Valid 70-341 Dumps shared by PassLeader for Helping Passing 70-341 Exam! PassLeader now offer the newest 70-341 VCE dumps and 70-341 PDF dumps, the PassLeader 70-341 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader 70-341 dumps with VCE and PDF here: http://www.passleader.com/70-341.html (261 Q&As Dumps –> 272 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader 70-341 dumps from Cloud Storage: https://drive.google.com/open?id=0B-ob6L_QjGLpfjZ2U1ZfVEZvU0ZreTJkNG1xdmxjS0xUYkdHWVMxWFNRVDhOYTlyRzBjOXM
QUESTION 41
You have an Exchange Server 2013 organization that contains two servers named EX1 and EX2. EX1 and EX2 are the members of a database availability group (DAG) named DAG1. EX1 and EX2 each contain a copy of a mailbox database named DB1. DB1 is configured to retain deleted items for 120 days. At the end of each month, the mailbox databases on EX1 are backed up to tape. The monthly backups are retained for two years. A user named User1 has a mailbox in DB1. User1 discovers that a mailbox folder that contained important email messages was deleted more than six months ago. You need to recover the deleted mailbox folder without affecting any other users who have mailboxes in DB1. Which three actions should you perform? (Each correct answer presents part of the solution. Choose three.)
A. Run the New-MaiboxRestoreRequestcmdlet.
B. Run the New-MailboxDatabasecmdlet and specify the Recovery parameter.
C. Restore DB1 from the tape backup to an alternate location.
D. Restore DB1 from the tape backup to the database’s original location.
E. Run the New-Mailbox cmdlet and specify the Recovery parameter.
Answer: ABC
Explanation:
Recovery Database.
A recovery database is a special kind of mailbox database that allows you to mount a restored mailbox database and extract data from the restored database as part of a recovery operation. You can use the New-MailboxRestoreRequest cmdlet to extract data from a recovery database. After extraction, the data can be exported to a folder or merged into an existing mailbox. Recovery databases enable you to recover data from a backup or copy of a database without disturbing user access to current data.
A
New-MaiboxRestoreRequestcmdlet.
Use the New-MailboxRestoreRequest cmdlet to restore a soft-deleted or disconnected mailbox. This cmdlet starts the process of moving content from the soft-deleted mailbox, disabled mailbox, or any mailbox in a recovery database into a connected primary or archive mailbox. For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
To create a restore request, you must provide the DisplayName, LegacyDN, or MailboxGUID for the softdeleted or disabled mailbox. This example uses the Get-MailboxStatistics cmdlet to return the DisplayName, LegacyDN, MailboxGUID, and DisconnectReason for all mailboxes on mailbox database MBD01 that have a disconnect reason of SoftDeleted or Disabled.
Get-MailboxStatistics -Database MBD01 | Where { $_.DisconnectReason -eq “SoftDeleted” -or $_.
DisconnectReason -eq “Disabled” } | Format-List LegacyDN, DisplayName, MailboxGUID, DisconnectReason
This example restores the source mailbox with the MailboxGUID 1d20855f-fd54-4681-98e6-e249f7326ddd on mailbox database MBD01 to the target mailbox with the alias Ayla. New-MailboxRestoreRequest -SourceDatabase “MBD01” -SourceStoreMailbox 1d20855f-fd54-4681-98e6-e249f7326ddd -TargetMailbox Ayla
B
Use the New-MailboxDatabase cmdlet to create a mailbox database object in the database container in Active Directory. For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
This example creates the mailbox database MailboxDatabase01. This example also specifies where to create the .edb database file, which is different than the default location.
New-MailboxDatabase -Name “MailboxDatabase01” -EdbFilePath
D:\DatabaseFiles\MailboxDatabase01.edb
The Recovery parameter specifies that the new database is designated as a recovery database.
NOT D
Need to recover data from a backup or copy of a database without disturbing user access to current data. Therefore restore to an alternate location.
NOT E
No recovery parameter exists for the New-Mailbox cmdlet.
Reference: Create a Recovery Database
Reference: Restore Data Using a Recovery Database
QUESTION 42
You have an Exchange Server 2010 organization. All users connect to their mailbox by using Microsoft Outlook 2013 and Outlook Web App. All client connections to Exchange Server use the name mail.contoso.com. You deploy Exchange Server 2013 to the organization, you move all of the users to Exchange Server 2013, and then you decommission all of the Exchange Server 2010 servers. The users report that when they open Outlook 2013, they receive a certificate warning message. The users do not receive a certificate error message or a certificate warning message when they open Outlook Web App. You need to prevent the certificate warning message from occurring when the users open Outlook 2013. Which cmdlet should you run?
A. Set-ClientAccessServer
B. New-ExchangeCertficiate
C. New-ClientAccessArray
D. Import-ExchangeCertificate
Answer: A
Explanation:
UNABLE TO ASSOCIATE SET-CLIENTACCESSSERVER WITH CERTIFICATE ERROR D LOOKS LIKE A BETTER RESPONSE. IMPORT THE SSL CERTIFICATE AND THEN ASSIGN IT TO OUTLOOK 2013.
Self-signed Certificate.
When you install Exchange 2013, a self-signed certificate is automatically configured on the Mailbox servers. A self-signed certificate is signed by the application that created it. The subject and the name of the certificate match. The issuer and the subject are defined on the certificate. This self-signed certificate is used to encrypt communications between the Client Access server and the Mailbox server. The Client Access server trusts the self-signed certificate on the Mailbox server automatically, so no third-party certificate is needed on the Mailbox server. When you install Exchange 2013, a self-signed certificate is also created on the Client Access server. This self-signed certificate will allow some client protocols to use SSL for their communications. Exchange ActiveSync and Outlook Web App can establish an SSL connection by using a self-signed certificate. Outlook Anywhere won’t work with a self-signed certificate on the Client Access server. Self-signed certificates must be manually copied to the trusted root certificate store on the client computer or mobile device. When a client connects to a server over SSL and the server presents a self-signed certificate, the client will be prompted to verify that the certificate was issued by a trusted authority. The client must explicitly trust the issuing authority. If the client confirms the trust, then SSL communications can continue.
Note:
By default, the digital certificate installed on the Mailbox server or servers is a self-signed certificate. You don’t need to replace the self-signed certificate on the Mailbox servers in your organization with a trusted third-party certificate. The Client Access server automatically trusts the self-signed certificate on the Mailbox server and no other configuration is needed for certificates on the Mailbox server.
Outlook 2013.
When connecting to an Exchange server using Outlook 2013 you may encounter an SSL trust error.
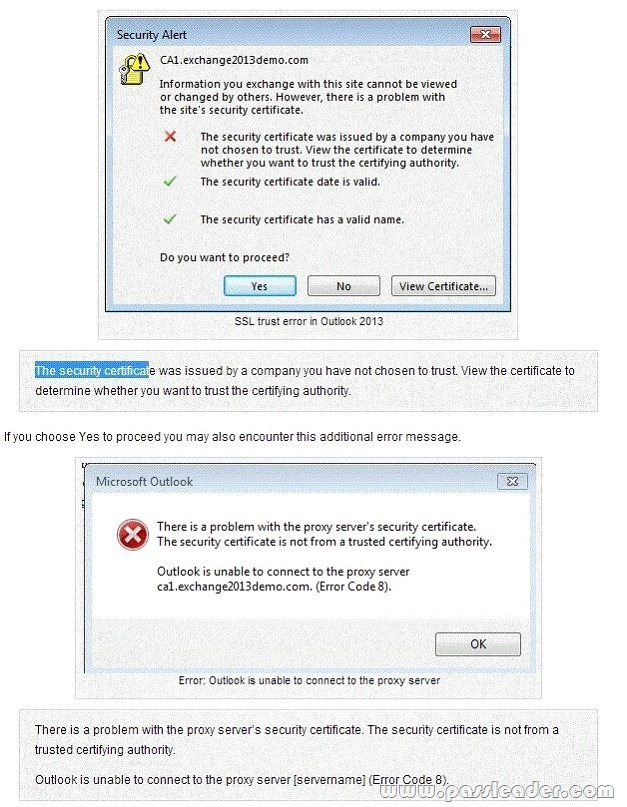
This error occurs when the Exchange server is configured with a self-signed SSL certificate. Outlook makes connections to the Exchange server over HTTPS and therefore must trust the SSL certificate that is configured on the server, otherwise it will display those error messages to the end user. To resolve the issue install a valid SSL certificate on the Exchange server from a trusted certificate authority. See Exchange Server 2013 SSL certificates for more details on this as well as step by step instructions.
A
Set-ClientAccessServer.
Use the Set-ClientAccessServer cmdlet to set properties on specified Client Access server objects.
For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
This example sets two properties on the Client Access server CAS-01.
Set-ClientAccessServer -Identity “CAS-01” -AutoDiscoverServiceInternalUri “https://cas01.contoso.com/autodiscover/autodiscover.xml” -AutoDiscoverSiteScope “Mail”
EXAMPLE 2
This example sets two properties on the Client Access server CASMail.
Set-ClientAccessServer -Identity “CASMail” -AutoDiscoverServiceInternalUri “https://casmail.contoso.com/autodiscover/autodiscover.xml” -AutoDiscoverSiteScope “Mail”
NOT B
New-ExchangeCertficiate. Not an Exchange 2013 command or any other Exchange version command.
NOT C
Exchange 2010 command.
Use the New-ClientAccessArray cmdlet to create an object that represents a load balanced array of Client Access servers within a single Active Directory site.
EXAMPLE 1
This example creates the Client Access server array server.contoso.com.
New-ClientAccessArray -Fqdn server.contoso.com -Site “Redmond” -Name
“server.contoso.com”
NOT D
Exchange 2013 command.
Use the Import-ExchangeCertificate cmdlet to import a certificate or chain of certificates. For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
This example imports an existing certificate and private key from the PKCS #12 file ExportedCert.pfx.
Import-ExchangeCertificate -FileData ([Byte[]]$(Get-Content -Path
c:\certificates\ExportedCert.pfx -Encoding
byte -ReadCount 0)) -Password:(Get-Credential).password
QUESTION 43
Your network contains an Active Directory forest. The forest contains two sites named Montreal and New York. You have an Exchange Server 2013 organization that contains a Mailbox server and a Client Access server in each site. The users in the New York site report that the offline address book (OAB) is not updated after an extended WAN outage between the sites. The Montreal site contains the OAB generation server. You need to ensure that the New York site users download the OAB from a server in the New York site. Which two cmdlets should you run? (Each correct answer presents part of the solution. Choose two.)
A. Set-Mailbox
B. New-OfflineAddressBook
C. New-Mailbox
D. New-OabVirtualDirectory
E. Set-OfflineAddressBook
Answer: AC
Explanation:
A
Set-Mailbox.
Use the Set-Mailbox cmdlet to modify the settings of an existing mailbox. You can use this cmdlet for one mailbox at a time. To perform bulk management, you can pipeline the output of various Get-cmdlets (for example, the Get-Mailbox or Get-User cmdlets) and configure several mailboxes in a single-line command. You can also use the Set-Mailbox cmdlet in scripts. For information about the parameter sets in the Syntax section below, see Syntax.
Enable OABGen capability.
Set-Mailbox -Arbitration oabs -OABGen $true
http://technet.microsoft.com/en-us/library/aa996345(v=exchg.150).aspx
Provision Recipients for Offline Address Book Downloads.
To specify which OAB is downloaded by linking the OAB directly to a recipient’s mailbox, use the following syntax.
Set-Mailbox -Identity <MailboxIDParameter> -OfflineAddressBook <OfflineAddressBookIdParameter>
Better for this question (but the option is not covered). Use the Shell to specify the OAB that multiple recipients will download. This example specifies that all user mailboxes in the United States for Contoso will download the OAB Contoso United States.
Get-User -ResultSize Unlimited -Filter { Company -eq “Contoso” -and RecipientType -eq “UserMailbox” } | Where { $_.CountryOrRegion -eq “United States”} | Set-Mailbox -OfflineAddressBook “Contoso United States”
NOT B
New-OfflineAddressBook.
Use the New-OfflineAddressBook cmdlet to create an offline address book (OAB).
EXAMPLE 1
This example uses two commands to create the OAB named OAB_AgencyB that includes all address lists where AgencyB is part of the name. With the settings shown, an OAB is generated by myserver.contoso.com on Mondays and Wednesdays from 01:00 (1:00 A.M.) to 02:00 (2:00 A.M.). The command also creates the default OAB for the organization.
$a = Get-AddressList | Where {$_.Name -Like “*AgencyB*”
New-OfflineAddressBook -Name “OAB_AgencyB” -Server myserver.contoso.com -AddressLists $a -Schedule “Mon.01:00-Mon.02:00, Wed.01:00-Wed.02:00”
C
New-Mailbox
Use the New-Mailbox cmdlet to create a user in Active Directory and mailbox-enable this new user.
Create a new arbitration mailbox.
New-Mailbox -Arbitration -Name “OAB New York” -Database DB2NewYork -UserPrincipalName [email protected] –DisplayName “OAB Mailbox for New York”
EXAMPLE 1
This example creates a user Chris Ashton in Active Directory and creates a mailbox for the user. The mailbox is located on Mailbox Database 1. The password must be reset at the next logon. To set the initial value of the password, this example creates a variable ($password), prompts you to enter a password, and assigns that password to the variable as a SecureString object.
$password = Read-Host “Enter password” -AsSecureString
New-Mailbox -UserPrincipalName [email protected] -Alias chris -Database “Mailbox Database 1” -Name ChrisAshton -OrganizationalUnit Users -Password $password -FirstName Chris -LastName Ashton -DisplayName “Chris Ashton” -ResetPasswordOnNextLogon $true
NOT D
New-OabVirtualDirectory.
Use the New-OABVirtualDirectory cmdlet to configure a server as a web distribution point for an offline address book (OAB).
EXAMPLE 1
This example creates an OAB virtual directory on CASServer01 and configures the distribution service to poll the generation server every two hours.
New-OABVirtualDirectory -Server CASServer01 -PollInterval 120
NOT E
Set-OfflineAddressBook.
Use the Set-OfflineAddressBook cmdlet to modify offline address book (OAB) settings.
EXAMPLE 1
This example changes the name of the OAB.
Set-OfflineAddressBook -Identity “\Default Offline Address Book” -Name “My Offline Address Book”
QUESTION 44
Your network contains an Active Directory forest. The forest contains one domain. The domain contains two sites and three domain controllers. The sites and domain controllers are configured as shown in the following table. The sites connect to each other by using a WAN link. You have an Exchange Server 2013 organization that contains two servers in the Main Office site. In Branch1, you plan to deploy one server to the Exchange Server 2013 organization. You need to ensure that all of the Exchange Server services in Branch1 are available if the WAN link fails after the planned deployment. What should you do?

A. Create a site link bridge, and then configure Branch1 as a hub site.
B. Replace the domain controller in Branch1 with an RODC that runs Windows Server 2012.
C. Replace the domain controller in Branch1 with a writable domain controller that runs a Server Core installation of Windows Server 2008.
D. Create an additional site link, and then configure Branch1 as a hub site.
Answer: C
Explanation:
Site link bridge. A site link bridge connects two or more site links and enables transitivity between site links. Each site link in a bridge must have a site in common with another site link in the bridge. The Knowledge Consistency Checker (KCC) uses the information on each site link to compute the cost of replication between sites in one site link and sites in the other site links of the bridge. Without the presence of a common site between site links, the KCC also cannot establish direct connections between domain controllers in the sites that are connected by the same site link bridge. By default, all site links are transitive.
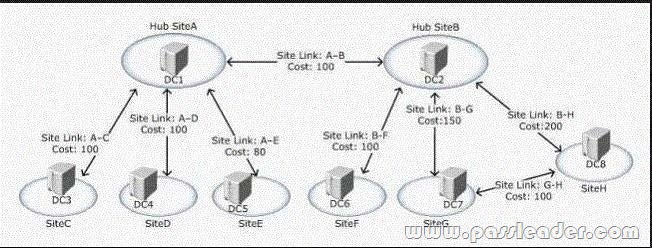
This figure illustrates an organization’s hub-and-spoke network topology, consisting of two hub sites (A and B) and six satellite sites (C through H). The site links between all sites are named A-B, A-C, A-D, A-E, B-F, B-G, and B-H.
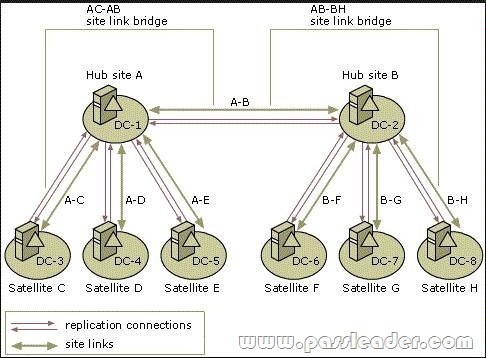
Hub Site
A hub site is based on having large numbers of outgoing links.
NOT ABD
If you want to install or operate any Exchange 2013 server in a site, you must have a writable global catalog in the same AD site. Be aware that no versions of Exchange Server will make use of RODC or the Global Catalog server on a RODC although Exchange will work in the presence of RODC as long as writable versions of domain controllers and GCs are available.
C
If you want to install or operate any Exchange 2013 server in a site, you must have a writable global catalog in the same AD site. The Global Catalog is the central repository of information about objects in a tree or forest but with a limited number of each objects attribute. The domain controller that holds a copy of the Global Catalog is the Global Catalog Server. The global catalog server makes it possible to search the entire AD DS forest without referrals to the domain controller that stores the target of the search. The global catalog server is also required for searching and processing domain logons in forests where universal groups is available Be aware that no versions of Exchange Server will make use of RODC or the Global Catalog server on a RODC although Exchange will work in the presence of RODC as long as writable versions of domain controllers and GCs are available.
QUESTION 45
Your company has a main office site and a disaster recovery site. The two sites connect to each other by using redundant WAN links. Each site connects directly to the Internet. Each site contains one Exchange Server 2013 server that is accessible from the Internet. The company uses the ©ontoso.com email address suffix. The DNS records that can be resolved from the Internet are configured as shown in the following table. When the Internet link at the main office site fails, the company cannot receive incoming email from the Internet. You need to ensure that incoming email from the Internet is delivered to Server1. Incoming email from the Internet must be delivered to Server2 if Server1 is unavailable. What should you create?

A. A CNAME record for the name mail.contoso.com that resolves to server2.contoso.com
B. An MX record that has a cost of 20 and resolves to mail.contoso.com
C. An MX record that has a cost of 20 and resolves to server2.contoso.com
D. An A record for the name mail.contoso.com that resolves to 131.107.101.1
Answer: C
Explanation:
CNAME record. A CNAME record is an abbreviation for Canonical Name record and is a type of resource record in the Domain Name System (DNS) that specifies that the domain name is an alias of another, canonical domain name. Here “canonical” usually means: a more generally accepted or standard name.
MX record. A mail exchanger record (MX record) is a type of resource record in the Domain Name System that specifies a mail server responsible for accepting email messages on behalf of a recipient’s domain, and a preference value used to prioritize mail delivery if multiple mail servers are available. The set of MX records of a domain name specifies how email should be routed with the Simple Mail Transfer Protocol (SMTP). A Record. An A (address) record is a DNS record that can be used to point your domain name and host names to a static IP address.
NOT ABD
Need to increase the cost associated with the MX record of Server2 so that Server1 is preferred over Server2 but Server2 will be used if Server1 is not available.
C
Need to increase the cost associated with the MX record of Server2 so that Server1 is preferred over Server2 but Server2 will be used if Server1 is not available. There is already a CNAME (Alias) associated with mail.contoso.com which points to Server1.contoso.com.
QUESTION 46
Drag and Drop Question
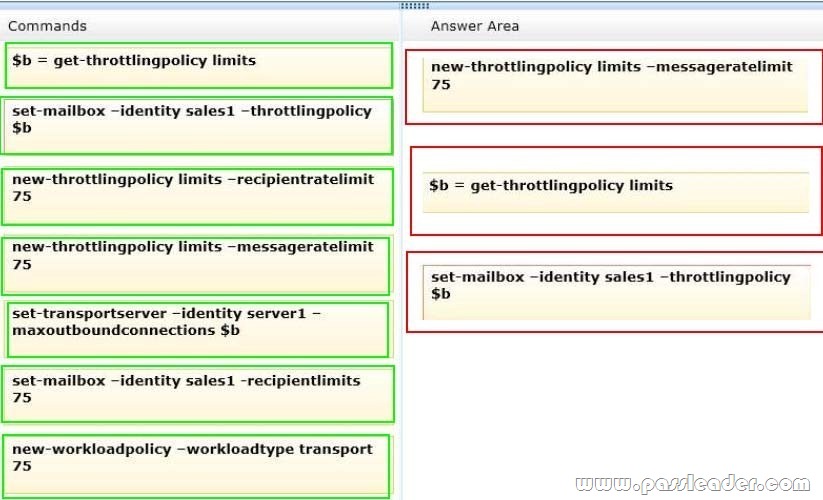
You have an Exchange Server 2013 organization named adatum.com. The organization contains a server named Server1. Server1 is a member of a Database Availability Group (DAG) named DAG1. You have a user named Sales1 in the Sales department. You need to prevent Sales1 from submitting more than 75 email messages per minute to the Exchange Server organization by using Microsoft Outlook. Which three commands should you run in sequence? (To answer, move the appropriate three commands from the list of commands to the answer area and arrange them in the correct order.)

QUESTION 47
Drag and Drop Question
You have an Exchange Server organization that contains three servers. The servers are configured as shown in the following table.
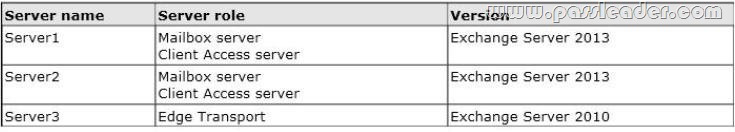
You need to create a new database availability group (DAG) that contains EX1 and EX2.
Which three actions should you perform in sequence? (To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.)
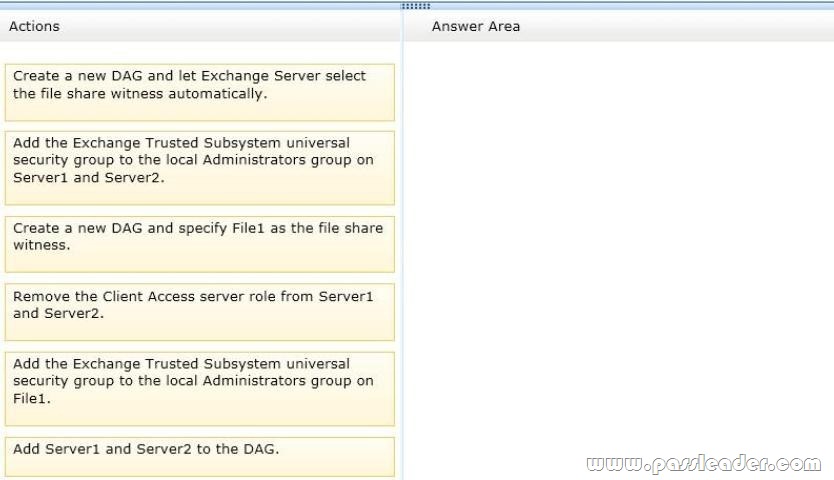
Answer:

Explanation:
Box 1: Add the Exchange Trusted Subsystem universal security group to the local Administrators group on Server1.
Box 2: Create a new DAG and specify Server1 as the file share witness.
Box 3: Add EX1 and EX2 to the DAG.
Note:
– A database availability group (DAG) is a set of up to 16 Microsoft Exchange Server 2013 Mailbox servers that provide automatic database-level recovery from a database, server, or network failure. When a Mailbox server is added to a DAG, it works with the other servers in the DAG to provide automatic, database-level recovery from database, server, and network failures.
– You can specify a name for the DAG and the witness server that you want to use, and leave the Witness directory field empty. In this scenario, the task will create the default witness directory on the specified witness server.
– If the witness server you specify isn’t an Exchange 2013 or Exchange 2010 server, you must add the Exchange Trusted Subsystem universal security group to the local Administrators group on the witness server. These security permissions are necessary to ensure that Exchange can create a directory and share on the witness server as needed.
Reference: Exchange 2013, Create a Database Availability Group
QUESTION 48
You have an Exchange Server 2013 organization that contains two Mailbox servers named MBX1 and MBX2. You create a database availability group (DAG) named DAG1. DAG1 is configured as shown in the exhibit. You need to ensure that replication only occurs over the replication network. Which two commands should you run? (Each correct answer presents part of the solution. Choose two.)

A. Set-DatabaseAvailabilityGroupNetwork ReplicationDagNetwork01 -ReplicationEnabled $true
B. Set-DatabaseAvailabilityGroupNetworkMapiDagNetwork -ReplicationEnabled $false
C. Set-DatabaseAvailabilityGroup Dag1 -ManualDagNetworkConfiguration $true
D. Set-DatabaseAvailabilityGroup Dag1 -ManualDagNetworkConfiguration $false
Answer: BC
Explanation:
You need to ensure that replication only occurs over the replication network. If you would like to ‘force’ replication to only go over the Replication Network, then you definately would like to disable replication on the MAPI Network, but IF the NIC on the Replication Network goes down, it will start replicating over the MAPI NIC. There is no way of blocking that behaviour and isn’t what you’d want anyway since DAGs actually cope quite fine with just 1 NIC.
DAG Networks.
Each database availability group (DAG) network has several properties that you can configure, including the name of the DAG network, a description field for the DAG network, a list of subnets that are used by the DAG network, and whether the DAG network is enabled for replication. You can configure a DAG network only when automatic network configuration has been disabled for a DAG. There are specific networking requirements that must be met for each DAG and for each DAG member. Each DAG must have a single MAPI network, which is used by a DAG member to communicate with other servers (for example, other Exchange 2013 servers or directory servers), and zero or more Replication networks, which are networks dedicated to log shipping and seeding.
Although a single network is supported, we recommend that each DAG have at least two networks: a single MAPI network and a single Replication network. This provides redundancy for the network and the network path, and enables the system to distinguish between a server failure and a network failure. Using a single network adapter prevents the system from distinguishing between these two types of failures.

MAPI.
MAPI stands for Messaging Application Programming Interface, and it gives programs the ability to send email using your email program to do the actual sending.
Set-DatabaseAvailabilityGroup.
The Set-DatabaseAvailabilityGroup cmdlet enables you to manage DAG properties that can’t be managed from the Exchange Administration Center (EAC), such as configuring network discovery, selecting the TCP port used for replication, and enabling datacenter activation coordination (DAC) mode.
Set-DatabaseAvailabilityGroupNetwork.
Use the Set-DatabaseAvailabilityGroupNetwork cmdlet to configure a network for a database availability group (DAG). You can configure a variety of network properties, such as the name for the network, a description of the network, a list of one or more subnets that comprise the network, and whether the network is enabled for replication (log shipping and seeding). You need to be assigned permissions before you can run this cmdlet. Although all parameters for this cmdlet are listed in this topic, you may not have access to some parameters if they’re not included in the permissions assigned to you.
C
Ensures that you can configure a DAG network by turning the automatic configuration off. The ManualDagNetworkConfiguration parameter Specifies whether DAG networks should be automatically configured. If this parameter is set to False, DAG networks are automatically configured. If this parameter is set to True, you must manually configure DAG networks. You can configure a DAG network only when automatic network configuration has been disabled for a DAG. Need to manually configure the DAG NETWORK.
NOT D
Need to turn the automatic DAG configuration off. The ManualDagNetworkConfiguration parameter Specifies whether DAG networks should be automatically configured. If this parameter is set to False, DAG networks are automatically configured. If this parameter is set to True, you must manually configure DAG networks. You can configure a DAG network only when automatic network configuration has been disabled for a DAG.
NOT A
Does not disable the replication over the MAPI network as required in this scenario.
B
Disables replication over the MAPI network as required in this scenario.
QUESTION 49
You have an Exchange Server 2013 organization that contains a server named Server1. Server1 has an IP address of 10.1.100.16 and is configured to use a default gateway of 10.1.100.1. You deploy a hardware load balancer that is configured to use the IP addresses of 192.168.101.31 and 10.1.100.31. A user named User1 has a client computer that has an IP address of 102.168.101.201. User1 reports that he cannot view his mailbox by using Outlook Web App. When you review the IIS logs on Server1, you discover the following information. You need to ensure that User1 can access his mailbox successfully from Outlook Web App. What are two possible ways to achieve this goal? (Each correct answer presents a complete solution. Choose two.)
![]()
A. Configure the hardware load balancer to use the same certificate as the certificate used on Server1.
B. Configure the hardware load balancer to use source NAT (SNAT).
C. Configure the computer of User1 to ignore response headers.
D. Modify the default gateway of Server1.
Answer: BD
Explanation:
Source NAT.
When using source NAT, the client IP address is not passed to the load balanced server. The insertion of the Client IP address into the header allows the servers to see the IP that made the connection. They are then able to return the requested information correctly.
B
Configuring the hardware load balancer to use source NAT (SNAT) will resolve the problem.
D
Changing the default gateway of Server1 to that of the hardware load balancer will ensure that the connection to Server1 will be returned via the network load balancer and out to User1.
NOT A
Not a certificate problem.
NOT C
NOT a http response header issue.
HTTP response header.
The information, in the form of a text record, that a Web server sends back to a clients browser in response to receiving an HTTP request. The response header contains the date, size and type of file that the server is sending back to the client and also data about the server itself. The header is attached to the files being sent back to the client.
QUESTION 50
You have an Exchange Server 2013 organization that is configured to filter email messages for spam and malware. You need to modify the schedule for applying updates to the anti-spam and the antimalware definitions. Which command should you run?
A. Update-MalwareFilteringServer.ps1
B. Set-MalwareFilteringServer
C. Set-SenderFilterConfig
D. Update-SafeList
Answer: B
Explanation:
NOT A
Microsoft Exchange Server 2013 administrators can manually download anti-malware engine and definition (signature) updates. Update-MalwareFilteringServer.ps1 used in manual updates not schedule updates.
NOT C
Not used for spam and malware updates. Use the Set-SenderFilterConfig cmdlet to modify the Sender Filter agent configuration.
EXAMPLE 1
This example makes the following modifications to the Sender Filter agent configuration:
It enables blocking of blank senders.
It blocks messages from lucernepublishing.com and all subdomains. It adds [email protected] and [email protected] to the blocked senders list without affecting any existing entries.
Set-SenderFilterConfig -BlankSenderBlockingEnabled $true –
BlockedDomainsAndSubdomains
lucernepublishing.com -BlockedSenders
@{Add=”[email protected]”,”[email protected]”}
NOT D
Use the Update-SafeList cmdlet to update the safelist aggregation data in Active Directory. Safelist aggregation data is used in the built-in anti-spam filtering in Microsoft Exchange. EdgeSync replicates safelist aggregation data to Edge Transport servers in the perimeter network.
EXAMPLE 1
This example updates Safe Senders List data for the single user [email protected].
Update-Safelist [email protected]
B
Set-MalwareFilteringServer.
Use the Set-MalwareFilteringServer cmdlet to configure the Malware agent settings in the Transport service on a Mailbox server.
Example 1
This example sets the following Malware agent settings on the Mailbox server named Mailbox01:
Sets the update frequency interval to 2 hours
Sets the time to wait between resubmit attempts to 10 minutes
Set-MalwareFilteringServer Mailbox01 -UpdateFrequency 120 -DeferWaitTime 10
QUESTION 51
Hotspot Question
Your network contains an Active Directory forest named contoso.com. The forest contains two sites named Site1 and Site2. You have an Exchange Server 2013 organization that contains two servers. The servers are configured as shown in the following table.
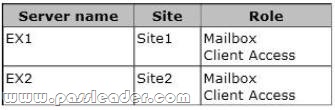
An administrator creates a new Active Directory site named Site3. The administrator creates mailboxes for the users in Site3. All of the mailboxes of the Site3 users are located on EX1. Site3 contains a domain controller named dc3.contoso.com. The Site3 users report that sometimes, when they open Microsoft Outlook, it takes a long time to access their mailbox. You need to reduce the amount of time it takes for the users to access their mailbox. Which command should you run? (To answer, select the appropriate options in the dialog box in the answer area.)
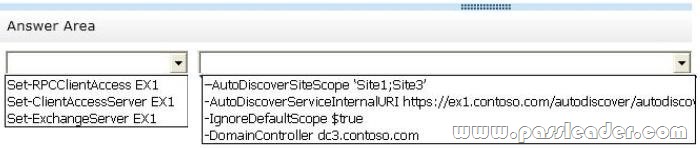
Answer:
Explanation:
Autodiscover Service.
Microsoft Exchange 2013 includes a service named the Autodiscover service. This topic gives an overview of the service and explains how it works, how it configures Outlook clients, and what options there are for deploying the Autodiscover service in your messaging environment. The Autodiscover service does the following:
– Automatically configures user profile settings for clients running Microsoft Office Outlook 2007, Outlook 2010, or Outlook 2013, as well as supported mobile phones. Phones running Windows Mobile 6.1 or a later version are supported. If your phone isn’t a Windows Mobile phone, check your mobile phone documentation to see if it’s supported.
– Provides access to Exchange features for Outlook 2007, Outlook 2010, or Outlook 2013 clients that are connected to your Exchange messaging environment.
– Uses a user’s email address and password to provide profile settings to Outlook 2007, Outlook 2010, or Outlook 2013 clients and supported mobile phones. If the Outlook client is joined to a domain, the user’s domain account is used.
When you install a Client Access server in Exchange 2013, a default virtual directory named Autodiscover is created under the default website in Internet Information Services (IIS). This virtual directory handles Autodiscover service requests from Outlook 2007, Outlook 2010, and Outlook 2013 clients and supported mobile phones under the following circumstances:
– When a user account is configured or updated. When an Outlook client periodically checks for changes to the Exchange Web Services URLs When underlying network connection changes occur in your Exchange messaging environment Additionally, a new Active Directory object named the service connection point (SCP) is created on the server where you install the Client Access server. The SCP object contains the authoritative list of Autodiscover service URLs for the forest. You can use the Set-ClientAccessServer cmdlet to update the SCP object. For more information, see Set-ClientAccessServer.
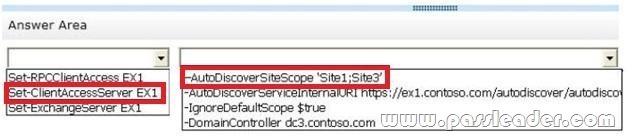
SECTION1
Set-ClientAccessServer EX1.
Use the Set-ClientAccessServer cmdlet to set properties on specified Client Access server objects. Use the Set-ClientAccessServer cmdlet to change AutoDiscover settings.
NOT Set-ExchangeServer.
Use the Set-ExchangeServer cmdlet to set Exchange attributes in Active Directory for a specified server.
NOT Set-RPCClientAccess.
Use the Set-RpcClientAccess cmdlet to manage the settings for the Exchange RPC Client Access service that’s running on a Microsoft Exchange Server 2010 Client Access server.
SECTION2
-AutoDiscoverSiteScope ‘Site1;Site3’.
The AutoDiscoverSiteScope parameter specifies the site for which the Autodiscover service is authoritative. Clients that connect to the Autodiscover service by using the internal URL must belong to a listed site.
NOT -AutoDiscoverServiceInternalURI.
The AutoDiscoverServiceInternalUri parameter specifies the internal URL of the Autodiscover service. Need to specify Site3.
NOT -IgnoreDefaultScope.
NOT a parameter of Set-ClientAccessServer.
The IgnoreDefaultScope parameter instructs the command to ignore the default recipient scope setting for the Exchange Management Shell session and use the entire forest as the scope. This allows the command to access Active Directory objects that aren’t currently in the default scope. Using the IgnoreDefaultScope parameter introduces the following restrictions:
– You can’t use the DomainController parameter. The command uses an appropriate global catalog server automatically.
– You can only use the DN for the Identity parameter. Other forms of identification, such as alias or GUID, aren’t accepted.
– You can’t use the OrganizationalUnit and Identity parameters together.
– You can’t use the Credential parameter.
NOT -DomainController.
The DomainController parameter specifies the fully qualified domain name (FQDN) of the domain controller that writes this configuration change to Active Directory will not resolve the issue.
QUESTION 52
You deploy an Active Directory forest that contains two domains named contoso.com and child.contoso.com. You plan to deploy Exchange Server 2013 servers to the child.contoso.com domain. You need to prepare Active Directory for the installation of the first Exchange Server 2013 servers. Which command should you run in each domain? (To answer, drag the appropriate commands to the correct domains. Each command may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
Answer:

Explanation:
THE SUPPLIED ANSWER IS CORRECT.
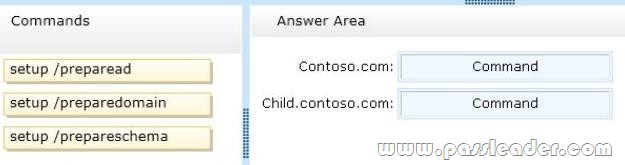
FOR 3 STEPS USE
1. SETUP/PREPARESCHEMA
2. SETUP/PREAREAD
3. SETUP /PREPAREDOMAIN
HOWEVER THE ANSWER ONLY PROVIDES FOR 2 STEPS. IF YOU RUN SETUP /PREPAREAD THEN THIS COMMAND CHECKS TO SEE IF THE SCHEMA EXTENSIONS HAVE BEEN INSTALLED. AND IF NOT THEN IT PROCEEDS TO INSTALL THEM. HENCE SETUP /PREPAREAD IS CORRECT.
A TRICK QUESTION FROM MICROSOFT TO CHECK IF YOU KNOW HOW SETUP/PREPAREAD ACTUALLY OPERATES.
QUESTION 53
You have an Exchange Server 2013 organization. Your company has a Service Level Agreement (SLA) stating that you must be able to reconnect disconnected mailboxes to user accounts for up to 365 days. After 365 days, disconnected mailboxes must be deleted permanently. You need to recommend a solution to meet the SLA. What should you include in the recommendation?
A. Create a retention policy and apply the policy to all mailboxes.
B. Configure the deleted mailbox retention setting for all databases.
C. Configure the deleted item retention setting for all databases.
D. Implement a database availability group (DAG) that contains a lagged copy.
Answer: B
Explanation:
Recoverable Items Folder Exchange 2013.
The Recoverable Items folder replaces the feature known as the dumpster in Exchange Server 2007. The Recoverable Items folder is used by the following Exchange features:
– Deleted item retention
– Single item recovery
– In-Place Hold
– Litigation hold
– Mailbox audit logging
– Calendar logging
– Disconnected Mailboxes
Each Microsoft Exchange mailbox consists of an Active Directory user account and the mailbox data stored in the Exchange mailbox database. All configuration data for a mailbox is stored in the Exchange attributes of the Active Directory user object. The mailbox database contains the mail data that’s in the mailbox associated with the user account. The following figure shows the components of a mailbox.
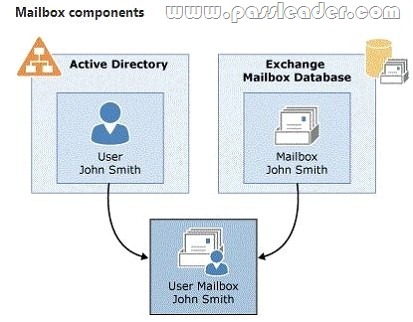
A disconnected mailbox is a mailbox object in the mailbox database that isn’t associated with an Active Directory user account. There are two types of disconnected mailboxes:
1. Disabled mailboxes.
When a mailbox is disabled or deleted in the Exchange Administration Center (EAC) or using the Disable-Mailbox or Remove-Mailbox cmdlet in the Exchange Management Shell, Exchange retains the deleted mailbox in the mailbox database, and switches the mailbox to a disabled state. This is why mailboxes that are either disabled or deleted are referred to as disabled mailboxes. The difference is that when you disable a mailbox, the Exchange attributes are removed from the corresponding Active Directory user account, but the user account is retained. When you delete a mailbox, both the Exchange attributes and the Active Directory user account are deleted. Disabled and deleted mailboxes are retained in the mailbox database until the deleted mailbox retention period expires, which is 30 days by default. After the retention period expires, the mailbox is permanently deleted (also called purged). If a mailbox is deleted using the Remove-Mailbox cmdlet, it’s also retained for the duration of the retention period.
Important:
If a mailbox is deleted using the Remove-Mailbox cmdlet and either the Permanent or StoreMailboxIdentity parameter, it will be immediately deleted from the mailbox database. To identify the disabled mailboxes in your organization, run the following command in the Shell:
Get-MailboxDatabase | Get-MailboxStatistics | Where { $_.DisconnectReason -eq “Disabled” } | ft
DisplayName,Database,DisconnectDate
2. Soft-deleted mailboxes.
When a mailbox is moved to a different mailbox database, Exchange doesn’t fully delete the mailbox from the source mailbox database when the move is complete. Instead, the mailbox in the source mailbox database is switched to a soft-deleted state. Like disabled mailboxes, soft-deleted mailboxes are retained in the source database either until the deleted mailbox retention period expires or until the Remove-StoreMailbox cmdlet is used to purge the mailbox. Run the following command to identify soft-deleted mailboxes in your organization:
Get-MailboxDatabase | Get-MailboxStatistics | Where { $_.DisconnectReason -eq “SoftDeleted” } | ft
DisplayName,Database,DisconnectDate
NOT A
Need to modify the deleted mailbox retention settings.
NOT C
Not related to an item but to databases.
NOT D
Need to modify the deleted mailbox retention settings. DAG with a lagged copy is not modifying the mailbox retention policy settings.
B
Disabled and deleted mailboxes are retained in the mailbox database until the deleted mailbox retention period expires, which is 30 days by default. This example configures a deleted item retention period of 365 days for the mailbox database MDB2. Set-MailboxDatabase -Identity MDB2 -DeletedItemRetention 365 Content can be retained using a variety of built-in functions such as:
– Journaling: With journaling, the organization can have exact copies of content captured and retained in a separate database (a “journaling database”) to ensure the content has not been tampered with and is available for legal search and review at a future time Retention Policy: Content within an Exchange environment can be set to be retained (or purged) based on policies set on the Exchange databases, so either configured through the Exchange Admin console or through a PowerShell command like Set-MailboxDatabase -Identity MDB4 -eletedItemRetention 365 to hold content from being deleted off the Exchange server.
– Personal Archives: Each user in Exchange can have their primary mailbox and an Archive mailbox where the archive mailbox can have content drag/dropped to the archive box for long term storage, similar to what users have historically used Personal Store (PST) files in the past. Unlike a PST file that is almost completely unmanaged by the organization (yet is still considered legal evidence), the Personal Archive in Exchange is part of the Exchange environment with content that can be searched, set for long term retention, and put on legal hold.

QUESTION 54
A user fails to connect to his mailbox by using Outlook Anywhere. The user successfully connects to the mailbox by using an Exchange ActiveSync-enabled mobile device and Outlook Web App. You need to identify what prevents the users from connecting to the mailbox by using Outlook Anywhere. Which tool should you use?
A. Microsoft Outlook
B. Microsoft Exchange Server Deployment Assistant
C. Microsoft Exchange RPC Extractor
D. Microsoft Exchange Server Profile Analyzer
E. Microsoft Exchange Server User Monitor
F. Microsoft Exchange Load Generator
G. Exchange Remote Connectivity Analyzer
H. Exchange Server MAPI Editor
Answer: G
Explanation:
G
Exchange Remote Connectivity Analyzer (ExRCA).
The Exchange Remote Connectivity Analyzer (ExRCA) is a web-based tool designed to test connectivity with a variety of Exchange protocols. The Microsoft Exchange Remote Connectivity Analyzer (ExRCA) can help you confirm that connectivity for your Exchange servers is configured correctly and diagnose any connectivity issues. The Remote Connectivity Analyzer website offers tests for Microsoft Exchange ActiveSync, Exchange Web Services, Microsoft Outlook, and Internet email.

QUESTION 55
Drag and Drop Question
You have an Exchange Server 2013 organization that contains a database availability group (DAG). There are four copies of every mailbox database. One of the copies is a lagged copy configured to have a replay lag time of 14 days. All mailboxes have single item recovery enabled. All databases are configured to have a deleted item retention period of seven days. A company executive reports that an email message, which was deleted 10 days ago, must be restored. You need to ensure that you can recover the email message from the lagged copy of the mailbox database. The solution must preserve the lagged copy of the mailbox database. Which three actions should you perform? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.

Answer:

Explanation:
Run the Suspend-MailboxDatabaseCopy cmdlet.
Run the vssadmin command.
Run the eseutil.exe command.
vssadmin.
Displays current volume shadow copy backups and all installed shadow copy writers and providers in the command window. There could be VSS errors causing the datasources not to enumerate. If so, verify that all Exchange Node and Exchange VSS components are functional. Ensure all databases are mounted and healthy Run vssadmin list writers Move-ActiveMailboxDatabase. Use the Move-ActiveMailboxDatabase cmdlet to perform a database or server switchover. This example performs a switchover of the database DB2 to the Mailbox server MBX1. When the command completes, MBX1 hosts the active copy of DB2. Because the MountDialOverride parameter is set to None, MBX1 mounts the database using its own defined database auto mount dial settings. Move-ActiveMailboxDatabase DB2 -ActivateOnServer MBX1 -MountDialOverride. None The SkipLagChecks parameter specifies whether to allow a copy to be activated that has replay and copy queues outside of the configured criteria.
eseutil.exe.
The key to matching log files and databases is the signature. You can view log file signatures by using the Exchange Server Database Utilities (Eseutil.exe) tool and viewing the log file header with the command Eseutil/ml [log filename]. You can view database (.edb) and streaming database (.stm) file signatures by viewing the file header with Eseutil /mh [database filename].edb. A typical log file or database file signature looks like this:
Signature: Create time:12/17/2002 18:1:44 Rand:81060559 Computer:
Activating and recovering a lagged mailbox database copy is an easy process if you want the database to replay all log files and make the database copy current. If you want to replay log files up to a specific point in time, it’s a more difficult operation because you manually manipulate log files and run Exchange Server Database Utilities (Eseutil.exe).
Suspend-MailboxDatabaseCopy.
Use the Suspend-MailboxDatabaseCopy cmdlet to block replication and replay activities (log copying and replay) or activation for a database configured with two or more database copies. For a variety of reasons, such as performing planned maintenance, it may be necessary to suspend and resume continuous replication activity for a database copy. In addition, some administrative tasks, such as seeding, require you to first suspend a database copy. We recommend that all replication activity be suspended when the path for the database or its log files is being changed.
You can suspend and resume database copy activity by using the EAC, or by running the Suspend-MailboxDatabaseCopy and Resume-MailboxDatabaseCopy cmdlets in the Shell.
EXAMPLE 1
This example suspends replication and replay activity for the copy of the database DB1 hosted on the Mailbox server MBX3. An optional administrative reason for the suspension is specified.
Suspend-MailboxDatabaseCopy -Identity DB1\MBX3 -SuspendComment “Maintenance on MBX3” NOT Move-ActiveMailboxDatabase.
Not attempting to make a passive or lagged database active. You need to ensure that you can recover the email message from the lagged copy of the mailbox database. The solution must preserve the lagged copy of the mailbox database.
STEPS:
No need to use Move-ActiveMailboxDatabase.
1. First Use the Suspend-MailboxDatabaseCopy cmdlet to block replication and replay activities (log copying and replay).
2. 2nd use vssadmin to check that there could be VSS errors causing the datasources not to enumerate.
3. 3rd Run Exchange Server Database Utilities (Eseutil.exe).
THIS LAST STEP NEEDS CLARIFYING.
QUESTION 56
Your company has four regional offices and 20 branch offices. The regional offices connect to each other by using a 30-Mbps WAN link. Each branch office connects to its nearest regional office by using a 1-Mbps WAN link. The network contains an Active Directory forest. The forest contains a domain controller in each office. Each office maps to an Active Directory site. Each branch office site connects to the nearest regional office site by using an Active Directory site link. You have an Exchange Server 2013 organization that contains one server in each office. You need to implement a messaging solution to meet the following requirements:
– The users in the branch offices must only be able to send email messages that are up to 2 MB to the users in the other offices.
– The users in the regional offices must be prevented from sending email messages that are larger than 5 MB to the users in any of the regional offices.
Which cmdlet should you run?
A. Set-TransportRule
B. Set-ADSite
C. Set-AdSiteLink
D. Set-RoutingGroupConnector
Answer: C
Explanation:
NOT A
Does not relate to message size.
Set-TransportRule.
Use the Set-TransportRule cmdlet to modify an existing transport rule in your organization. For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
This example modifies the Sales Team Disclaimer transport rule. Modifying the value of one predicate doesn’t affect other predicates used in the rule’s conditions or exceptions and doesn’t affect actions on the same rule.
This example sets the FromMemberOf parameter to a value of Sales-Group, which specifies that the rule is applied if the sender of the message is a member of the Sales- Group distribution group.
Set-TransportRule “Sales Team Disclaimer” -FromMemberOf “Sales-Group”
NOT B
Does not relate to message size.
Set-ADSite
Use the Set-AdSite cmdlet to configure the Exchange settings of Active Directory sites.
EXAMPLE 1
This example configures the Active Directory site named Default-First-Site-Name as a hub site.
Set-AdSite Default-First-Site-Name -HubSiteEnabled $true
NOT D
Does not relate to message size.
Set-RoutingGroupConnector.
With routing groups and Routing Group connectors you can consolidate communication between servers by designating bridgehead servers that act as communication points between routing groups. For example, your organization may have a remote site connected through a wide-area-network (WAN) link to your main office. In this example, you can use a Routing Group connector to route Exchange traffic between a server at your main office and a server at your remote site.
C
The only command that deals with message size.
Set-AdSiteLink.
Use the Set-AdSiteLink cmdlet to assign an Exchange-specific cost to an Active Directory IP site link. You can also use this cmdlet to configure the maximum message size that can pass across an Active Directory IP site link.
EXAMPLE 1
This example assigns an Exchange-specific cost of 25 to the IP site link DEFAULT_IP_SITE_LINK and configures a maximum message size limit of 10 MB on the IP site link.
Set-AdSiteLink DEFAULT_IP_SITE_LINK -ExchangeCost 25 -MaxMessageSize 10MB
Case Study 5: Fabrikam, Inc. (QUESTION 57 ~ QUESTION 68)
Overview
Fabrikam, Inc., is a pharmaceutical company located in Europe. The company has 5,000 users. The company is finalizing plans to deploy an Exchange Server 2013 organization. The company has offices in Paris and Amsterdam.
Existing Environment
Active Directory Environment
The network contains an Active Directory domain named fabrikam.com. An Active Directory site exists for each office.
Network Infrastructure
The roles and location of each server are configured as shown in the following table.

Client computers run either Windows 7 or Windows 8 and have Microsoft Office 2010 installed. The Paris office uses the 192.168.1.0/24 IP range. The Amsterdam office uses the 192.168.2.0/24 IP range. The offices connect to each other by using a high-speed, low-latency WAN link. Each office has a 10-Mbps connection to the Internet.
Planned Exchange Infrastructure
The company plans to deploy five servers that run Exchange Server. The servers will be configured as shown in the following table.

The company plans to have mailbox databases replicated in database availability groups (DAGs). The mailbox databases and DAGs will be configured as shown in the following table.
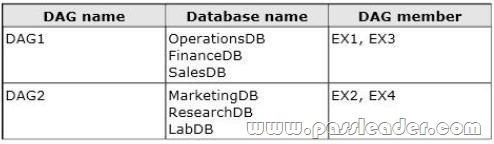
DAG1 will use FS1 as a file share witness. DAG2 will use FS3 as a file share witness. You plan to create the following networks on each DAG:
– A dedicated replication network named DAGNET1
– A MAPI network named DAGNET2
All replication traffic will run on DAGNET1. All client connections will run on DAGNET2. Client connections must never occur on DAGNET1. Replication traffic must only occur on DAGNET2 if DAGNET1 is unavailable. Each Exchange Server 2013 Mailbox server will be configured to have two network adapters. The following two mailbox databases will not be replicated as part of the DAGs:
– A mailbox database named AccountingDB that is hosted on EX1.
– A mailbox database named TempStaffDB that is hosted on EX4 EDGE1 will have an Edge Subscription configured, with both EX1 and EX2 as targets.
Requirements
Planned Changes
An external consultant reviews the Exchange Server 2013 deployment plan and identifies the following areas of concern:
– The DAGs will not be monitored.
– Multiple Edge Transport servers are required to prevent the potential for a single point of failure.
Technical Requirements
Fabrikam must meet the following technical requirements:
– Email must be evaluated for SPAM before the email enters the internal network.
– Production system patching must minimize downtime to achieve the highest possible service to users.
– Users must be able to use the Exchange Control Panel to autonomously join and disjoin their department’s distribution lists.
– Users must be able to access all Internet-facing Exchange Server services by using the names of mail.fabrikam.com and autodiscover.fabrikam.com.
The company establishes a partnership with another company named A. Datum Corporation. A. Datum uses the SMTP suffix adatum.com for all email addresses. Fabrikam plans to exchange sensitive information with A. Datum and requires that the email messages sent between the two companies be encrypted. The solution must use Domain Security. Users in the research and development (R&D) department must be able to view only the mailboxes of the users in their department from Microsoft Outlook. The users in all of the other departments must be prevented from viewing the mailboxes of the R&D users from Outlook. Administrators plan to produce HTML reports that contain information about recent status changes to the mailbox databases. Fabrikam is evaluating whether to abort its plan to implement an Exchange Server 2010 Edge Transport server and to implement a Client Access server in the Paris office instead. The Client Access server will have anti-spam agents installed.
QUESTION 57
Hotspot Question
You need to recommend which configurations must be set for each network. Which configurations should you recommend? To answer, select the appropriate configurations for each network in the answer area.

QUESTION 58
An administrator recommends removing EDGE1 from the implementation plan and adding a new Client Access server named CAS-8 instead. You need to identify which anti-spam feature will NOT be available on CAS-8. Which anti-spam feature should you identify?
A. Connection Filtering
B. Sender Filtering
C. Content Filtering
D. Recipient Filtering
Answer: A
Explanation:
EDGE1 is an exchange server 2010. CAS-8 would be an exchange server 2013. Typically, you would enable the anti-spam agents on a mailbox server if your organization doesn’t have an Edge Transport server, or doesn’t do any prior anti-spam filtering before accepting incoming messages. Connection Filtering agent is only available on the Edge Transport server role. Exchange 2013 does not have an Edge Transport server role yet. The Connection Filter agent and the Attachment Filter agent are only available on an Edge Transport server. Connection Filtering on Edge Transport Servers: Exchange 2013 Help.
Anti-spam agents on Legacy Edge Transport servers.
If your organization has an Exchange 2007 or Exchange 2010 Edge Transport server installed in the perimeter network, all of the anti-spam agents that are available on a Mailbox server are installed and enabled by default on the Edge Transport server. However, the following anti-spam agents are only available on an Edge Transport server. Connection Filtering agent Connection filtering inspects the IP address of the remote server that’s trying to send messages to determine what action, if any, to take on an inbound message. The remote IP address is available to the Connection Filtering agent as a byproduct of the underlying TCP/IP connection that’s required for the SMTP session. Connection filtering uses a variety of IP Block lists, IP Allow lists, as well as IP Block List provider services or IP Allow List provider services to determine whether the connection from the specific IP should be blocked or allowed in the organization. For more information about connection filtering in Exchange 2010:
http://technet.microsoft.com/library/bb124320(v=exchg.141).aspx
Attachment Filter agent.
Attachment filtering filters messages based on attachment file name, file name extension, or file MIME content type. You can configure attachment filtering to block a message and its attachment, to strip the attachment and allow the message to pass through, or to silently delete the message and its attachment. For more information about attachment filtering in Exchange 2010:
http://technet.microsoft.com/library/bb124399(v=exchg.141).aspx
What’s Discontinued in Exchange 2013.
http://technet.microsoft.com/en-us/library/jj619283(v=exchg.150).aspx
Feature.
Anti-spam agent management in the EMC.
In Exchange 2010, when you enabled the anti-spam agents on the Hub Transport server, you could manage the anti-spam agents in the Exchange Management Console (EMC). In Exchange 2013, when you enable the anti-spam agents in the Transport service on a Mailbox server, you can’t manage the agents in the Exchange admin center (EAC). You can only use the Exchange Management Shell. For information about how to enable the anti-spam agents on a Mailbox server, see Enable Anti-Spam Functionality on a Mailbox Server.
Connection Filtering agent on Hub Transport servers.
In Exchange 2010, when you enabled the anti-spam agents on a Hub Transport server, the Attachment Filter agent was the only anti-spam agent that wasn’t available. In Exchange 2013, when you enable the antispam agents in the Transport service on a Mailbox server, the Attachment Filter agent and the Connection Filtering agent aren’t available. The Connection Filtering agent provides IP Allow List and IP Block List capabilities. For information about how to enable the anti-spam agents on a Mailbox server, see Enable Anti-Spam Functionality on a Mailbox Server.
Note:
You can’t enable the anti-spam agents on an Exchange 2013 Client Access server. Therefore, the only way to get the Connection Filtering agent is to install an Exchange 2010 or Exchange 2007 Edge Transport server in the perimeter network. For more information, see Use an Edge Transport Server in Exchange 2013.
Sender Filter agent
Sender filtering compares the sender on the MAIL FROM: SMTP command to an administrator-defined list of senders or sender domains who are prohibited from sending messages to the organization to determine what action, if any, to take on an inbound message.
Content Filter agent
Content filtering assesses the contents of a message. Spam quarantine is a feature of the Content Filter agent that reduces the risk of losing legitimate messages that are incorrectly classified as spam. Spam quarantine provides a temporary storage location for messages that are identified as spam and that shouldn’t be delivered to a user mailbox inside the organization.
Recipient Filter agent
Recipient filtering compares the message recipients on the RCPT TO: SMTP command to an administrator defined Recipient Block list. If a match is found, the message isn’t permitted to enter the organization. You can’t enable the anti-spam agents on an Exchange 2013 Client Access server. Therefore, the only way to get the Connection Filtering agent is to install an Exchange 2010 or Exchange 2007 Edge Transport server in the perimeter network Connection Filtering agent is only available on the Edge Transport server role. Exchange 2013 does not have an Edge Transport server role yet.
NOT BCD
Only need to identify 1 and this is connection filtering.
QUESTION 59
You need to recommend which task is required to prepare Active Directory for the planned Exchange Server 2013 implementation. What should you recommend?
A. On any domain controller in the Paris office, run setup.exe /preparead.
B. On any domain controller in the Amsterdam office, run setup.exe /preparead.
C. On any domain controller in the Paris office, run setup.exe /preparealldomains.
D. On any domain controller in the Amsterdam office, run setup.exe /preparedomain.
Answer: B
Explanation:
B
The schema master is in the Amsterdam office. Before you install the release to manufacturing (RTM) version of Microsoft Exchange Server 2013 or later cumulative updates (CU) on any servers in your organization, you must prepare Active Directory and domains. Run setup.exe /preparead on the schema master.
NOT AC
The schema master is in the Amsterdam office. Run setup.exe /preparead on the schema master.
NOT D
Fabrikam has a single domain. In order to prepare a domain, run the following command from an elevated command prompt after browsing to the Exchange 2013 DVD/ISO:
Setup.exe /PrepareDomain /IAcceptExchangeServerLicenseTerms
If you have a single domain environment, you don’t have to prepare the domain as the local domain is prepared for 2013 as part of preparing the AD. But, if you have a multi-domain environment, all other domains (except the one on which the AD was prepared) has to be ready for 2013. You can prepare all the domains in one go by running the command below:
Setup.exe /PrepareAllDomains /IAcceptExchangeServerLicenseTerms (you will need Enterprise Admin rights).
QUESTION 60
Drag and Drop Question
You need to recommend to a solution to deploy the Outlook app. Which three actions should you recommend performing in sequence?

Get the newest PassLeader 70-341 VCE dumps here: http://www.passleader.com/70-341.html (261 Q&As Dumps –> 272 Q&As Dumps)
And, DOWNLOAD the newest PassLeader 70-341 PDF dumps from Cloud Storage for free: https://drive.google.com/open?id=0B-ob6L_QjGLpfjZ2U1ZfVEZvU0ZreTJkNG1xdmxjS0xUYkdHWVMxWFNRVDhOYTlyRzBjOXM