
– The manager of the human resources department in the New York office cannot see new London office users in the GAL until several hours after the help desk confirms that the users were created.
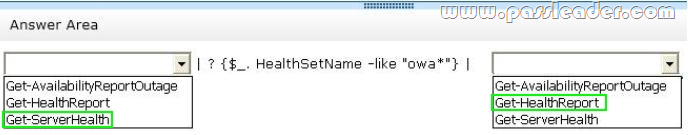
– A hung MSExchangeOWAAppPool in Internet Information Services (IIS) on EX1 causes all of the database copies to fail over. Despite having the same CopyQueueLength and ReplayQueueLength as the copies on EX2, the copies on EX3, which have a higher activation preference, are activated, forcing user connections over the WAN.
– A custom application named Appl recently malfunctioned and sent hundreds of false positive email notifications that had a subject of System Alert: Sales Database Reaching Capacity to all of the users in the organization. While attempting to remove the email messages, an administrator ran the Search-Mailbox -DeleteContent command and erroneously deleted valid email messages from the mailboxes of some executives.
Requirements
Business Goal
Proseware identifies the following business goals:
– Reduce the costs associated with using bandwidth on the WAN links.
– Improve social media integration by using a Microsoft Outlook app that will be deployed to all of the users in the sales department.
Planned Changes
Proseware plans to make the following changes:
– Implement a lagged copy for the mailbox database of the executives.
– Implement an RBAC-linked role group for the administrators at Contoso to manage the mailboxes of the Proseware users.
Technical Requirements
Proseware identifies the following technical requirements:
– End users must be notified after one hour if the email messages that they send are not delivered.
– If mailbox database storage fails, the IT department must be able to recover old email messages that were sent up to five days earlier to the mailboxes of the executives.
– All new users hired at Contoso must have a user account in contoso.com and an Exchange Server mailbox in proseware.com. All new user accounts in contoso.com must have a user principal name (UPN) that ends with proseware.com.
– Administrators at Contoso must be able to create and manage recipient objects in the Exchange Server organization of Proseware by using their existing contoso.com administrator account. All Contoso recipient objects must reside in an organizational unit (OU) named proseware.com.
Security Requirements
The Chief Security Officer (CSO) introduces the following security requirements:
– All Outlook users who connect from the Internet must use Basic authentication only.
– All Outlook users who connect from the internal network must use NTLM authentication only.
SLA Requirements
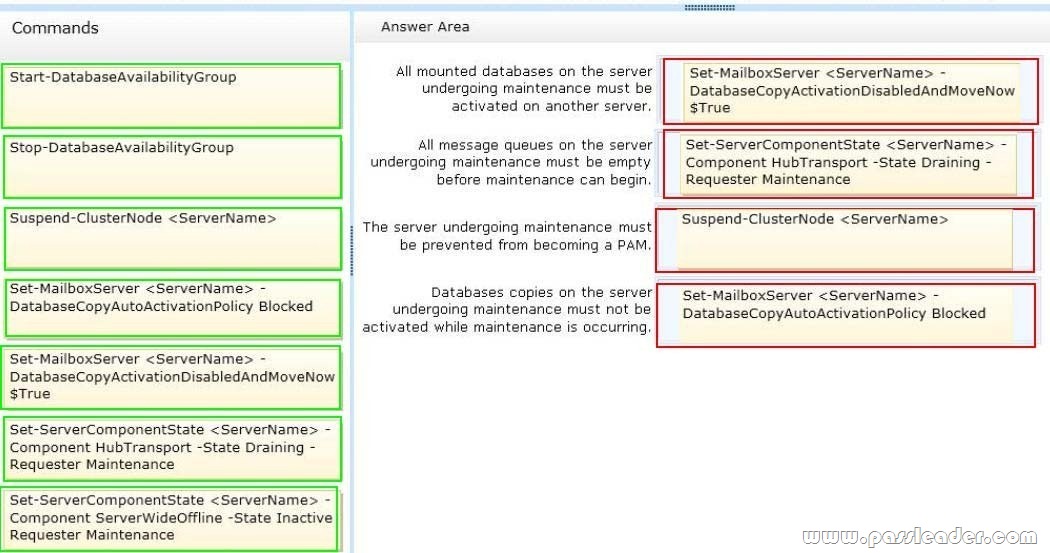
Due to productivity losses during some recent maintenance windows, the Chief Information Officer (CIO) introduces a new service level agreement (SLA) requiring that all servers entering or exiting a maintenance window must be taken in and out of service properly. The SLA contains the following requirements:
– All mounted databases on the server undergoing maintenance must be activated on another server.
– All message queues on the server undergoing maintenance must be empty before maintenance can begin.
– The server undergoing maintenance must be prevented from becoming a Primary Active Manager (PAM).
– Databases copies on the server undergoing maintenance must not be activated while maintenance is occurring.
QUESTION 31
Hotspot Question
You are attempting to resolve the database activation issue. You need to identify why the database copies are activated on EX3 instead of EX2. Which command should you use? (To answer, select the appropriate options in the answer area.)
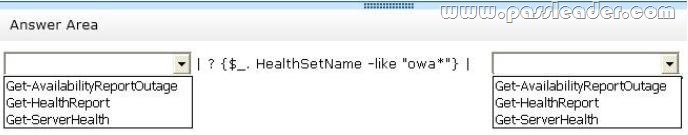
QUESTION 32
Drag and Drop Question
You need to identify which commands must be run to perform the maintenance window tasks. Which commands should you run? (To answer, drag the appropriate commands to the correct tasks. Each command may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)

QUESTION 33
You need to recommend which command must be run to remove the email notifications from all of the servers if App1 malfunctions again. Which command should you recommend? (To answer, configure the appropriate options in the answer area.)

QUESTION 34
You are implementing a solution to meet the security requirements for Outlook authentication. You purchase a new certificate that has a subject name of mail.proseware.com and SANs of autodiscover.proseware.com and oa.proseware.com. You create a host (A) record for oa.proseware.com in the public DNS zone. Remote users report that they fail to connect to their mailbox by using Outlook. You need to ensure that the remote users can connect to their mailbox from Outlook. The solution must meet the security requirements. Which two commands should you run? (Each correct answer presents part of the solution. Choose two.)
A. Set-OutlookProvider EXPR -CertPrincipalName msstd:mail.proseware.com
B. Set-OutlookAnywhere -ExternalHostName oa.proseware.com –
ExternalClientAuthenticationMethod Basic -ExternalClientsRequireSsI $true –
InternalHostName mail.proseware.com –InternalClientAuthenticationMethod NTLM –
InternalClientsRequireSsI Strue
C. Set-OutlookProvider EXPR -CertPrincipalName msstd:oa.proseware.com
D. Set-OutlookAnywhere -ExternalHostName mail.proseware.com –
ExternalClientAuthenticationMethod Basic -ExternalClientsRequireSsI $true –
InternalHostName oa.proseware.com -InternalClientAuthenticationMethod NTLM –
InternalClientsRequireSsI $true
Answer: AB
Explanation:
Set-OutlookProvider EXPR.
The common benefit of enabling Outlook Provider, is to assure Outlook client connecting to a specific server, which has a specific name in subject name field on the certificate. Set-OutlookProvider EXPR -CertPrincipalName msstd:mail.contoso.com. Running above command will force Outlook client “Only connect to proxy servers that have this principal name in their certificate” to be enabled and value set to msstd:mail.contoso.com. If client connects to a proxy server, which does not have mail.contoso.com in subject name field in the certificate, the connection will fail.
Set-OutlookAnywhere.
Use the Set-OutlookAnywhere cmdlet to modify the properties on a computer running Microsoft Exchange Server 2013 enabled for Microsoft Outlook Anywhere. The ExternalHostname parameter specifies the external host name to use in the Microsoft Outlook profiles for users enabled for Outlook Anywhere. The InternalHostname parameter specifies the internal hostname for the Outlook Anywhere virtual directory.
A
Subject name of the certificate is mail.proseware.com not oa.prosware.com.
NOT C
Subject name of the certificate is mail.proseware.com not oa.prosware.com.
B
ExternalHostName oa.proseware.com is correct as oa.proseware.com is a host (A) record in the public DNS zone.
NOT D
ExternalHostName mail.proseware.com is NOT correct as oa.proseware.com is a host (A) record in the public DNS zone.
http://technet.microsoft.com/en-us/library/bb123683(v=exchg.150).aspx
http://technet.microsoft.com/en-us/library/bb123545(v=exchg.150).aspx
QUESTION 35
You need to recommend which actions must be performed to meet the technical requirements for the new Contoso users. Which three actions should you recommend? (Each correct answer presents part of the solution. Choose three.)
A. Configure UPN suffix routing.
B. Configure Contoso to trust Proseware.
C. Configure Proseware to trust Contoso.
D. Run the New-Mailbox cmdlet and specify the -AccountDisabled parameter.
E. Run the New-Mailbox cmdlet and specify the -LinkedMasterAccount parameter.
F. Create a linked role group.
Answer: ACE
Explanation:
http://technet.microsoft.com/en-us/library/cc731404.aspx
UNDERSTANDING TRUST DIRECTION
PROSEWARE CONTOSO
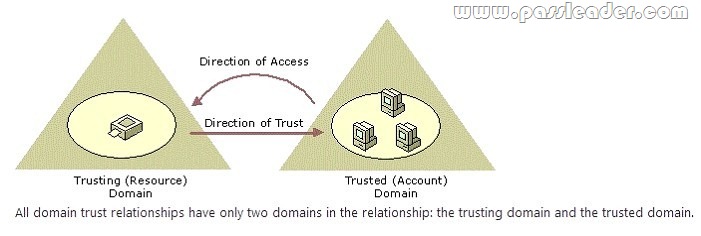
USER ACCOUNT IN CONTOSO NEEDS TO OBTAIN ACCESS TO MAILBOX IN PROSEWAR
E.INC DIRECTION OF TRUST IS FROM PROSEWARE TO CONTOSO. THAT IS PROSEWARE NEEDS TO TRUST CONTOSO.
A
All new user accounts in contoso.com must have a user principal name (UPN) that ends with proseware.com.
Configure UPN suffix routing.
Name suffix routing is a mechanism that you can use to manage how authentication requests are routed across Active Directory forests that are joined by forest trusts.
NOT B
AS PER ABOVE DIAGRAM PROSEWARE NEEDS TO TRUST CONTOSO.
C
AS PER ABOVE DIAGRAM PROSEWARE NEEDS TO TRUST CONTOSO.
E
All new users hired at Contoso must have a user account in contoso.com and an Exchange Server mailbox in proseware.com. Use the New-Mailbox cmdlet to create a user in Active Directory and mailbox-enable this new user. The LinkedMasterAccount parameter specifies the master account in the forest where the user account resides. The master account is the account to link the mailbox to. The master account grants access to the mailbox. This parameter is required only if you’re creating a linked mailbox. A linked mailbox is a mailbox that’s associated with an external account. The resource forest scenario is an example of a situation in which you would want to associate a mailbox with an external account. In a resource forest scenario, user objects in the Exchange forest have mailboxes, but the user objects are disabled for logon. You must associate these mailbox objects in the Exchange forest with enabled user objects in the external accounts forest.
NOT D
Need to use linked mailboxes. Use the New-Mailbox cmdlet to create a user in Active Directory and mailbox-enable this new user. The AccountDisabled parameter specifies whether to create the mailbox in a disabled state. You don’t have to specify a value with this parameter.
NOT F
Need to use linked mailboxes. You can use a linked management role group to enable members of a universal security group (USG) in a foreign Active Directory forest to manage a Microsoft Exchange Server 2013 organization in a resource Active Directory forest. By associating a USG in a foreign forest with a linked role group, the members of that USG are granted the permissions provided by the management roles assigned to the linked role group. For more information about linked role groups, see Understanding Management Role Groups.
http://technet.microsoft.com/en-us/library/aa997663(v=exchg.150).aspx
QUESTION 36
Hotspot Question
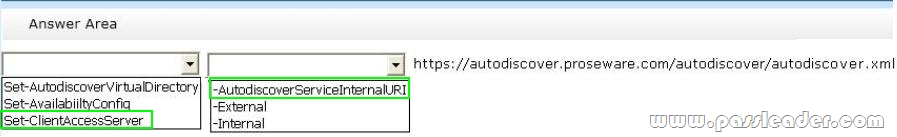
You need to recommend a solution to resolve the Autodiscover and the free/busy information issues. Which command should you include in the recommendation? (To answer, configure the appropriate options in the answer area.)

QUESTION 37
You need to recommend a solution to resolve the issue of the human resources department manager. What should you include in the recommendation?
A. Run Set-ADServerSettings -ConfigurationDomainController dcl.proseware.com on all of the Exchange servers in the London site.
B. Move the PDC emulator to the New York office.
C. Modify the replication interval on the Active Directory site link.
D. Schedule a task that runs the Update-AddressList command to run once per hour.
Answer: C
Explanation:
NOT A
Set-ADServerSettings.
Use the Set-AdServerSettings cmdlet to manage the Active Directory Domain Services (AD DS) environment in the current Exchange Management Shell session. The Set-AdServerSettings cmdlet replaces the AdminSessionADSettings session variable that was used in Microsoft Exchange Server 2007. The ConfigurationDomainController parameter specifies the fully qualified domain name (FQDN) of the configuration domain controller to be used for reading Exchange configuration information in this session.
NOT B
Issue is related to AD Site replication.
NOT D
Will not improve the site replication. You can use the Shell to update a global address list (GAL). A GAL is a directory that contains entries for every group, user, and contact within an organization’s implementation of Microsoft Exchange.
C
You must set the site link replication interval property to indicate how frequently you want replication to occur during the times when the schedule allows replication. For example, if the schedule allows replication between 02:00 hours and 04:00 hours, and the replication interval is set for 30 minutes, replication can occur up to four times during the scheduled time. The default replication interval is 180 minutes, or 3 hours. Consider the following criteria to determine how often replication occurs within the schedule window: A small interval decreases latency but increases the amount of WAN traffic. To keep domain directory partitions up to date, low latency is preferred.
http://technet.microsoft.com/en-us/library/cc738212(v=WS.10).aspx
QUESTION 38
You have an Exchange Server 2013 organization that contains two Client Access servers named SERVER1 and SERVER2 and two Mailbox servers named SERVER3 and SERVER4. You have a firewall that controls all of the traffic between the internal network and the Internet. SERVER3 and SERVER4 are prevented from communicating with Internet hosts. SERVER1 and SERVER3 are in a site named Main. SERVER2 and SERVER4 are in a site named Main_2. All outbound email is sent through SERVER1. Main fails. You discover that email messages for the Internet are queued on SERVER4. You create a new send connector in Main_2. You discover that all of the outbound email is queued on SERVER4 and is not delivered to the Internet. You verify that the client computers on the network can receive email messages from the Internet successfully. You need to ensure that the email messages are delivered successfully to the Internet. Which cmdlet should you run?
A. Set-SendConnector
B. Set-TransportService
C. Set-ExchangeServer
D. Set-ADSite
Answer: A
Explanation:
Mailbox Server.
In an Exchange Server 2013 organization the Mailbox server role is responsible for sending outbound email via a Send Connector.

When this option is enabled outbound email that is being sent via a Send Connector does not go directly out from the Mailbox server, and instead is proxied through a Client Access server in the site. There is nothing complicated going on here, the Client Access server simply acts as a proxy for the connection so that the receiving host out on the internet sees the connection as coming from the Client Access server name and IP address rather than the Mailbox server.
IN THIS QUESTION THE CLIENT ACCESS SERVER (SERVER1) IS ACTING AS A PROXY SERVER FOR THE MAILBOX SERVERS.
NEED TO CHANGE THE SEND CONNECTOR SETTINGS IN ORDER FOR MAIL TO FLOW OUT FROM SERVER4 TO THE INTERNET.
Set-SendConnector.
Use the Set-SendConnector cmdlet to modify a Send connector.
EXAMPLE 1
This example makes the following configuration changes to the Send connector named Contoso.com Send Connector:
Sets the maximum message size limit to 10 MB. Changes the connection inactivity time-out to 15 minutes.
Set-SendConnector “Contoso.com Send Connector” -MaxMessageSize 10MB –
ConnectionInactivityTimeOut
00:15:00
Send Connector.
In Microsoft Exchange Server 2013, a Send connector controls the flow of outbound messages to the receiving server. They are configured on Mailbox servers running the Transport service. Most commonly, you configure a Send connector to send outbound email messages to a smart host or directly to their recipient, using DNS. Exchange 2013 Mailbox servers running the Transport service require Send connectors to deliver messages to the next hop on the way to their destination. Send connectors that are created on Mailbox servers are stored in Active Directory and are available to all Mailbox servers running the Transport service in the organization.



NOT B
Set-transportservice.
Use the Set-TransportService cmdlet to set the transport configuration options for the Transport service on Mailbox servers or for Edge Transport servers. This example sets the TransientFailureRetryCount parameter to 3 and sets the TransientFailureRetryInterval parameter to 30 seconds for the Transport service on a Mailbox server named Mailbox01.
Set-TransportService Mailbox01 -TransientFailureRetryCount 3 -TransientFailureRetryInterval
00:00:30
NOT C
Will not resolve the issue.
Set-ExchangeServer.
Use the Set-ExchangeServer cmdlet to set Exchange attributes in Active Directory for a specified server. For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
This example disables error reporting on the specified server.
Set-ExchangeServer -Identity TestServer.Contoso.com -ErrorReportingEnabled: $false
NOT D
Will not resolve the issue.
Set-ADSite
Use the Set-AdSite cmdlet to configure the Exchange settings of Active Directory sites.
EXAMPLE 1
This example configures the Active Directory site named Default-First-Site-Name as a hub site. Set-AdSite Default-First-Site-Name -HubSiteEnabled $true
http://technet.microsoft.com/en-us/library/aa998294(v=exchg.150).aspx
QUESTION 39
You have an Exchange Server 2013 organization named adatum.com. The organization contains five Mailbox servers and two Client Access servers. You need to ensure that an administrator named user1 receives a daily email message that contains a log of all the Exchange Server administrative actions. Which cmdlet should you use in a scheduled task?
A. Search-AdminAuditLog
B. Set-Mailbox
C. New-AdminAuditLogSearch
D. Set-ExchangeServer
E. Set-AdminAuditLogConfig
Answer: C
Explanation:
NOT A
Use Search-AdminAuditLog for searching through the audit logs.
Search-AdminAuditLog.
Use the Search-AdminAuditLog cmdlet to search the contents of the administrator audit log. For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
This example finds all the administrator audit log entries that contain either the New-RoleGroup or the New-ManagementRoleAssignment cmdlet. Search-AdminAuditLog -Cmdlets New-RoleGroup, New-ManagementRoleAssignment.
NOT B
Set-Mailbox.
Use the Set-Mailbox cmdlet to modify the settings of an existing mailbox. You can use this cmdlet for one mailbox at a time. To perform bulk management, you can pipeline the output of various Get-cmdlets (for example, the Get-Mailbox or Get-User cmdlets) and configure several mailboxes in a single-line command. You can also use the Set-Mailbox cmdlet in scripts. For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
This example delivers John Woods’s email messages to John’s mailbox and also forwards them to Manuel Oliveira’s ([email protected]) mailbox.
Set-Mailbox -Identity John -DeliverToMailboxAndForward $true -ForwardingSMTPAddress [email protected]
NOT D
Set-ExchangeServer.
Use the Set-ExchangeServer cmdlet to set Exchange attributes in Active Directory for a specified server. For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
This example disables error reporting on the specified server.
Set-ExchangeServer -Identity TestServer.Contoso.com -ErrorReportingEnabled: $false
NOT E
NOT Set-AdminAuditLogConfig.
Use the Set-AdminAuditLogConfig cmdlet to configure the administrator audit logging configuration settings.
EXAMPLE 1
This example enables administrator audit logging for every cmdlet and every parameter in the organization, with the exception of Get cmdlets.
Set-AdminAuditLogConfig -AdminAuditLogEnabled $true -AdminAuditLogCmdlets * -AdminAuditLogParameters *
C
New-AdminAuditLogSearch.
Use the New-AdminAuditLogSearch cmdlet to search the contents of the administrator audit log and send the results to one or more mailboxes that you specify. For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
This example finds all the administrator audit log entries that match the following criteria and sends the results to the [email protected] and [email protected] SMTP addresses:
Cmdlets Set-Mailbox Parameters UseDatabaseQuotaDefaults, ProhibitSendReceiveQuota, ProhibitSendQuota StartDate 01/24/2012 EndDate 02/12/2012
New-AdminAuditLogSearch -Name “Mailbox Quota Change Audit” -Cmdlets Set-Mailbox -Parameters
UseDatabaseQuotaDefaults, ProhibitSendReceiveQuota, ProhibitSendQuota -StartDate 01/24/2012 -EndDate
02/12/2012 -StatusMailRecipients [email protected], [email protected] New-AdminAuditLogSearch: Exchange 2013 Help
QUESTION 40
You have an Exchange Server 2013 organization. You plan to deploy Exchange ActiveSync for mobile devices. Each mobile device will be authenticated by using certificates issued by an internal certification authority (CA). You need to configure the organization to authenticate the mobile devices by using the certificates. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. From Internet Information Services (IIS) Manager on each Client Access server, configure the Microsoft-Server-ActiveSync virtual directory to require client certificates.
B. From Exchange Admin Center, configure the Microsoft-Server-ActiveSync virtual directory to require client certificates.
C. From Internet Information Services (IIS) Manager on each Client Access server, enable Active Directory Client Certificate Authentication.
D. From Internet Information Services (IIS) Manager on each Mailbox server, enable Active Directory Client Certificate Authentication.
Answer: BC
Explanation:
NOT A
Enable Active Directory Client Certificate Authentication within IIS but configure the Microsoft-Server-ActiveSync virtual directory to require client certificates is performed in Exchange Admin Center.
NOT D
IIS is configured on the Client Access Server not the Mailbox Server.
B
After you’ve installed the Exchange 2013 Client Access server, there are a variety of configuration tasks that you can perform. Although the Client Access server in Exchange 2013 doesn’t handle processing for the client protocols, several settings need to be applied to the Client Access server, including virtual directory settings and certificate settings.
http://technet.microsoft.com/en-us/library/gg247612(v=exchg.150).aspx
Exchange Server 2013 automatically configures multiple Internet Information Services (IIS) virtual directories during installation. This topic contains information about the default IIS authentication settings and default Secure Sockets Layer (SSL) settings for the Client Access and Mailbox servers.
C
Configure certificate-based authentication for Exchange ActiveSync.
http://blogs.technet.com/b/exchange/archive/2012/11/28/configure-certificate-based-authentication-forexchange-activesync.aspx
Client Access Server Configuration.
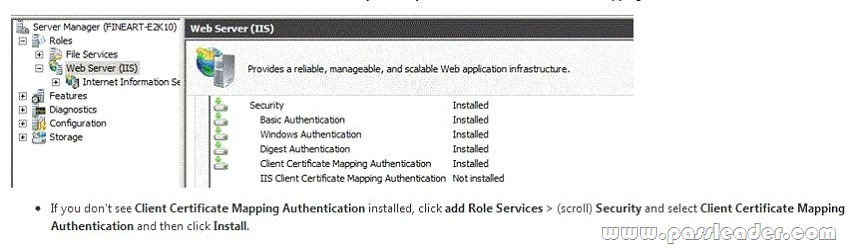
To configure the Client Access server to enforce certificate based authentication:
1. Verify if Certificate Mapping Authentication is installed on the server. Right click on Computer in the start menu and choose Manage. Expand Roles and click on Web Server (IIS). Scroll down to the Role Services section. Under the Security section you should see Client Certificate Mapping Authentication installed.


Get the newest PassLeader 70-341 VCE dumps here: http://www.passleader.com/70-341.html (261 Q&As Dumps –> 272 Q&As Dumps)
And, DOWNLOAD the newest PassLeader 70-341 PDF dumps from Cloud Storage for free: https://drive.google.com/open?id=0B-ob6L_QjGLpfjZ2U1ZfVEZvU0ZreTJkNG1xdmxjS0xUYkdHWVMxWFNRVDhOYTlyRzBjOXM